Introduction to VoIP fraud
VoIP devices are the primary tools used by fraudsters. Studies have shown that 46% of fraudulent calls were made from VoIP phones.
Voice over Internet protocol (VoIP) services transmit telephone calls over high-speed Internet connections rather than over traditional land-based telephone lines. They do not usually travel directly from a caller to a recipient’s computer but rather through computers belonging to several layers of intermediary VoIP service providers, or wholesalers.
VoIP is about convergence, saving money and resources. However, these types of systems also create more inroads for attack. As VoIP has become more accessible and popular, security threats have grown as well. The most prevalent threats to today’s VoIP deployments are rooted in traditional data networking and PSTN attacks.
What constitutes VoIP fraud?
For the purposes of this whitepaper, we will consider VoIP fraud to be the use of a VoIP telecommunications network with the intention of avoiding payment. In that sense, the payment may be incorrect, entirely lacking, or the attempt to force another party to pay. We will consider both illegal activities and those activities which, though technically legal, may still hurt telecommunications companies by taking advantage of systems and vulnerabilities.
Whom does VoIP fraud affect?
VoIP fraud can affect any organization which uses or sells VoIP services. In most cases, the fraud target is an enterprise. Most enterprises never realize that they have been hacked, refuse to pay the fraudulent charges and threaten to switch to a different service provider. The SIP service provider has little leverage over its international long distance vendors and is left to cover the bill.
However, in some cases, service providers will demand the enterprise pay for fraudulent charges. This was the case in a 2009 when Michael Smith, a small business owner in Massachusetts, found that someone had hacked into his PBX to make $900,000 worth of calls to Somalia. AT&T attempted to sue Smith for $1.15 million to recoup the cost of the calls and interest.
Though AT&T eventually dropped the charges, a spokeswoman for the company maintained that they had been entitled by law to collect the amounts owed, and that Smith should have put more safeguards in place to protect his phone system.
VoIP fraud can and does occur in any industry. Certain industries, such as banking, tend to attract more fraud than others. A recent study from Pindrop Security found that nine out of the top ten banks, and 34 of the top 50 banks had been victims of call fraud.
Where does VoIP fraud come from?
VoIP fraud comes from all over the globe. Traditionally, Africa has been a “Hot Continent” from telecom fraud, because the termination costs are very high and regulation is not as stringent as in other parts of the world.
However, a 2011 study from the Communications Fraud Control Association (CFCA) found that the top 5 countries from which fraud originates are the United States, India, the United Kingdom, Pakistan, and the Philippines. The top five fraud terminating countries were Cuba, Somalia, Sierra Leone, Zimbabwe, and Latvia.
How big of a problem is VoIP fraud?
VoIP fraud is a significant and growing problem in the telecommunications industry. Because fraudsters often attack during weekends, fraud events often go undetected for many hours. A single fraud event can easily cost a company between three and fifty thousand dollars. In many cases, this number can be even larger.
A 2009 attack on an Australian company’s VoIP PBX resulted in 11,000 international calls in just 46 hours, leaving the SIP provider with a bill in excess of $120,000.5 A 2011 weekend episode in South Africa resulted in a bill of over $12,000 and another in the US cost victims more than $1.4 million.
Experts have trouble estimating an aggregated global yearly loss, because calculations are often based on subjective and individual standards. However, most experts agree that total loss is somewhere between 3 and 10 percent of income. This translates to total global losses of somewhere between 30 and 50 billion dollars per year.7
The CFCA’s 2011 report put the number at $40.1 billion dollars lost. This is a problem that is only increasing. According to the CFCA report, phone fraud is growing at a rate of 29% per year. As the popularity of VoIP continues to grow, the problem of VoIP fraud will become an increasing threat to the industry.
Types of fraud
In our exploration of VoIP fraud, we explain the numerous flavors of fraudulent activities. Fraudsters have come up with a myriad of techniques for exploiting the VoIP industry. Some are stolen from traditional phone fraud tactics, others from computer hacking techniques, and still others exploit VoIP specific equipment and software. These are just a few examples of the many types of VoIP fraud and fraudsters are constantly coming up with new ways to attack. In addition, most fraudsters will use some sort of combination of the techniques listed below.
Arbitrage
Arbitrage is simply the exploitation of the differences in settlement rates between countries, the complexity of services and rates, and the multi-operator environment of VoIP. For example, if country A has much lower settlement rates with country B than with country C, it might be cheaper for country C to send its traffic for country A via country B. One of the first larger arbitrage routes was for traffic between Australia and the US, which was cheaper if sent via New Zealand and Canada.
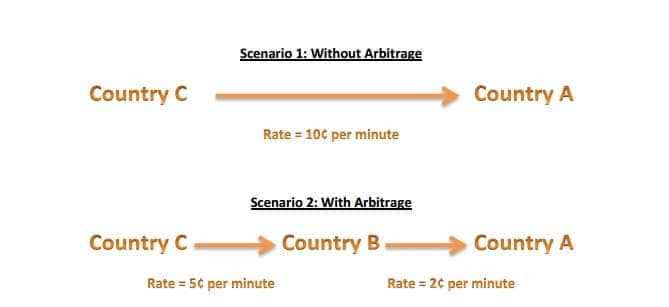
This is an example of a type of fraud that falls into a legal gray area. Though it may seem relatively tame, arbitrage can create problems for telecom companies. Unscrupulous providers may artificially inflate traffic where arbitrage is profitable. Telcos often withhold payments to Service Providers if this type of activity is suspected.
Buffer overflow
Some VoIP fraud relies on methods typically used for computer fraud. In this case, fraudsters use buffer overflow errors in handling INVITE or SIP (Session Initiation Protocol) packets. The flaw might be used to crash applications or run arbitrary code. This is an issue that has was a particular problem for Asterisk users in the past, but has since been remedied.
Bypass fraud
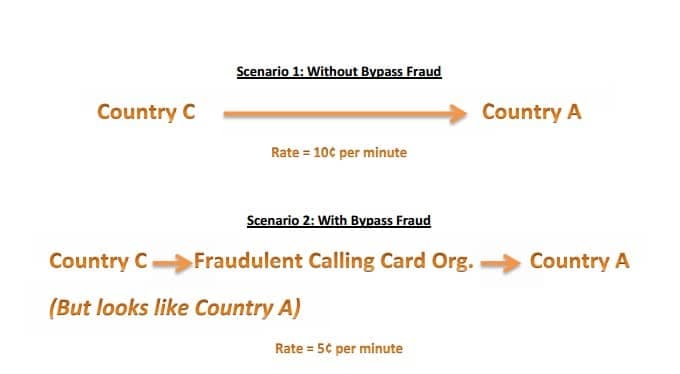
Bypass fraud is the unauthorized insertion of traffic onto another carrier’s network. You may also find this type of fraud referred to as Interconnect fraud, GSM Gateway fraud, or SIM Boxing. This scenario requires that the fraudsters have access to advanced technology, which is capable of making international calls appear to be cheaper, domestic calls, effectively bypassing the normal payment system for international calling.
The fraudsters will typically sell long distance calling cards overseas. When customers call the number on the cards, operators are able to switch the call to make it seem like a domestic call.
Call transfer fraud
One type of fraud that has been a particular issue for softswitch users is call transfer fraud. In this scenario, the fraudster hacks into a PBX and uses that PBX’s services to make free long distance calls. By instructing the compromised PBX to transfer the call to the hacker’s own phone service, subscribers to the fraudster’s phone service can speak to their international destinations through the hacked soft switch, and the soft switch operator cannot bill the hacker’s subscriber.
Those familiar with three-way calling will recognize the inspiration for this type of fraud. See the chart below for a detailed explanation.
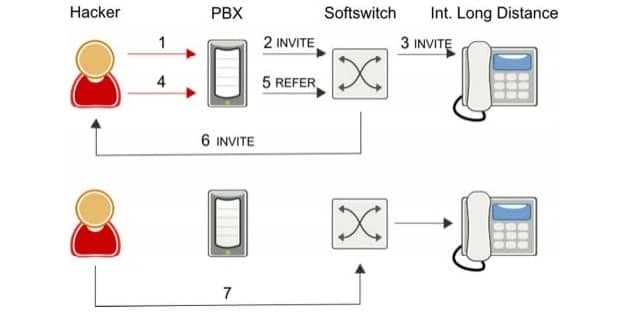
- Hacker phone service hacks unsuspecting PBX to make a call to make international calls
- PBX sends SIP INVITE to soft switch
- Softswitch routes call to international carrier
- Hacker instructs PBX to blind transfer call to Hacker Phone Service
- PBX sends SIP REFER to soft switch to blind transfer call to Hacker Phone Service
- Softswitch sends SIP INVITE to Hacker Phone Service
- Hacker’s Subscriber speaks to international destination through soft switch.
Most soft switches have no way of tracking a call once it is transferred out of the network, so fraudsters can generate a significant amount of traffic and revenue for themselves before being caught.
Domestic and International Revenue Share Fraud
Revenue share fraudulent activities are those which abuse carrier interconnect agreements. Cooperation is the key to this type of fraud. The fraudster’s goal is to pair up with a destination that can charge high rates, and then inflate traffic to his numbers at little or no cost to himself. These types of schemes can occur within a country, or across international borders. Though they may not be technically illegal, they are often also paired with PBX hacking or other forms of fraud that generate illegal and artificial traffic.
Fraud rings in the Philippines and other developing countries have been known to have human “labor pools” that perform password guessing and make manual calls originating from hacked PBXs. Sometimes the “labor pool” can even be generated by scams on social media, SPAM mail, or post cards that advertise free vacations or important information just by calling a phone number.
Traffic pumping or switch access stimulation
Because of telephone regulations, long distance carriers must pay access fees to local exchange carriers for calls to those carriers’ local subscribers. Rural carriers may charge substantially higher access fees than urban carriers.
In order to increase their incoming call volume and revenue, some rural carriers partner with telephone service providers to route their calls through the rural carrier. These often include phone sex or free conference call providers, who expect a high volume of incoming calls. A similar scenario occurs internationally, with fraudsters making setting up conference servers in third world countries and making deals with the local (often state owned) telephone company.
To qualify as access stimulation, a fraudster must:
- Have a revenue share agreement between the terminating carrier that stimulates demand
- Have a 3-to-1 increase in interstate terminating to originating traffic or 100% traffic growth in a month year over year.
In this case, authorities can step in and force the terminating carrier to re-file their access tariff with the public utilities commission within 45 days. Because of the extra traffic, the terminating carrier would no longer be eligible for the high access fee, and will likely be dropped from the revenue sharing agreement.
CNAM revenue pumping or dip pumping
Every call to a U.S. telephone number that has Caller ID (CID) enabled requires that the terminating phone company perform a lookup in one of several national databases that contain all the U.S. subscriber names and numbers. This database lookup is called a CNAM dip. When this database is being dipped, the originating local phone company gets compensated by the terminating phone company—this is commonly referred to as a CNAM dip fee (or simply a dip fee). This compensation happens for every call where the calling party name is displayed to the called party, even if the call is not answered.
CNAM Revenue Pumping, or DIP Pumping is similar to regular traffic pumping. The fraudsters again, partner with the parties who typically receive CNAM revenue, and generate traffic to conference servers with those numbers, sharing the revenue created. This traffic is generated wither by high volume call services (such as free conference calls and phone sex services) or by hacking into vulnerable PBX systems.
Premium rate services
Premium-rate telephone numbers are telephone numbers for telephone calls during which certain services are provided, and for which prices higher than normal are charged. Unlike a normal call, part of the call charge is paid to the service provider, thus enabling businesses to be funded via the calls. Like the other revenue sharing schemes, fraudsters will pair up with a premium rate service to generate traffic to the number, via legal or illegal methods.
False answer supervision
When a dialed phone number is not in service, the calling party will hear a brief recording telling them so. There is no answer supervision or connection between the calling and called party. Since the call never connects, it is an incomplete call and should not be billed.
However, fraudsters use false answer supervision to make these calls appear as completed calls which may be billed. Perhaps the fraudster has published rates for terminating calls without any intention of actually completing the calls.
Here, service providers will route calls through the fraudster, who, instead of terminating the call, will play a not-in-service message and then bill the service provider for more than 10 seconds of calling. This type of fraud hurts the originating service provider by costing money and hurting their reputation. The key indicators of this type of fraud are:
- Short phone calls
- Calling party hangs up nearly 100% of the time
- High answer seizure ratio
Location Routing Number (LRN) fraud
Location Number Fraud or LRN fraud works based on the desire of some service providers to avoid extra charges from LRN dips. Most providers will run an LRN dip to determine the correct LRN for a dialed number. However, many service providers will not perform an LRN dip if the LRN is already in the SIP message.
Fraudsters take advantage of this by inserting fake LRNs into their calls. For example, they may insert the LRN for a relatively cheap terminating destination, when the call is actually going to a high cost rural destination. The service provider will then bill the fraudster for the cheaper call, but will have to eat the cost of the expensive rural call. In some cases, this can be up to 5x the price they billed the fraudster.
PBX hacking
One of the most typical and certainly one of the most insidious flavors or VoIP fraud involves hacking into a Private Branch Exchange (PBX). Fraudsters who can exploit the vulnerabilities of the IP PBX are able to generate a significant amount of traffic. PBX hacking is the common technique used to perpetrate the Domestic and International Revenue Share Fraud and Call Transfer Fraud schemes listed above.
PBXs can be compromised in-band (over the phone circuit) by someone guessing the numeric pin on an extension or by finding an extension with a default pin. There are four common configuration mistakes in VoIP security architecture that can increase the risk of PBX hacking:
- Weak user authentication and access control
- Relying solely on Session Border Controllers (SBCs) to provide security
- Inadequate virtual LAN separation and control
- Inadequate use of encryption
Phreaking
Phreaking is simply unauthorized access and control of a phone. Phreaked PBXs may be networked together to create a fraudulent telecom network for providing services. Customers of phreaked services often include call shops, call centers, calls sold through the internet, and traffic pumping schemes.
Roaming fraud
Roaming fraud is the use of a wireless operator’s services outside of the user’s home country, where there is no intention of paying for calls made. Typically, this type of fraud is committed by someone who is also using subscription fraud (obtaining a service subscription using a false identity). Because of the delay in the transference of call detail records between roaming partners, it can take days or even weeks for the home network to receive the call records and notice the fraud.
SIPVicious
Though its name suggests otherwise, the SIPVicious program is a mainstream auditing too for VoIP systems. Unfortunately, fraudsters have also found a way to use it for attacks. The attacks are apparently aimed at taking control of VoIP servers to place unauthorized calls.
The attacks use a known Trojan, jqs.exe, and connect to command and control servers to receive instructions on downloading instructions as well as the SIPVicious tool from a .cc domain. After installation, SIPVicious is run and scans for SIP devices on the compromised computer’s network and launches brute force attacks to guess the administrative password on those systems.
This creates a base from which attackers can make VoIP calls from the victim’s phone or VoIP infrastructure. Those calls might be used to rack up charges on premium rate numbers controlled by the attackers, or as part of voice phishing (vishing) scams that target unwitting consumers.
Shell companies
Recent VoIP scams have involved the creation of shell companies. These companies have no operations, and their sole purpose is to induce companies that sell VoIP services to extend service on credit to the shell companies. When the victim providers sell VoIP services to the shell companies on credit, the conspirators “bust out” the accounts by causing the companies to use substantially more VoIP services than the companies had been approved to buy in such a short period of time.
Fraudsters typically do this over weekends and holidays so that the providers do not notice. When the invoices for the services came due, the fraudsters send fake wire transfer confirmations via e-mail or submit small payments to keep the victim providers from cutting off service.
Subscription fraud
Subscription fraud is simple the use of service with no intent to pay. Often this type of fraud is associated with other crimes, such as identity theft. The true impact of subscription fraud often goes unrecognized because providers mistake it for bad debt. The key difference between the two is intention.
Fraudsters gain access to a service in one of three ways:
- Giving valid details, but disappearing without paying the bill
- Using false details
- Using the identity of another person (identity theft)
Once recognized as a ‘bona fide’ customer, fraudsters then have access to a network and are able to carry out revenue generating schemes that can seriously damage reputation and bottom-line profits.
Toll fraud
Toll fraud is a scheme where fraudsters break into a company’s VoIP network and sell long distance minutes. Fraudsters hack companies’ PBXs, and then control the hacked PBXs to make long distance calls. To make money, the fraudsters will sell long distance calls, and then use the hacked PBXs to complete the calls.
Unallocated number fraud
Some fraudsters simply add unallocated phone numbers to their rate deck. They can then simulate traffic to this number, which will generally be routed to the fraudulent company, as they are the only ones that will “terminate” the call, based on the rate decks. According to recent estimates, 32% of called numbers used for fraud are unallocated numbers.
Techniques for fighting VoIP fraud
The most prevalent threats to VoIP deployments today are rooted in hacking of the underlying and supporting infrastructure. The major IP PBX vendors can be secured, but security has to be considered during deployments. It’s important to consider your existing network security before adding VoIP components. A VoIP security assessment and penetration test will help identify vulnerabilities.
Analyzing Call Detail Records
The simplest way of tacking VoIP fraud is by analyzing Call Detail Records (CDRs). VoIP providers should put into place a system that detects the most common symptoms of fraud and PBX hacking, traffic spikes, unusual call patterns, etc. These systems work best when they are reported in near real time. In addition, there must be a system for monitoring this analysis, especially overnight, on weekends, and over holidays. The best analysis solutions will include alerts or will be integrated with your routing system to temporarily block suspicious calls.
Call blocking
Some providers are taking an even more aggressive stance against fraud and completely blocking destination countries with reportedly high incidences of fraud, or simply blocking calls to fraud related phone numbers. Obviously, this method risks denying legitimate traffic, and can also become a timeconsuming project, keeping up with the latest news on countries and numbers that have been reported.
Call routing
Other service providers have chosen to route fraud countries only through operators who perform a validation on the call before completing it. Though this method may cut down on fraud, it is also time consuming and not cost effective.
Legal action
Though it is tempting to rely on legal action as a solution to VoIP fraud, it is not the ideal option. Recent studies have shown that companies choose not to report fraud cases to law enforcement due to a perceived lack of interest and understand from authorities. Though 89.1% of communications companies refer at least one case to law enforcement per year, few fraudsters are ultimately caught and punished.
That being said, there have been recent arrests over VoIP fraud. In May 2012, two men who stole more than $4.4 million from VoIP providers were sentenced to three years in prison and will be required to pay back the millions of dollars. In another recent case in Australia, fraudsters were sentenced to 40 years in federal prison and owe $18 million in restitution.
Session Border Controllers
Session Border Controllers, which work in front of an IP connected PBX can be a deterrent to fraud. The SBC can detect and stop attempts to guess user credentials or unauthorized attempts to route traffic. Some SBCs can analyze call patters and dynamically learn your normal traffic patterns, sending warnings when something deviates from the norm. Session Border Controller cannot, however, detect Traffic pumping attacks
TransNexus VoIP fraud detection solutions
TransNexus has developed a number of solutions to detect fraud in VoIP networks. NexOSS, in addition to its already industry-leading least cost routing features, effectively eliminates the problem of traffic pumping fraud for VoIP providers.
The solution is to include smart monitoring features that sense when there is an unusual spike in call traffic to a specific destination. When a suspicious spike occurs, the NexOSS system simply and automatically puts a temporary block on the route, ensuring that fraud losses are kept to an absolute minimum without interrupting legitimate calls.
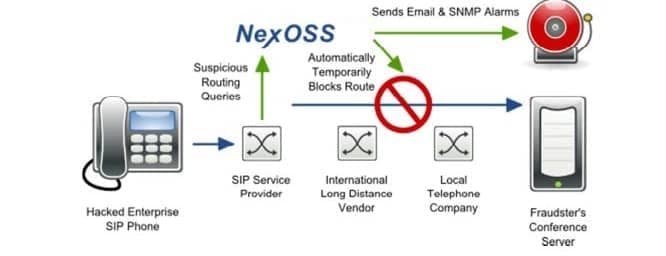
TransNexus solutions analyze CDRs or RADIUS records, and can identify fraud by IP address, or by group or user id. TransNexus has partnered with top industry leaders to ensure that the solutions operate smoothly with any network.
Summary
VoIP fraud is, and will remain, a lucrative criminal business. As VoIP continues to grow in popularity, schemes for beating the system will continue to become more complex and powerful. VoIP providers and enterprises must work together to ensure their networks are secure from every angle. By securing networks and analyzing traffic for signs of fraud, VoIP providers can minimize their fraud risks.
More on TransNexus.com
February 15, 2023
Suggestions to curb access arbitrage
June 27, 2022
FCC proposes new rules to prevent access stimulation
June 6, 2022
Denial of service attack and ransom demand defeated
May 18, 2022
China cracks down on telecom fraud
December 6, 2021
Telecom fraud losses increasing, according to CFCA report
December 1, 2020
FCC Report and Order on one-ring scam calls
November 9, 2020
Domestic telecom toll fraud is still a problem
October 12, 2020
FCC changes rules for intercarrier compensation on toll free calls
January 23, 2020
TRACED Act calls for one-ring scam protection
November 19, 2019
Robocall and TDoS case studies
October 28, 2019
FCC denies stay request on their Access Arbitrage Order
October 28, 2019
Wangiri telecom fraud activity reported in Canada
September 26, 2019
FCC issues order to prevent access stimulation
July 16, 2019
ClearIP adds new call forwarding blacklist capabilities
July 10, 2019
July holiday week telecom fraud attack profiles
June 13, 2019
ClearIP enhancements for blacklisting of SPID and location
May 20, 2019
Anatomy of a telecom fraud attack
May 14, 2019
Study on rule changes to eliminate access arbitrage
May 8, 2019
FCC warns of Wangiri telecom fraud scams
March 8, 2019
SIP Analytics vs. CDR-based fraud management – a case study
October 22, 2018
FCC proposal to curb domestic telecom fraud
September 27, 2018