VoIP theft of service
Fraudulent activity across VoIP networks is increasing, and will continue to be a major problem for service providers in the coming years. However, with proper planning and maintenance, as well as the proper monitoring tools, this threat can be successfully managed.
Introduction to VoIP theft of service
The truth is you just aren’t a phone company until you’ve had a run-in with telecom fraud. VoIP fraud is a significant and growing problem in the telecommunications industry. Because fraudsters often attack during weekends, fraud events often go undetected for many hours. A single fraud event can easily cost a company between three and fifty thousand dollars. In many cases, this number can be even larger.
This is a problem that is only increasing. According to the CFCA report, phone fraud is growing at a rate of 29% per year. As the popularity of VoIP continues to grow, the problem of VoIP fraud will become an increasing threat to the industry.
Understanding the threat is the first step in preventing fraud. The more an organization learns about the many ways that criminals can compromise a vulnerable network, the easier it will be to put measure in place to prevent criminal access.
Meet our expert: Ryan Delgrosso
At TransNexus, we want to help our customers prepare their best defense against the VoIP security threats. For help, we turned to an expert in enterprise communications security, Ryan Delgrosso, former CTO of Phone Power and Broadvoice. He has over a decade of direct experience designing and building distributed, carrier-grade voice networks and solving hard problems such as fraud, network transformation and network function virtualization.
The anatomy of International Revenue Sharing Fraud
International Revenue Sharing Fraud (IRSF) is, without a doubt, both the most damaging and the most prevalent VoIP fraud scenario. Revenue share fraudulent activities are those which abuse carrier interconnect agreements. The fraudster partners with a local carrier that charges high rates for call termination and agreement to share revenue for any traffic generated by the fraudster. Common destinations for these calls include West African countries, UK mobile numbers, and satellite phones.
IRSF is characterized by large amounts of calls, often with long duration, to a single destination. While it is not difficult to detect IRSF by examining Call Detail Records (CDRs), by the time you collect the CDRs, the damage has been done.
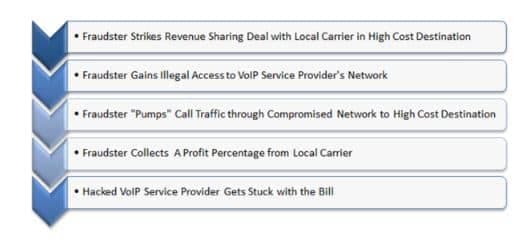
“IRSF is the most common form of fraud we see,” said Ryan Delgrosso, CTO of Phone Power. “The international carrier that delivers the last mile is obligated for paying the final destination telco. They charge the carrier that sent them the call, and the cost flows downhill until you get to the access point that was compromised. Further complicating matters, these schemes always cross international boundaries making pursuing it from a criminal perspective almost impossible. Access or retail service providers usually end up eating the costs.”
Common International Revenue Sharing Fraud scenarios
The first step for a potential VoIP fraudster is gaining illegal access to your network. As with any large network, it is nearly impossible to protect every access point to a VoIP network. This is especially true for retail service providers whose customers access the service provider’s network over the Internet using a wide range of different access devices.
Residential or small business customers access the service provider network using analog telephone adaptors (ATAs) that may be easily compromised. Larger enterprises may access the service provider’s network via a SIP trunk connected to a Private Branch eXchange (PBX) which aggregates traffic from hundreds of SIP phones. Many of the SIP phones may be on the public Internet and completely removed from any security precautions that could be enforced the enterprise or service provider. In addition, lax PBX security precautions can make PBX hacking a simple task.
Following are several examples that illustrate how fraud techniques have progressed from hacks over the telephone network using dial tones, to hacks of the web interfaces of PBXs to more sophisticated hacks of customer premise equipment on the internet.
Voicemail hacking
Voicemail hacking was an early form of communications fraud. It can happen simply and easily through the telephone network. It is a problem rampant enough that even the FCC has recently issued guidelines on how to avoid becoming a victim.
Here, a hacker need only find a device with an easy to break password. Some voice mail systems have static or easily guessed default passwords, and users often do not change the default. Recent studies have shown that the password 1-2-3-4 constitutes nearly 5% of Voice Mail passwords – 7x the frequency of the next most common password (0-0-0-0).
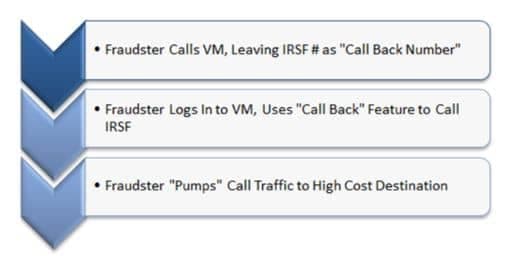
Criminals can easily use this straightforward technique for International Revenue Sharing Fraud (IRSF). Once they have the password to an account, it is a simple matter in many Voice Mail systems to exploit the “Call Back” feature – that feature that allows a user to immediately return a missed call. The criminal calls the phone number, leaving their IRSF number as the “call back” number. Then, they login to the account, find their missed call, and return it, signaling the Voice Mail to initiate a call to their IRSF number. Once the call is connected, a criminal can attempt to leave it up as long as possible, often hours or days.
Call forwarding hack
The call forwarding hack is a more sophisticated form of VoIP fraud. In this case, fraudsters are hacking through the user access web portal of an enterprise PBX. By guessing a user’s password, they can login to a PBX, and configure call forwarding to an expensive long distance destination to profit from IRSF. Then the hacker will call the telephone number of the hacked account which forwards the call for IRSF.
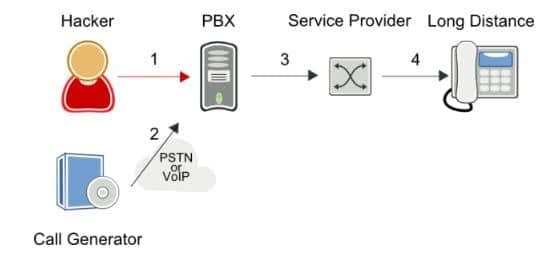
- Hacker accesses the web interface of the PBX and configures call forwarding to international long distance destination
- Hacker calls the compromised number over either the PSTN or VoIP.
- Hacked PBX forwards the call to the service provider’s softswitch.
- The service provider switch forwards the call to the IRSF destination.
Buffer overflow ATA attack
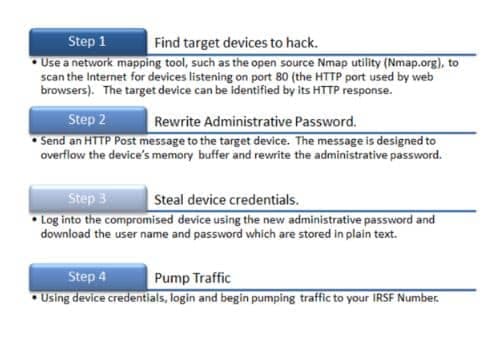
Certain Analog Telephone Adapters (ATAs) with web interfaces are notoriously vulnerable to attack. VoIP fraud expert, Ryan Delgrosso , from Phone Power, describes credential theft from customer premise devices, such as ATAs or SIP phones, as a potential worst case scenario.
“If you blow this up to a global scale, all across the industry, there is a really big dollar figure attached,” said Delgrosso. Buffer overflow vulnerabilities occur when an ATA has a web login screen, something Delgrosso describes as “exceptionally common.”
Customers use their ATA as router with a public IP address so the service provider’s technical support can access the device when needed. In this case, the vulnerable device is an ATA from a vendor with very high market share, so the potential for widespread fraud is huge.
Adding to the mess, Delgrosso adds that one attack signature he has seen with this scenario is that hackers will delete the configuration URLs from compromised devices. This prevents the administrative password from being updated again. The device will continue to function, leaving the compromised customer completely unaware of the attack, but the device will stop talking to the carrier’s configuration server. When (and if) the security breach is discovered, a carrier cannot make a global change that is pushed out to all devices at once. Rather, the service provider must contact each individual device owner to perform a factory reset.
“Once we discovered this particular vulnerability, we were able to get ahead of it pretty quickly,” said Delgrosso. “We know of another company that found thousands of compromised accounts. We have since shared our findings with many other carriers, and have validated that this is happening across the industry, on a global scale. For many carriers, this can be a nightmare scenario.”
In scenarios like this it is important to note that the carriers have an urgent vested interest in detecting and securing devices that show these kinds of vulnerabilities, and often times a response to threats of this type cannot wait for the hardware vendor to write a patch, and in many cases they do not want to announce the vulnerability or the patch for PR reasons.
Blind call transfers
Blind call transfers are a sophisticated technique for doubling International Revenue Sharing Fraud while making the fraud more difficult to detect. See the chart below for a detailed explanation.
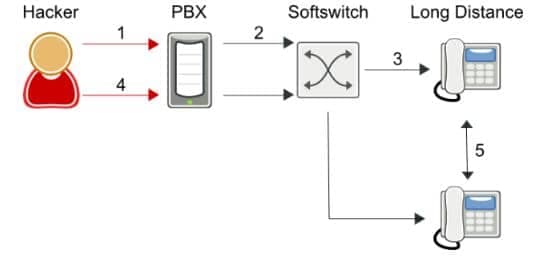
- Hacker phone service hacks unsuspecting PBX to make a call to make international calls
- PBX sends SIP INVITE to service provider’s soft switch
- Softswitch routes call to international number for IRSF
- Hacker instructs PBX to blind transfer call to another international number for IRSF
- The hacker hangs up. The call between the two international destinations remains in place.
This is double IRSF with one phone call.
“We saw a lot of these happening several years ago,” said Delgrosso. “Once the calls are transferred, they stay up until the carrier shuts it down. We’ve seen calls stay up for over 24 hours. On many platforms transferred calls don’t count against concurrent calls, and most switches won’t cut a call record until the call is over. If the criminal is clever, he will transfer dozens or hundreds of calls concurrently. They are pinned in the network, and can go unnoticed until it is too late.”
Wholesale trunking
Fraudulent wholesale trunking is a relatively new phenomenon, but one that is growing in popularity and difficult to detect. In this scenario, the fraudster is actually making money by selling wholesale trunking services, using stolen credentials to terminate the calls.
The key calling signature for this type of fraud is a huge number of apparently random calls. The destinations are not particularly high cost, but neither are they cheap. Countries like Vietnam, Laos, and other middle-priced Asian countries show up often. The traffic often appears to be to residential numbers.
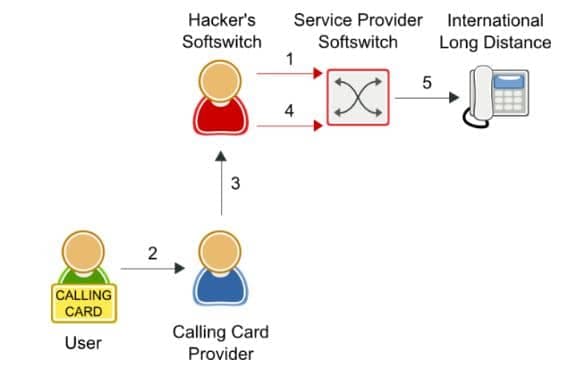
- Hacker’s softswitch registers with service provider’s softswitch using stolen user name and password
- Calling card user places a call
- Calling card provider routes call to lowest advertised route (hacker)
- Hacker sends INVITE to service provider’s softswitch
- Softswitch routes call to international long distance destination
Delgrosso explains that he has traced this type of fraudulent traffic coming from prepaid calling card companies operating a VoIP platform in an offshore colocation facility. Prepaid calling services are well suited to exploit this type of fraud since there are no calling numbers linked to customers. The IP address of the prepaid calling platform is the only link to trace the fraudster.
Unfortunately, geolocation cannot always be used to identify the fraudster. These services can be offered via a tunnel through the internet that hides the true IP address of the fraudster. The public IP address of the fraudster’s calling platform could be the IP address of a hosted Virtual Private Network (VPN) service, while the actual prepaid calling platform is located in a different part of the world.
The future of VoIP theft of service
Delgrosso believes that the rapid growth of VoIP related fraud techniques is creating its own eco-system. His observations lead him to believe that some hackers specialize in stealing network access credentials. This is their specialty, not VoIP fraud. He theorizes that a black market exists for selling telecom credentials, and many hackers simply sell stolen credentials to as many criminals as possible.
For this reason, service providers may see call signatures from a variety of types of VoIP fraud. A single account, once compromised, can be sold over and over again to any criminal who wishes to perpetuate IRSF or start a fraudulent wholesale trunking company.
Preventing VoIP theft of service
Secure your network
The first layer of defense against VoIP Theft of Service is to secure your network. It may seem simple, but ensuring that your network passwords are strong can be one of the best ways to avoid security threats.
We recommend increasing your networks password strength requirements, and well as improving your default password strength. For maximum protection, passwords should not be sequential or repeated numbers, or your own extension. To limit the impact of any compromised passwords, disable voice portal dialing.
Unfortunately, for many carriers, it is difficult, if not impossible, to control customer password choices. This is especially true in SIP trunking scenarios, where there carrier may have no control over the types of devices and passwords used behind the PBX. The less direct control a carrier has over their network endpoints and devices, the greater the risk.
Telecom fraud detection software
Though a secure network can help to prevent fraud, attacks are almost inevitable today. Constantly changing technologies and savvy criminals ensure that there is always a new way to hack into a network. It is absolutely essential to have some sort of fraud detection software in place, to catch instances of fraud before it hits your bottom line.
It is not enough to analyze CDRs for evidence of fraud. By the time calls are completed, or cut off by the carrier, the damage has been done, and tens of thousands of dollars lost. Instead, effective fraud detection software will look at call routing requests. This allows alarms to go off before the calls are set up, and before you find 300 calls to the Ivory Coast that have been connected for 48 hours.
TransNexus has developed a number of solutions to detect and prevent fraud in VoIP networks. TransNexus solutions integrate fraud detection with an already world class least cost routing (LCR) platform. TransNexus software can block fraudulent calls before they are routed, including calls that have been transferred from their original source.
More on TransNexus.com
February 15, 2023
Suggestions to curb access arbitrage
June 27, 2022
FCC proposes new rules to prevent access stimulation
June 6, 2022
Denial of service attack and ransom demand defeated
May 18, 2022
China cracks down on telecom fraud
December 6, 2021
Telecom fraud losses increasing, according to CFCA report
December 1, 2020
FCC Report and Order on one-ring scam calls
November 9, 2020
Domestic telecom toll fraud is still a problem
October 12, 2020
FCC changes rules for intercarrier compensation on toll free calls
January 23, 2020
TRACED Act calls for one-ring scam protection
November 19, 2019
Robocall and TDoS case studies
October 28, 2019
FCC denies stay request on their Access Arbitrage Order
October 28, 2019
Wangiri telecom fraud activity reported in Canada
September 26, 2019
FCC issues order to prevent access stimulation
July 16, 2019
ClearIP adds new call forwarding blacklist capabilities
July 10, 2019
July holiday week telecom fraud attack profiles
June 13, 2019
ClearIP enhancements for blacklisting of SPID and location
May 20, 2019
Anatomy of a telecom fraud attack
May 14, 2019
Study on rule changes to eliminate access arbitrage
May 8, 2019
FCC warns of Wangiri telecom fraud scams
March 8, 2019
SIP Analytics vs. CDR-based fraud management – a case study
October 22, 2018
FCC proposal to curb domestic telecom fraud
September 27, 2018