Prevent telecom fraud with blacklist call forwarding
Call-forwarding fraud is a common telecom fraud attack. This blog post explains how ClearIP blacklisting can be used to easily prevent call-forwarding telecom fraud.
What is call-forwarding telecom fraud?
In this attack, a fraudster gains access to a user account within an enterprise PBX or web portal, often when the user account has an easy-to-guess password—sometimes a default password configured in the PBX. (Safety tip: insist that users always reset their telephone account passwords!)
Once fraudsters gain access to a user account, they configure call forwarding on that number to an expensive long-distance destination, such as premium rate numbers they’ve set up for telecom fraud. Then the fraudster will call the telephone number of the hacked account, which then forwards the call to the expensive destination.
This telecom fraud attack can be caught by telecom fraud prevention systems that monitor call traffic and block calls once a threshold has been reached.
But some organizations and subscribers do not expect to forward any calls to high-cost countries. Wouldn’t it be nice if they could block such calls immediately, without waiting for their fraud prevention system to detect a fraud attack underway?
That’s what ClearIP Blacklist Forwarded Calls can do.
ClearIP Blacklist Forwarded Calls
This feature is a standard service in ClearIP. It’s quick-and-easy to set up, and it stops call forwarding telecom fraud attacks dead in their tracks.
Here is an example of a call forwarding blacklist policy:
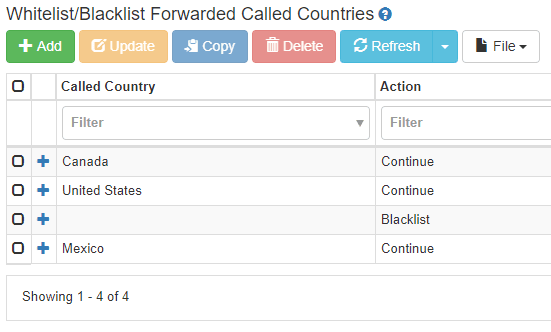
In this example, call forwarding is allowed to telephone numbers in Canada, Mexico, and the U.S. Call forwarding to numbers in any other country is blacklisted. Presto! In just a few seconds, this telecom fraud attack vector has been closed.
But you know how it goes: as soon as you set up a policy, someone will have a valid exception. Our sales rep, Bob, said he will be on a business trip to Saint Helena next week and will need to forward his calls to the Government Press Office there. Now what?
Simple: just set up an exception that allows such call forwarding. Here is an example of a pinhole set up to allow call forwarding:
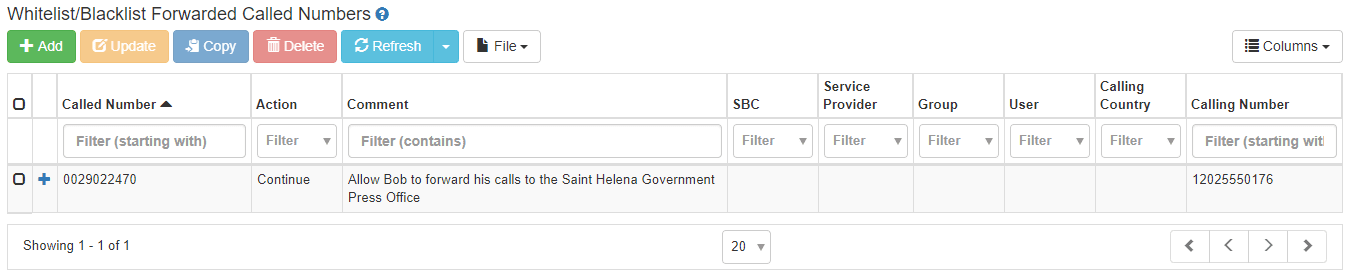
This pinhole is very specific and precise. It only allows calls to be forwarded to a specific called number, the Saint Helena Government Press Office at 0029022470. Further, it only allows such calls to be forwarded for a specific telephone number, Bob’s number, at 12025550176.
Pinholes do not have to be that specific. ClearIP is very flexible, and it allows exception policies to be as precise or as broad as you need. For example, you could allow a specific number to forward all calls to Saint Helena or calls to any number to be forwarded to the Saint Helena Government Press Office. Policies can be tailored to match other call groups.
It’s important to highlight a few things about these policy settings:
- They only apply to forwarded calls. Subscribers can still make calls to other countries directly. ClearIP has separate blacklist and fraud prevention settings to control those calls.
- Calls forwarded to Canada, Mexico, the U.S., and Bob's calls forwarded to Saint Helena, aren’t whitelisted. The action is set to Continue, which means ClearIP will still perform normal fraud prevention and other services on those calls.
Stop call-forwarding telecom fraud attacks today with ClearIP. Contact us for more information and to arrange a trial.
More on TransNexus.com
October 22, 2018
FCC proposal to curb domestic telecom fraud
October 11, 2018
Google Voice call screening as robocall prevention
September 27, 2018
Robocaller hit with large fine
September 27, 2018
ClearIP delivers the fastest, easiest, most-precise prevention of toll fraud, robocalls and TDoS attacks. It’s ready-to-go with STIR/SHAKEN.
Learn more about ClearIP