Lessons learned from call forwarding attacks
A new ClearIP customer enabled call forward blacklisting. They experienced a telecom fraud call forwarding attack over the weekend. Here’s what happened:
- After hacking into a few customer accounts and setting up unconditional call forwarding, the fraudster launched 1,700 call attempts to 17 different high-cost countries within the North American numbering plan.
- None were successful. Not a single one.
- Legitimate calls, including domestic forwarded calls, were not blocked.
- Based on the termination rates of the destination countries in this attack and a modest estimate of likely call duration, the ClearIP system has already paid for itself for a long time.
Call forwarding telecom fraud prevention
Call forwarding telecom fraud is a common attack profile. Telecom service providers, and their customers, are vulnerable to this attack primarily because many customers like to use simple, easy-to-guess passwords on their customer portal accounts. Hackers run software programs that try to guess simple passwords. Sometimes they find one.
There are two very simple ways to completely block this attack:
Encourage customers to change their password or PIN to a complex password not easily guessed by hackers. This helps, but it only takes one subscriber with an easy-to-crack password to open the door to fraudsters.
Use call forward blacklisting, a flexible, highly-effective fraud prevention method available in ClearIP.
A call forwarding attack case study
Last week, a new ClearIP customer began using call forward blacklisting. Call forwarding telecom fraud had been a problem for their customers in the past. This telecom service provider had reluctantly removed the feature from their customer web portal. Encouraged by the call forwarding blacklist capability in ClearIP, they decided to offer call forwarding again, which some customers wanted.
Over the weekend, hackers broke into several customer accounts on the web portal. Weak passwords again. The carrier had not done anything wrong. They had even decreased the number of failed login attempts allowed before locking the account to thwart hackers.
Once the fraudster gained access to a few accounts, he launched a call forwarding fraud attack, including 1,700 call attempts with unconditional forwarding to 17 high-cost destination countries within the North American numbering plan. (Most softswitches do not classify such calls as international.) But because call forward blacklisting was in place, not one fraudulent call was forwarded. And because blacklists are checked at the beginning of SIP Analytics, ClearIP didn’t process any more services on these calls.
Here is a list of call forwarding attempts made:
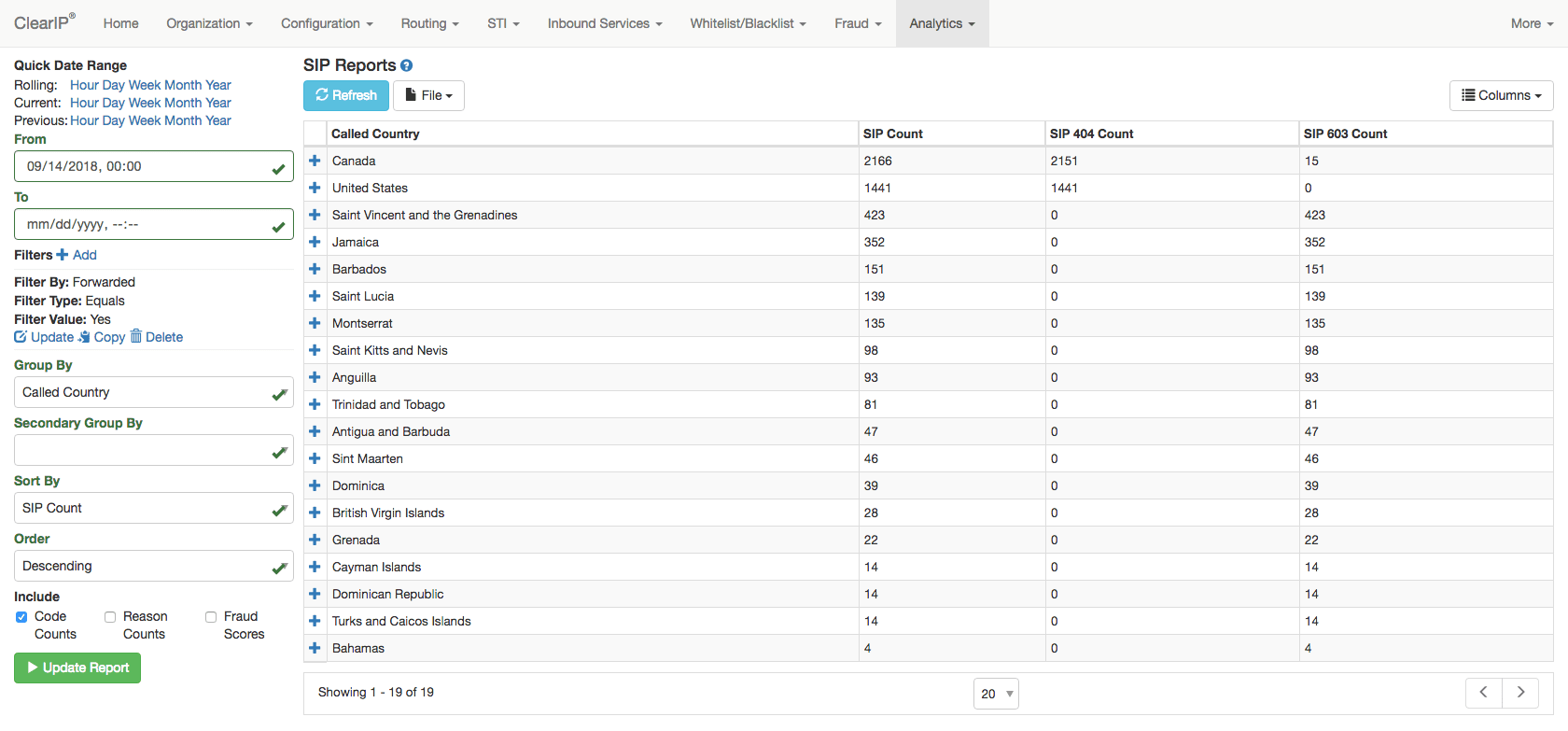
Most all calls forwarded to numbers in Canada and the U.S. were legitimate. The call forwarding attempts to the other countries were from the call forwarding attack.
Outcomes
None of their customers were victims of fraudulent call forwarding. None of their legitimate calls were disrupted. Fraud losses were zero.
Contact us today to learn how to quickly and easily eliminate telecom fraud attacks from your network.
More on TransNexus.com
October 22, 2018
FCC proposal to curb domestic telecom fraud
October 11, 2018
Google Voice call screening as robocall prevention
September 27, 2018
Robocaller hit with large fine
September 10, 2018
