July 2021 STIR/SHAKEN statistics
We examined SHAKEN call statistics from our ClearIP customers in July. They received signed calls from 181 originating service providers in July, which gives us insight into trends in SHAKEN usage in the first full month of the mandate. Here’s an overview.
Signed robocalls
In July, we observed calls that were (1) identified as robocalls using call analytics and (2) signed by the Originating Service Provider using SHAKEN.
We dug into this further to look for robocall patterns by SHAKEN attestation level. We also compared the proportions of robocalls among signed and unsigned calls. Here’s what we found.
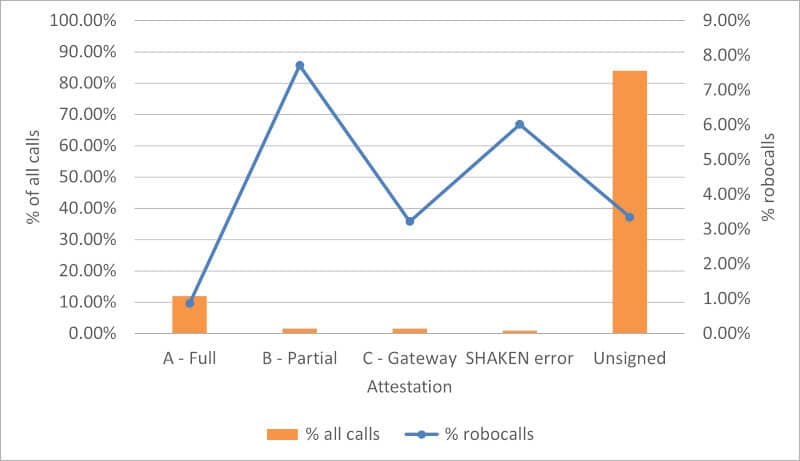
SHAKEN Calls and Robocalls by Attestation Level
The orange bars show the distribution of calls by attestation types, unsigned calls, and signed calls that generated SHAKEN errors. The bars are measured by the percentages on the left side of the graph.
The blue line shows the percentage of calls that were identified as robocalls using call analytics by attestation types, unsigned calls, and signed calls that generated SHAKEN errors. Points on the line are measured by the percentages on the right side of the graph.
- About 83% of calls received were unsigned. About 3.4% of these unsigned calls were robocalls.
- About 12% of calls received were signed with full attestation. Fewer than 1% of these calls were robocalls.
- About 1.5% of calls were signed with gateway attestation. About 3.2% were robocalls—about the same ratio as with unsigned calls.
- About 1.6% of calls received were signed with partial attestation. Here’s the surprising part: almost 8% of these calls were robocalls!
We first noticed this was taking place in mid-July 2021. These numbers show the trend continued for all of July. We dug into the details behind the robocalls with partial attestations, and we found that many were signed by downstream service providers for their upstream service provider customers. This appears to be a weakness in the SHAKEN and robocall mitigation framework:
- Upstream providers are originating robocalls.
- Downstream providers are signing these calls with SHAKEN using a partial attestation.
- The upstream provider certified a Complete SHAKEN implementation in their Robocall Mitigation Database filing. Therefore, they are not required under current FCC rules to do robocall mitigation.
- The downstream provider signing calls is not required to do robocall mitigation either.
- The actors are complying with FCC SHAKEN rules (but not robocall rules).
We expect this situation will draw attention and action from the traceback group and the Commission.
Verification statuses and errors
Signed calls were up, unsigned calls were down, and signed calls that failed verification were up slightly.
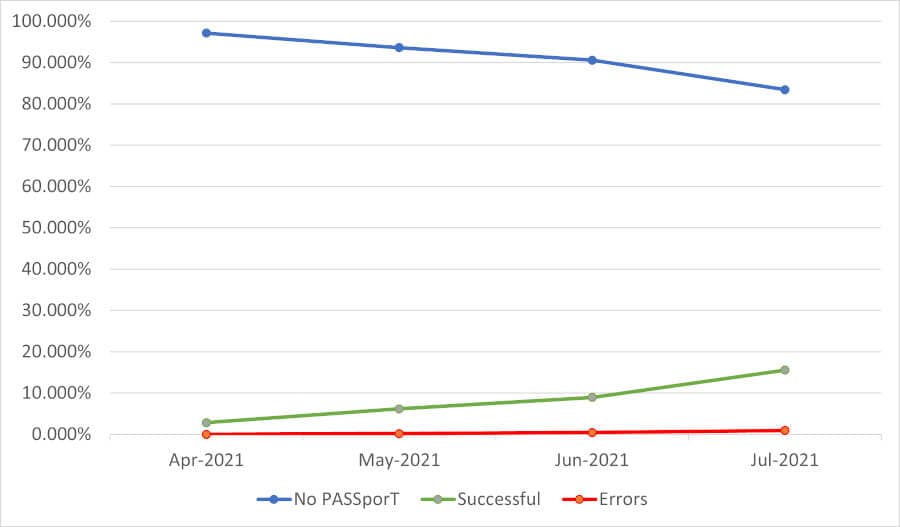
SHAKEN Trends March–June 2021
The following table provides details of SHAKEN errors encountered during verification.
Verification status and errors
| Verification status | Mar–Apr | May | June | July | Trend |
|---|---|---|---|---|---|
| No PASSporT | 97.149131% | 93.624665% | 90.575572% | 83.466339% | ▼ |
| Successful | 2.829892% | 6.195567% | 8.946494% | 15.573173% | ▲ |
| Certificate chain error | 0.013079% | 0.100030% | 0.000103% | 0.098368% | ▲ |
| Called number mismatch | 0.001151% | 0.064497% | 0.393571% | 0.449608% | ▲ |
| Calling number mismatch | 0.003335% | 0.012633% | 0.075460% | 0.390719% | ▲ |
| Invalid info parameter in Identity header | 0.003049% | 0.001455% | 0.002544% | 0.003637% | ▲ |
| Certificate repository error | 0.000280% | 0.000918% | 0.001901% | 0.000110% | ▼ |
| Invalid iat in PASSporT | 0.000052% | 0.000173% | 0.003268% | 0.002647% | ▼ |
| Invalid orig in PASSporT | 0.000033% | 0.000060% | 0.000259% | 0.001915% | ▲ |
| Malformed Identity header | 0.000259% | 0.009633% | ▲ | ||
| Invalid ppt in PASSporT | 0.000259% | 0.000005% | ▼ | ||
| Invalid dest in PASSporT | 0.000259% | 0.000082% | ▼ | ||
| Invalid origid in PASSporT | 0.003605% | ▲ | |||
| Invalid alg in Identity header | 0.000115% | ▲ | |||
| Invalid attest in PASSporT | 0.000027% | ▲ | |||
| 100.000000% | 100.000000% | 100.000000% | 100.000000% |

Originating service providers signing calls
There were more Originating Service Providers (OSPs) signing calls in July than in previous months.
Originating Service Providers signing calls
| Month | SHAKEN OSPs |
|---|---|
| Apr-2021 | 26 |
| May-2021 | 50 |
| Jun-2021 | 131 |
| Jul-2021 | 181 |
Participation continues to grow, with more expected:
- There are 351 authorized service providers listed on the Policy Administrator website as of this publication date.
- As of August 11, 2021, 1,084 U.S. service providers had certified that they have either a partial or complete implementation of SHAKEN in the Robocall Mitigation Database (RMD).
The number of SHAKEN implementations in the RMD might be inflated by service providers that claimed Complete SHAKEN and have a downstream provider signing calls for them. This would explain the sizeable difference between authorized SHAKEN providers and providers that claimed SHAKEN in the Robocall Mitigation Database.
Summary
- Some robocalls are being signed with SHAKEN, especially by downstream providers giving partial attestation.
- The proportion of signed calls is increasing.
- SHAKEN verification errors have increased slightly.
- There are more OSPs signing calls (181). Still a long way to go to match the number of authorized service providers (351) and the number of U.S. providers that certified they’ve implemented SHAKEN (1,084).
- SHAKEN participation can be greatly expanded by leveraging the new SHAKEN standards for non-IP traffic. The more SHAKEN is used, the more effective it will become.
TransNexus solutions
We offer STIR/SHAKEN and robocall mitigation solutions in our ClearIP and NexOSS software platforms. We can make your STIR/SHAKEN deployment a smooth process.
In addition, we help service providers with all aspects of STIR/SHAKEN deployment, including registering with the Policy Administrator and filing their certification with the FCC.
Contact us today to learn more.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy