STIR/SHAKEN
TransNexus STIR/SHAKEN solutions enable you to authenticate and digitally sign calls you originate and verify signed calls you receive. These are complete turnkey solutions that include everything you need to deploy STIR/SHAKEN quickly and easily.
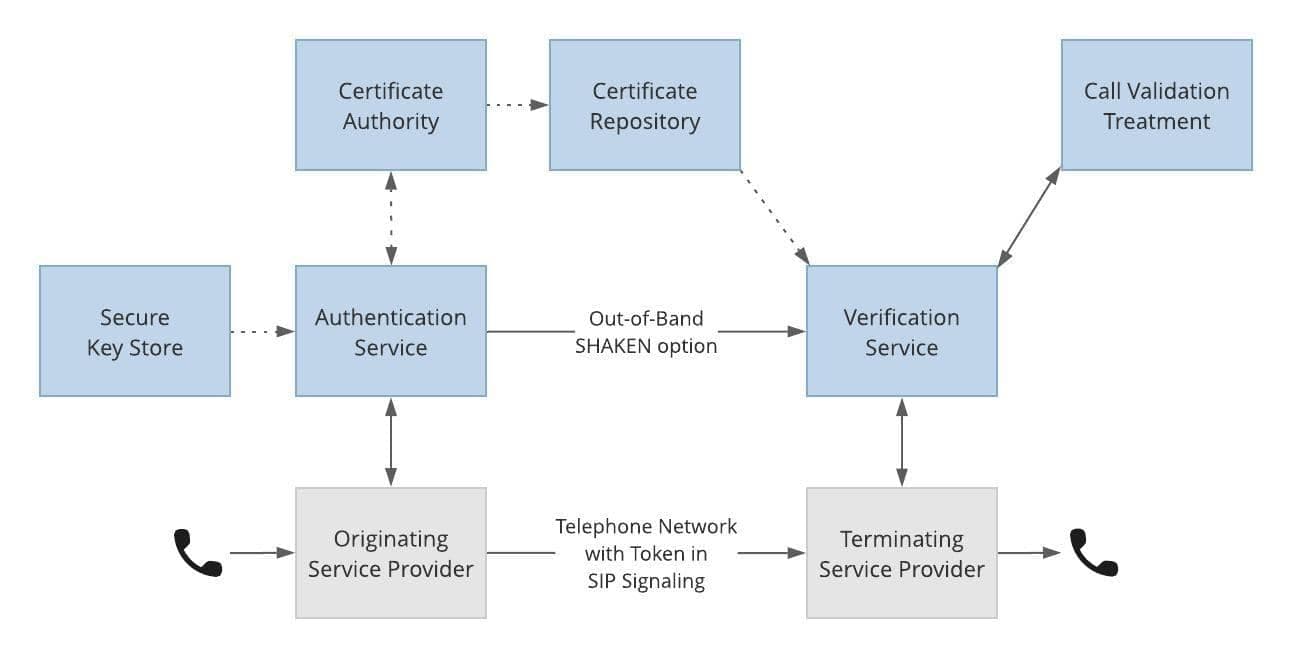
TransNexus STIR/SHAKEN solutions Provide Everything You Need
The Authentication Service uses policies you control to create digitally signed PASSporTs for calls you originate.
- The Secure Key Store securely manages keys used to sign calls.
- TransNexus is an approved Certificate Authority. We provide certificates and host them in a Certificate Repository for you.
The Verification Service checks signed calls you receive and terminate.
- Call Validation Treatment uses policies you control to manage calls based upon verification status and call analytics.
TransNexus STIR/SHAKEN solutions are compliant with ATIS and IETF standards.

“We still have a lot of TDM traffic. We started ClearIP STIR/SHAKEN with our Ribbon switchboard. We have zero cost in it. It works very well. We’re TRACED Act compliant today.”
— Dave Frigen, COO, Wabash Communications

The TransNexus difference
Here’s what sets our STIR/SHAKEN solutions apart:
- Most affordable commercial STIR/SHAKEN software solutions available
- Many happy customers using them in production networks
- Works with your existing network

“Our customers can now see incoming calls verified with a special signature or certificate, letting them know they can trust what they see on their caller ID.”
— Joe White, CTO, Brightlink
- Fully standards-based per ATIS-1000074, ATIS-1000080, ATIS-1000084 and others
- One of the first to complete testing with the ATIS Robocalling Testbed to confirm proper use of the standards
- Market leader for new STIR/SHAKEN capabilities, including:
- Out-of-Band SHAKEN
- Rich Call Data
- Support for a Centralized SHAKEN Server using an HTTP-based RESTful API

“We’re running version 9.3 on our Metaswitch. We have a lot of TDM traffic. It was a simple process to get ClearIP STIR/SHAKEN up and running.”
— John Smith, COO, Blue Valley Tele-Communications
Our customers tell us that our SHAKEN solutions are the most flexible, easiest to deploy, and best value for the money that they found.

“We are seeing some calls with a ‘[V]’ in front of the caller name. It surprised some of our customers. Once we explained what it means, that the caller ID was verified for that call, they were excited.”
— Rob Good, IT Director, Rhode Island Telephone
Let us show you
Contact us today to learn how we make your STIR/SHAKEN deployment quick, easy, and affordable.
TransNexus has a comprehensive suite of robocall mitigation solutions to prevent the origination of unlawful robocalls.
Learn more about robocall mitigation