The evolution of access arbitrage schemes
A discussion is underway to change access arbitrage rules again. Why? Because access arbitrage schemes are evolving, and the rule changes are designed to counter the latest traffic-pumping tactics. Here’s what’s happening.
The access stimulation problem
In the past, some LECs charged exorbitant access fees to terminate calls. Fraudsters would hack into a victim’s telephone system, pump traffic to such LECs and split the proceeds. The scheme funneled money from upstream providers to the access stimulating LEC to the fraudsters. The FCC calls this access arbitrage—others call it traffic pumping.
A solution
In September 2019, the FCC issued a rule change to prevent access stimulation. Here’s what the rule did:
- Made access stimulating LECs cover the cost of incoming traffic.
- Expanded the definition of access stimulation to include providers that have an unusually high ratio of inbound traffic compared to outbound traffic—no explicit revenue sharing agreements required.
- Allowed providers to bypass centralized equal access providers, which are otherwise exempt from some access arbitrage prevention rules.
So, this fixed the problem, yes? Well, not exactly.
New tactics
In a recent ex parte notice filed with the FCC, Inteliquent described an evolution of this traffic pumping scheme. Here are the good-news/bad-news points they made:
- “Multiple rural CLECs previously engaged in access stimulation have exited the business of access stimulation completely.”
- “However, there has been a shift of access stimulated traffic from certain rural CLECs to a small number of IPES providers.“
So, the rule changes worked, but the fraudsters found a way around. How?
The evolution of traffic pumping
The Inteliquent filing describes traffic pumping tactics that put an IPES provider in the mix. Here’s how it works:
- Upon receiving numbering authority, the IPES provider designates in the LERG a local interconnection partner, i.e., the Hosting LEC.
- The IPES provider makes other arrangements for direct connections of inbound and outbound traffic. These arrangements do not go through the Hosting LEC.
Inbound Call Flows for IPES Providers
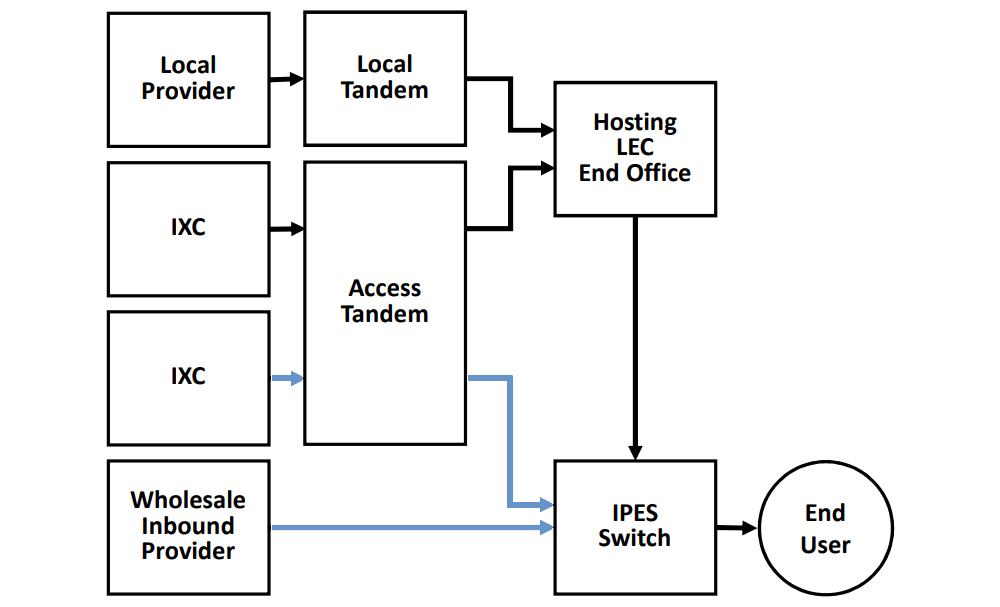
Figure 1. IPES Providers Often Route Most Inbound Calls Direct (Blue Lines). Image credit: Inteliquent
Figure 1 illustrates the inbound call flow. In many cases, most of the IPES provider’s inbound calls are brought directly to their switch and do not go through the Hosting LEC.
Is this a problem? In some cases, it is.
In the FCC’s Further Notice of Proposed Rulemaking on numbering policies and implementation of the TRACED Act, they describe in paragraph 17 their finding that interconnected VoIP providers have been inserted into the call path for the sole purpose of evading access stimulation rules.
New rules proposed
In this FNPRM, the Commission asked whether an applicant for direct access to number resources should be treated as a LEC regarding the access stimulation rules. In the same paragraph, they ask for comment on several other possible rules.
In their ex parte filing, Inteliquent urged the Commission to attribute the calls terminated by the IPES provider to that provider, not to the Hosting LEC.
“Because the IPES provider both functions like a LEC for the purposes of the access stimulation rules and necessarily has visibility into its own access traffic, it is reasonable for the IPES provider to have that access traffic attributed to it.
What would that do? Inteliquent pointed out that the Commission’s access stimulation rules caused many LECs to exit the business of access stimulation. Applying the same rules to IPES providers would have the same result.

TransNexus solutions
TransNexus is a leader in developing innovative software to manage and protect telecommunications networks. The company has over 20 years’ experience in providing telecom software solutions including toll fraud prevention, robocall mitigation and prevention, TDoS prevention, analytics, routing, billing support, STIR/SHAKEN and SHAKEN certificate services.
Contact us today to learn more.
SIP Analytics® inspects each call before it begins. It’s the fastest, most precise method available to detect and prevent telecom toll fraud.
Learn more about SIP Analytics