SIP Analytics—The fastest, most precise fraud prevention
It always happens at the worst time. On a holiday weekend. When you are enjoying time with your family, or on a date, or in the middle of the night when you are dead asleep. You get an alert; a fraud attack is in progress.
One of your company’s most important customers has been hacked. Their PBX is generating a constant flow of calls to high cost domestic and international destinations. Your network is hemorrhaging thousands of dollars every hour, possibly more. Blocking legitimate calls from your customer is not an option. The fraud source must be identified quickly with no mistakes. It is a stressful time for fraud analysts and Network Operations Center (NOC) technicians.
According to the Communications Fraud Control Association, telecom fraud attacks cost billions each year. Fraud events costing over $100,000 are not unusual. In addition to the financial losses, fraud events take a heavy toll on customer relationships and employee morale.
Fortunately, SIP Analytics can make fraud attacks a nonevent. Fraud losses can be reduced to negligible amounts and legitimate calls will never be blocked. No more worries about weekend fraud emergencies that disrupt service for customers and the lives of telecom staff. In addition, SIP Analytics will also protect your subscribers from unwanted robocalls and Telephony Denial of Service (TDoS) attacks.
SIP Analytics® — A better technique: faster, simpler, more effective
Traditional Fraud Management Systems (FMSs) analyze Call Detail Records (CDRs) to identify fraudulent calls. The analysis works, but it is too slow. Hundreds of fraudulent calls can be in progress before the first CDR is collected for analysis. As a result, a CDR-based FMS, working exactly as advertised, will allow fraud leakage costing hundreds or thousands of dollars each month. In addition, a CDR-based FMS cannot be easily integrated with network switches to automatically block calls. A fraud alert from a CDR-based FMS usually requires human action to initiate call blocking in the network.
Fraud Management Systems that passively monitor network packets are an improvement over CDR based fraud systems since they can identify the start of a fraud attack before CDRs are created. However, network monitoring fraud systems have two major drawbacks. First, they are expensive because they require data mirroring and deployment of multiple probes in the network. Second, they cannot be easily integrated with network switches to automatically block calls. A fraud alert from a network-monitoring-based FMS usually requires human action to initiate call blocking in the network.
SIP Analytics is different because the TransNexus software is just another SIP end point in your network—like a SIP phone or a SIP trunk. Integration is simple, and automated call blocking and call diversion are enabled natively—no special switch or Session Border Controller (SBC) configuration is required.
How it works
SIP Analytics is a powerful analytics engine with a SIP interface. The SIP Analytics engine ignores all SIP messages except for INVITEs. Each time a SIP INVITE message is received, SIP Analytics determines the call source from either the source IP address, trunk group, CustomerId or calling number. SIP Analytics then determines the fraud risk for the call based on the called number. By comparing the current risk profile of calls from the call source compared to the risk profile at the same time of week for the previous twelve weeks, SIP Analytics can determine if the call is fraudulent.
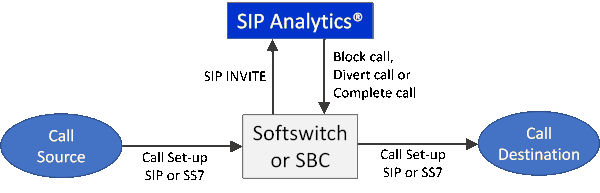
The following diagram illustrates how SIP Analytics is integrated with either a softswitch or Session Border Controller (SBC). A softswitch receives a call setup with either SIP or SS7 signaling. If the call should be analyzed for fraud, the softswitch will route the call out a SIP trunk to SIP Analytics. This simple SIP integration is an important feature. It gives the softswitch operator full control of what calls receive fraud analysis. High risk calls are routed to SIP Analytics and low risk calls are not. Resources are not wasted analyzing low risk calls.
SIP Analytics architecture
SIP Analytics monitors SIP traffic to detect the following three potential fraud risks:
- Total calls: SIP Analytics detects traffic pumping and theft of service risks by monitoring the call rate and the riskiness of the called number for every call source.
- Forwarded calls: Unconditional call forwarding is a common and potent toll fraud hack. For fast and accurate detection of call forwarding attacks, SIP Analytics monitors the fraud risk of calls forwarded by each call source.
- Transferred calls: Call transfers can be the most dangerous fraud attack. The hacker calls a high-cost destination, adds a third caller (using call transfer) at another high cost destination and then hangs up, leaving two very expensive call legs in progress through the victim’s switch. The fraudster then repeats the process creating hundreds of simultaneous calls from a single compromised phone line. SIP Analytics monitors all call transfers from each call source to quickly detect and stop these attacks.
Based on the fraud analysis, SIP Analytics will respond with one of the following SIP messages:
- 503 Service Unavailable — this message indicates no fraud was detected and that the switch should route advance to the next outbound trunk group to complete the call.
- 603 Decline — this message indicates fraud was detected and the standard behavior for any SIP device will be to return the 603 Decline message to the call source and block the call.
- 300 Redirect — This message indicates that fraud has been detected and the call should be diverted to a safe destination, such as voice mail, a honey pot or a CAPTCHA gateway.
SIP Analytics provides telephone service providers with two important benefits:
- Fraud is detected at the beginning of an attack.
- The SIP integration enables automated call blocking or diversion, which stops fraud losses immediately and reduces the workload on fraud analysts and switch operators.
Design options for integrating SIP Analytics into a network are very flexible. The common deployment designs are listed below:
- SIP Analytics is integrated with access SBCs to block fraudulent calls before they enter the service provider’s network.
- SIP Analytics is integrated with the softswitch to enable fraud control for traffic that originates from either SIP or ISUP signaling. This design also enables fraud control by SubscriberId.
- SIP Analytics is integrated with the egress SBC to block fraudulent calls from leaving the network.
SIP Analytics is a natural complement to Least Cost Routing (LCR) and SHAKEN Authentication. Most TransNexus customers combine LCR, SIP Analytics fraud control and SHAKEN Authentication services in a single SIP query. Combining these three functions in a single transaction improves network efficiency and reduces post dial delay.

Self-learning fraud control
Fraudsters are always changing their tactics. Large networks, with many customers, are too complicated for fraud analysts to manage. Machine learning is the only practical way to recognize fraudulent calls quickly. SIP Analytics learns the fraud profile of every call from every call source (IP address, trunk group, customerId and calling number) by time of week and stores that information for twelve weeks. The following chart shows actual data from a TransNexus customer.
SIP Analytics is self-learning
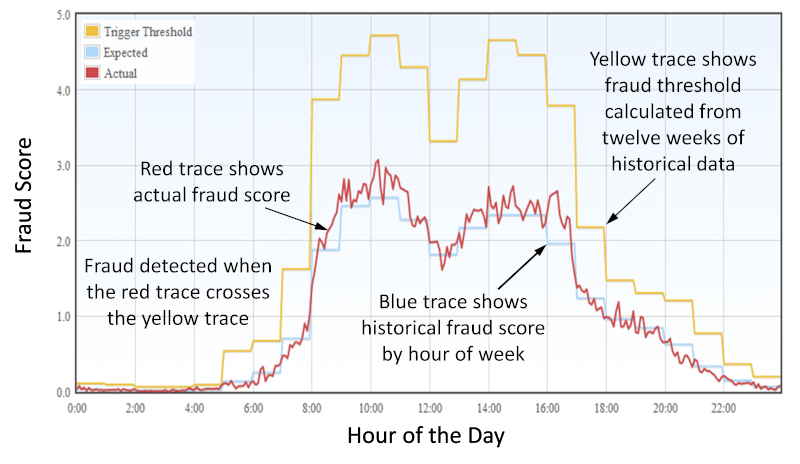
The red trace shows the actual fraud score recorded in five-minute increments by hour of the day. The blue trace shows the average fraud scores by hour of the day. The yellow trace shows the fraud trigger threshold calculated by SIP Analytics based on historical data. If the actual fraud score ever exceeds the fraud trigger threshold, the trigger will be activated, sending alerts, and taking action to block or divert calls based on pre-defined policies.
Targeted call blocking
When a fraud attack occurs, one of the unique benefits of SIP Analytics is targeted call blocking. Since fraud is detected by specific call sources, only fraudulent calls from the compromised calling number or subscriber account will be blocked or diverted. In addition, when a call source is hacked, only the fraudulent destinations are blocked. For example, assume a subscriber’s phone has been hacked and it being used to generate hundreds of calls per hour to Cuba. SIP Analytics will only block calls from the hacked subscriber’s account to Cuba. The hacked subscriber will be able to make calls as usual to all other countries and have no idea their account has been hacked until they learn from their service provider running SIP Analytics.
Case study: SIP Analytics versus conventional fraud detection
This success story comes from a TransNexus customer who was evaluating SIP Analytics compared to their existing FMS, which analyzed CDRs to detect fraud. This event provides hard data on the benefits of faster detection and automated call blocking enabled by SIP Analytics.
On a Sunday afternoon, a fraudster used a customer’s hacked PBX to place fraudulent calls to various high-cost international destinations. It was a classic International Revenue Share Fraud (IRSF) attack. The fraudster swiftly placed 228 calls distributed across 120 different called numbers within 31 different countries. The fraud attack is summarized below.
| Destination | Call Attempts | Fraud Losses |
|---|---|---|
| Madagascar | 92 | 1,048.98 |
| Macedonia | 29 | 185.60 |
| Montenegro | 22 | 161.48 |
| Maldives | 12 | 165.58 |
| Moldova | 11 | 52.29 |
| Cuba | 9 | 104.40 |
| Algeria | 6 | 69.00 |
| Tunisia | 5 | 67.87 |
| Other Countries | 42 | 278.38 |
| Total | 228 | $2,133.58 |
When the CDR-based FMS detected the fraud attack, it alerted the Network Operations Center (NOC). The NOC shut down the fraud attack after 228 fraudulent calls had completed over 56 minutes. The CDR-based FMS allowed fraud losses of $2,133.58.
SIP Analytics detected the fraud attack on the fifth call, 1 minute and 15 seconds into the attack. Unfortunately, the customer had not yet configured SIP Analytics to block fraud attacks; the software was still in report-only mode. Had blocking been enabled, fraud losses would have been only $2.03, or 0.1% of the actual losses. Relying on the CDR-based FMS cost the provider $2,131.55. After this event, the service provider activated the automated call blocking feature of SIP Analytics. The results were lower fraud losses and less staff time devoted to managing fraud events.
CAPTCHA — Legitimate calls are never blocked
After financial losses, blocking legitimate calls because of false positive fraud detection is the second greatest worry for fraud analytics. Minimizing fraud losses and false positives is a stressful balancing act. Stricter fraud controls cause more false positives. Less restrictive fraud controls reduce false positives but increase fraud losses. It seems impossible to minimize both fraud losses and false positives.
Unless, however, SIP Analytics is combined with the TransNexus CAPTCHA gateway. This combination enables very tight fraud controls to minimize losses and ensures that legitimate calls will never be blocked. When fraud is detected, SIP Analytics will return a SIP 300 redirect to the softswitch that diverts the call to a CAPTCHA gateway. In early media, the CAPTCHA plays a greeting requesting the caller to enter a random two-digit code. If the caller enters the code, the call is completed. A machine-generated call cannot enter the code, and so the call will be blocked. This simple mechanism ensures that your fraud detection levels can be very restrictive and that your customer’s calls will never be blocked by a false positive fraud detection.
A CAPTCHA gateway is a standard SIP end point. Integrating distributed CAPTCHA gateways into a SIP network is simple. If a call is valid, the CAPTCHA gateway will return a SIP 503 Service Unavailable response to the softswitch, which will automatically route advance to the next route in its local routing table to complete the call. If the call is machine generated, the CAPTCHA gateway will return a SIP 603 Decline message, and the softswitch will block the call.
Stop robocalls and Wangiri fraud
The techniques described for controlling outbound toll fraud also work exceptionally well for stopping Wangiri fraud, also known as one ring and cut fraud. SIP Analytics does more than just measure the inbound call rate from a calling number. It also assesses the fraud risk of the calling number for faster and more accurate Wangiri fraud control.
In addition to traffic pattern analysis and blacklisting tools (described below), SIP Analytics uses powerful calling number reputation analytics, drawing data from a variety of sources, including over 500,000 honey pots and SHAKEN verification to identify robocalls.
Using the rich analysis from different tools, SIP Analytics enables service providers with three options for handling robocalls on a per subscriber basis:
- Block the call
- Divert the call to a CAPTCHA gateway or voice mail
- Replace the CallerID (CNAM) with SPAM
SHAKEN verification
SIP Analytics will verify the digital signature in a SHAKEN PASSporT to determine if the calling number can be trusted. SHAKEN verification has the following six possible outcomes:
- PASSporT is valid with calling number attestation = A (high trust level)
- PASSporT is valid with calling number attestation = B (ID of the call source trunk group is trusted, but trust level for the specific calling number is limited)
- PASSporT is valid with calling number attestation = C (no trust, the calling number or source is accurate)
- PASSport is invalid
- PASSport cannot be validated
- PASSporT is not present
For each of the use cases listed above, policies can be set (by subscriber) in SIP Analytics to block or divert inbound calls. When a calling number is verified with attestation = A, SIP Analytics will add a [V] prefix to the P-Asserted-Id display name (CNAM) to indicate the call is verified. If no display name is present, SIP Analytics can make an external query to obtain the CNAM data. As a pioneer in SHAKEN deployments, TransNexus SIP Analytics is the first tool capable of verifying SHAKEN PASSporT received either inband or Out-of-Band.
Stop Telephony Denial of Service (TDoS) attacks
In most cases, robocalls are annoying. But when robocalls come in volume, they cause a Telephony Denial of Service (TDoS) attack. In a TDoS attack, a flood of inbound telephone calls will consume all the victim’s telephone lines preventing both inbound and outbound calls. In almost all cases, the calling number is randomly spoofed for every call so call blocking by calling number is impossible.
For businesses that rely on inbound calls to generate revenue, a TDoS attack is deadly and can literally destroy a small business in weeks. When the TDoS victim is a critical service, such as law enforcement, fire department or a hospital, the consequences can be life threatening for individuals trying to call those services. Blocking inbound calls is not an option. The CAPTCHA gateway has proven to be a perfect tool for immediately restoring telephone service in the middle of a high volume TDoS attack. CAPTCHA gateways scale horizontally, can be deployed on-premise or in the cloud, and can absorb any size TDoS attack.
SIP Analytics combined with a CAPTCHA gateway is an outstanding tool for protecting service provider customers from TDoS attacks.
Blacklisting, whitelisting, and the Shield database
SIP Analytics includes robust tools for blacklisting and whitelisting combinations of calling and called numbers, diversion numbers (to block forwarded calls), IP addresses and user agents. If you have a blacklisting or whitelisting requirement that is not supported, we will add the feature at no charge.
The Shield database is a TransNexus managed list of high risk calling and called numbers. The data sources for the Shield database include:
- Industry fraud control groups
- TransNexus honey pots
- Analysis of web sites selling premium rate numbers
- Analysis of the LERG and National Numbering plans to identify ranges for reserved, invalid, unallocated and premium rate numbers
- FCC complaint database
- TransNexus customers
Registration and call transfer attacks
An optional add-on feature for SIP Analytics is a SIP message probe which captures SIP registration messages and SIP Refer messages for transferred calls. Registration messages are processed in SIP Analytics to provide real time alerting and analysis of registration attacks. The SIP Refer messages are processed by SIP Analytics to monitor transferred calls.
Why fraud analysts and network operators like SIP Analytics
ClearIP delivers the fastest, easiest, most-precise prevention of toll fraud, robocalls and TDoS attacks. It’s ready-to-go with STIR/SHAKEN.
Learn more about ClearIPIn most large telephone service providers, the fraud team and Network Operations Center (NOC) team are different organizations with different leadership, priorities and work processes. However, traditional fraud control techniques require the fraud and network teams to work together to troubleshoot and stop a fraud attack. Often, this coordination effort is inefficient and aggravating for both the fraud and NOC teams. The NOC team can be annoyed with frequent requests for information and call blocking. The fraud team can be annoyed by being dependent on the NOC team to do their job.
SIP Analytics addresses these organizational issues and enables major efficiencies in fraud operations. Since SIP Analytics is a network element, it gives the fraud team real time visibility into network conditions for trouble shooting. More importantly, it gives the fraud team the ability to manually block or divert calls without assistance from the NOC.
However, years of customer experience have shown that the best practice is to avoid manual blocking in response to a fraud event and let the machine learning of SIP Analytics automate call blocking. When fraud detection is combined with automated call diversion to a CAPTCHA gateway to avoid blocking legitimate calls, the result can be significantly reduced human involvement in fraud control. In most cases, NOC involvement can be eliminated for most fraud events—freeing up NOC staff to work on other priorities. With more restrictive traffic pumping fraud controls and no concerns about blocking legitimate calls, fraud staff can focus their efforts on other fraud risks such as subscriber fraud or SIM box fraud.
SIP Analytics provides not only a reduction in fraud losses, but also a reduction in labor costs. For the fraud and NOC teams, the results are no more fraud emergencies on holiday weekends and late at night.
Customer-friendly licensing for big savings
For most telephone service providers, the fraud risk for 95+% of their calls is almost zero. However, most fraud systems analyze all calls in a network, regardless of the fraud risk. This results in wasting resources on a large system to analyze most calls that are not a fraud risk. The service provider pays for server resources and software licensing that are not needed.
SIP Analytics is different. Service providers using SIP Analytics are in full control of what calls are analyzed by SIP Analytics. The common use case for most U.S. customers is to only route calls to high risk international and domestic (IA, SD and MN) destinations to SIP Analytics. Typically, service providers may only need to analyze about 5% of their total traffic, which offers big savings when compared to pricing for other Fraud Management Systems.
Get started today
Let us show you how easy it can be to get started with SIP Analytics. Sign up for a free consultation and interactive demonstration today.
SIP Analytics® is a registered trademark of TransNexus.
