STIR/SHAKEN statistics for August 2021
We’ve pulled SHAKEN statistics from our ClearIP customers in August. How did this initiative do in the second full month since the mandate went into effect? Let’s have a look.
Signed robocalls by attestation level
The following chart shows the proportion of all calls and robocalls by verification status.
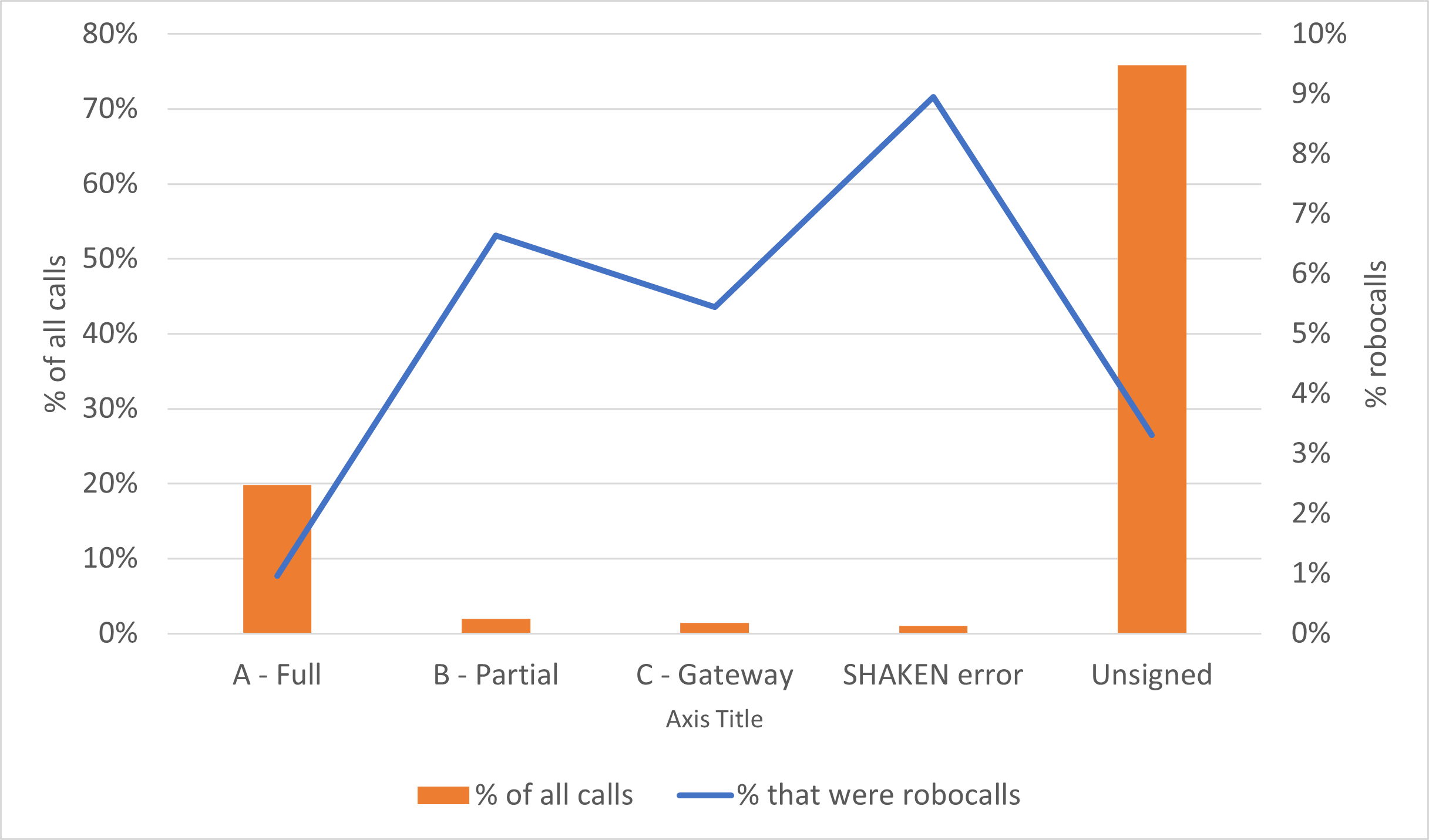
Calls and Robocalls by Verification Status
We’ve been following this story since July 2021. We found a surprisingly high percentage of calls signed with partial (B) attestation were robocalls. In July 2021, it was almost 8%. We found that many of these robocalls were signed by downstream providers for their upstream service provider customers.
Robocalls as a percentage of calls with partial (B) attestation dropped from 7.93% in July to 6.64% in August.
In July, 3.5% of calls with gateway (C) attestation were robocalls. In August, this number increased to 5.45%.
It appears that some downstream providers may have changed their attestation policy and are signing more calls with gateway attestation instead of partial attestation. It will be interesting to see if this change is a blip or a trend.
A high percentage of calls that failed SHAKEN verification with errors were robocalls, 8.95%. This is up from 6% in July—almost a 3% increase.

Originating service providers signing calls
There were 193 different originating service providers that signed calls. The trend is upward, but the growth rate is slowing.
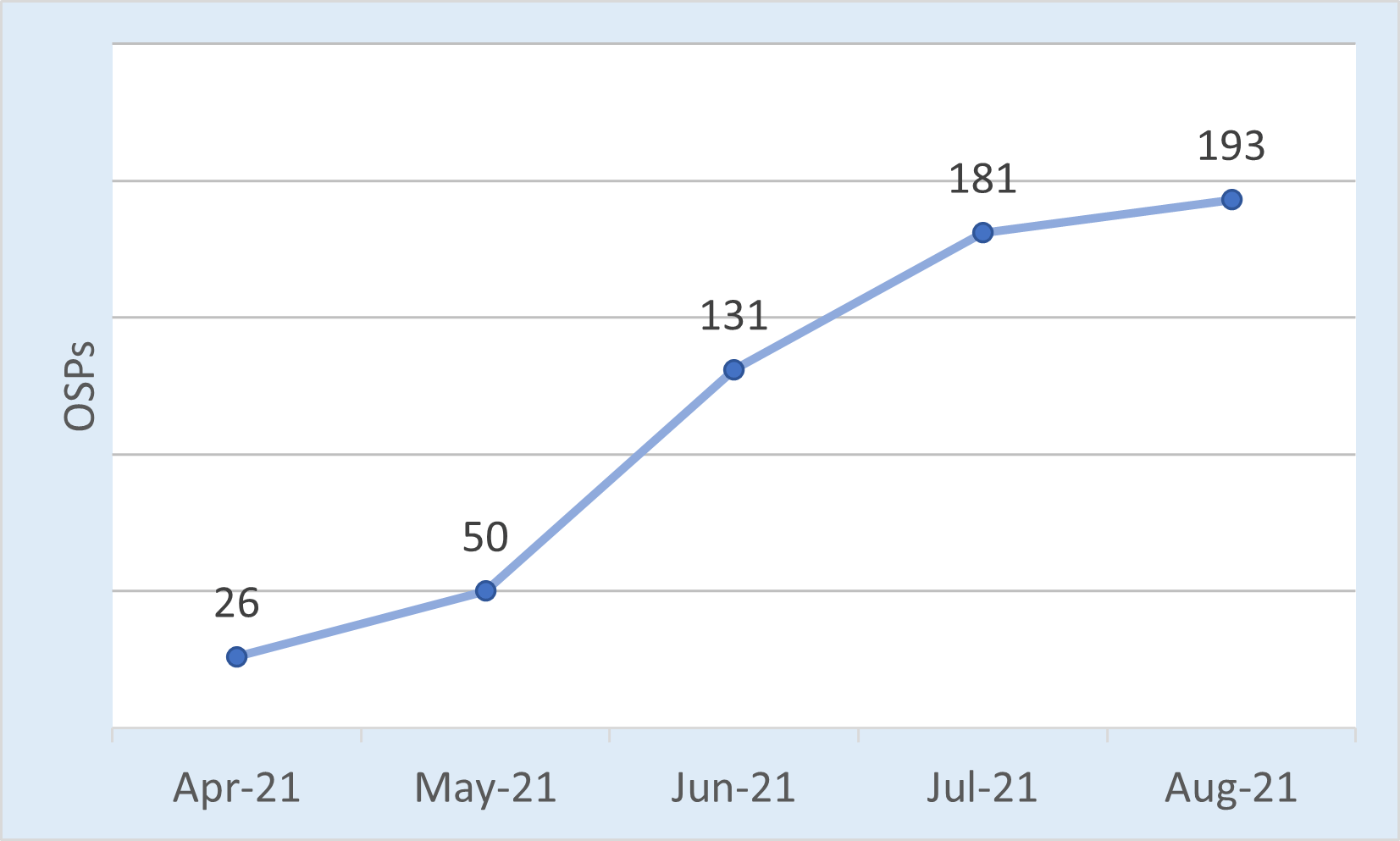
SHAKEN OSP Participation by Month
As in previous months, there’s a big difference between the number of service providers that certified either complete or partial SHAKEN implementation in the Robocall Mitigation Database compared to providers approved by the STI-PA for SHAKEN and the numbers of OSPs observed sending signed calls that appear for verification.
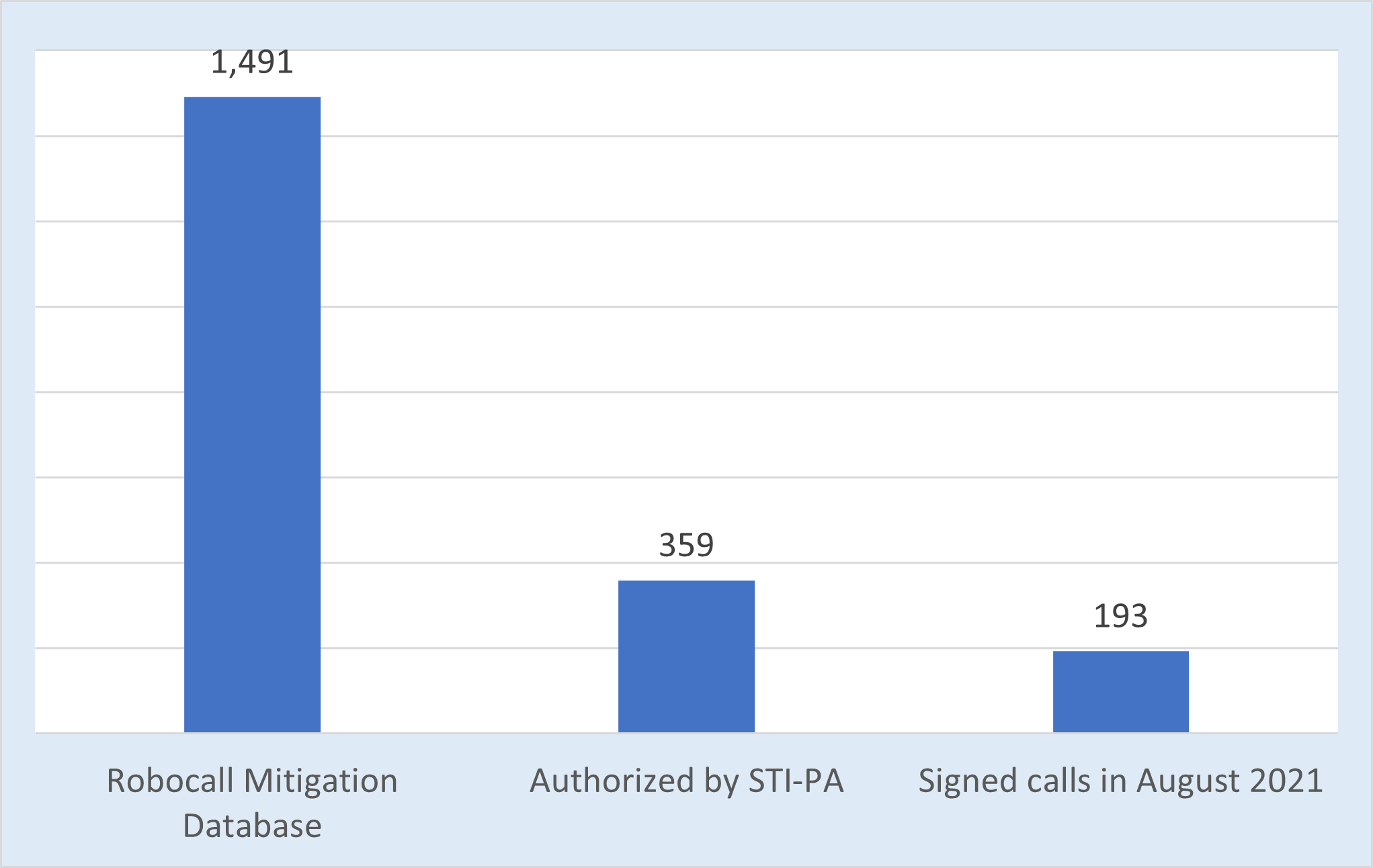
SHAKEN OSP Counts Differ
We’ve done some digging into this, and we have found many instances where calls were signed with SHAKEN at origination, but the SHAKEN PASSporT did not survive transit to the terminating service provider. Intermediate providers are receiving calls on IP networks and sending them along on TDM networks. Perhaps this might account for some of the difference between OSPs authorized by the STI-PA versus observed signing calls.
Verification status and errors
| Verification status | April | May | June | July | August |
|---|---|---|---|---|---|
| No PASSporT | 97.15% | 93.62% | 90.58% | 83.47% | 75.81% |
| Successful | 2.83% | 6.20% | 8.95% | 15.57% | 23.17% |
| Errors | 0.02% | 0.18% | 0.48% | 0.96% | 1.02% |
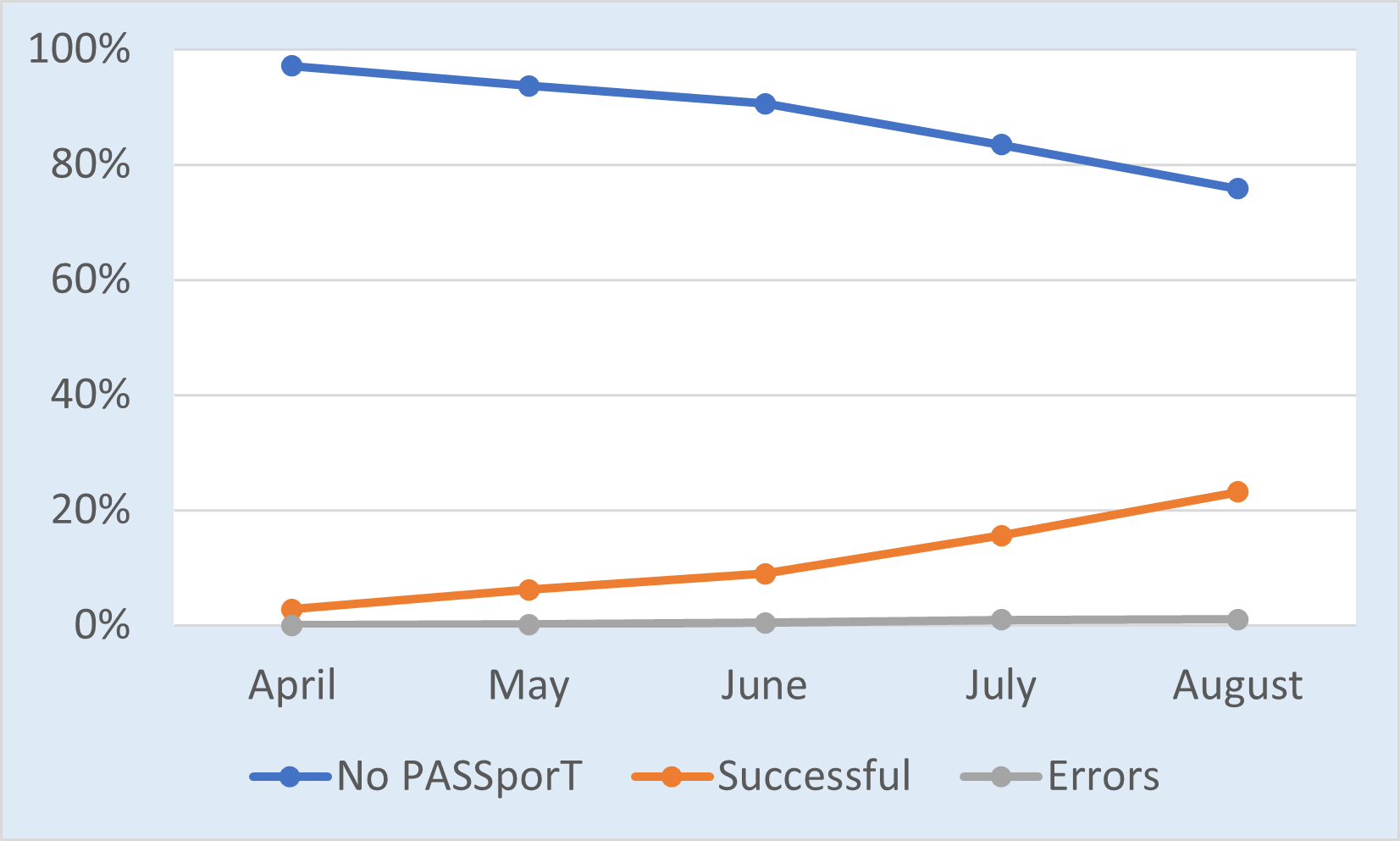
SHAKEN Verification Status Over Time
More calls are being signed, fewer calls are unsigned, and verification errors are getting worse.
Summary
There’s good news and some cause for concern.
- The percentage of signed calls continues upward, but it’s still small.
- Robocalls are still being signed with SHAKEN. The attestation level they are receiving may be migrating from partial (B) to gateway (C).
- SHAKEN information is being lost in transit. Some intermediate providers are receiving signed calls on IP networks and sending them downstream over TDM networks. The non-IP extension is crippling progress toward widespread call authentication.
- SHAKEN participation is increasing, but it’s leveling off. This is exacerbated by the non-IP problem.
TransNexus solutions
We offer STIR/SHAKEN and robocall mitigation solutions in our ClearIP and NexOSS software platforms. We can make your STIR/SHAKEN deployment a smooth process.
In addition, we help service providers with all aspects of STIR/SHAKEN deployment, including registering with the Policy Administrator and filing their certification with the FCC.
Contact us today to learn more.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy