NexOSS Centralized SHAKEN Server
The NexOSS software platform can be used as a SHAKEN Centralized Signing and Signature Validation Server as described in ATIS-1000082. This capability offers a simple SHAKEN solution for complex telecommunications networks.
Features
The NexOSS Centralized SHAKEN Server includes the following features:
- STI-KMS — Key Management System for managing multiple SHAKEN certificates
- STI-AS — Authentication Service
- STI-VS — Verification Service
- Interface — RESTful API that communicates via HTTP per ATIS-1000082
- Authentication signing with multiple SHAKEN certificates
- Rich Call Data
- Provides excellent monitoring, detection and reporting for robocall mitigation
- Unlimited horizontal scalability
Benefits
Some voice service providers using a complex, heterogeneous network might be interested in deploying SHAKEN as a centralized service. The NexOSS Centralized SHAKEN Server makes this easy:
- Fast, easy deployment for complex networks
- The fastest way to comply with the TRACED Act
- Simple network integration
- The SHAKEN HTTP API is lightweight and requires no network configuration changes
- Supports multiple customers, each with their own SHAKEN certificate
- Horizontal scalability supports networks of any size
- Plug-and-play interoperability with any network equipment:
- Ribbon PSX
- Metaswitch Perimeta
- Oracle Acme Packet
- And any other system that supports ATIS-1000082.
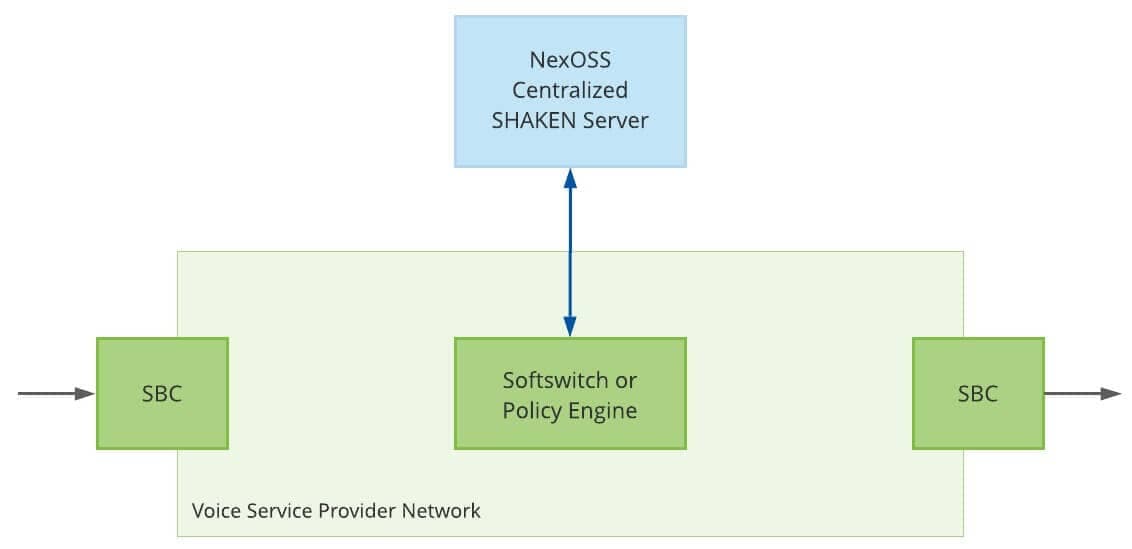
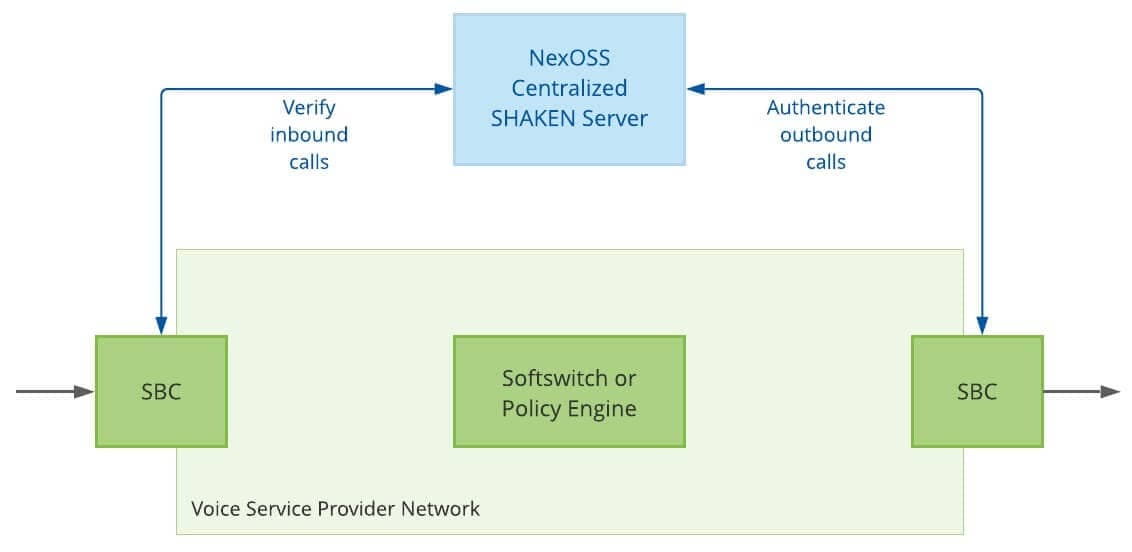
Deployment options
The NexOSS Centralized SHAKEN Server can be integrated with a softswitch or policy engine at the center of a network or with Session Border Controllers (SBCs) at the network edge.
Centralized deployment
Deployed at the network edge
Host server requirements
- Any virtual or bare metal host server running Red Hat or CentOS 7
- RAM 8–16 GB depending on configuration
- Host server sizing guidelines per CPU core and 1 GHz clock speed (50% CPU utilization):
- Authentication: 55 calls per second signed, PASSporT created
- For example, a host server with four 3 GHz cores running at 50% CPU utilization would authenticate and sign 660 calls per second (55 × 4 × 3 = 660).
- Verification: 37 calls per second, PASSporT verified
- For example, a host server with four 3 GHz cores running at 50% CPU utilization would verify 444 calls per second (37 × 4 × 3 = 444).
- Authentication: 55 calls per second signed, PASSporT created
- Minimal disk requirements
The TransNexus difference
TransNexus STIR/SHAKEN solutions are uniquely positioned to give you the best performance and value available:
- Fully standards-based
- One of the first to complete testing with the ATIS Robocalling Testbed to confirm proper use of the standards
- Most affordable commercial STIR/SHAKEN software solution available
- Many happy customers using them in production networks
- Works with existing network equipment
We make SHAKEN deployment easy:
- Registering with the STI-PA
- Testing with a free trial
- SHAKEN certificates and Certificate Repository
- Go-live support
- Assistance with your robocall mitigation program and FCC certification filing preparation as required by the FCC Second Report and Order
Contact us today to learn more.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy