Denial-of-service attacks target telcos
Several voice service providers have been targeted recently by distributed denial of service (DDoS) attacks. Here’s a recap.
Confirmed victims include the following:
- Voip Unlimited and Voipfone, two U.K.-based telephone service providers, as reported here.
- VoIP.ms, a Canadian telephone service provider, as reported here.
All have restored service since these attacks were reported.
In addition, Bandwidth.com, a large U.S.-based CLEC (Competitive Local Exchange Carrier), has reported partial service outages over the past few days. There were reports on bleepingcomputer.com, reddit, and the VoiceOps email list that Bandwidth was the target of a DDoS attack. David Morken, Bandwidth CEO, confirmed this in a message to customers and partners on September 28.
Background
A Denial-of-Service (DoS) attack is when a bad actor uses a computer program to stream heavy traffic to a victim’s network-accessible resource, like a website or VoIP telephone network.
A Distributed Denial of Service (DDoS) attack is when a bad actor infects many other network-accessible computers, or even Internet-of-Things (IoT) devices, with software that can stream heavy traffic to a victim’s network-accessible resource. These compromised computers/devices become a bot network that launches a simultaneous denial of service attack. This is what makes it distributed.
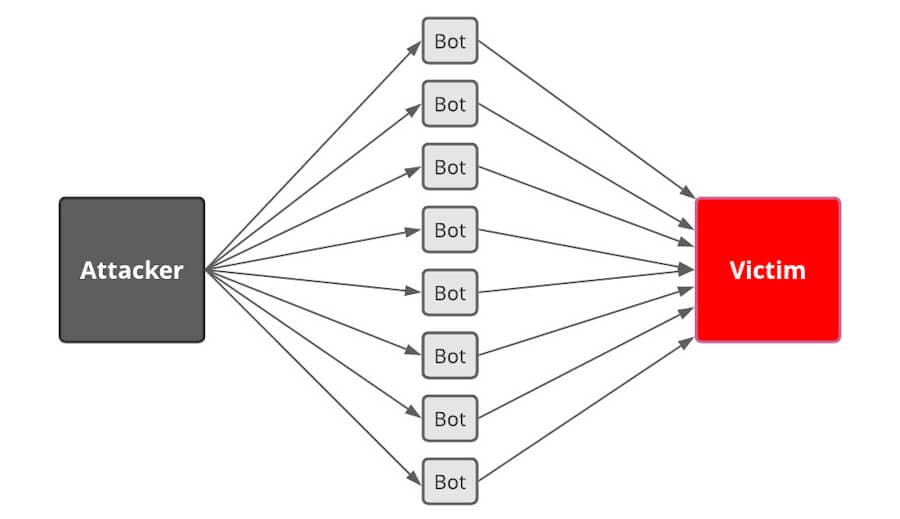
Distributed Denial of Service Attack
DDoS attacks can be amplified for greater effect. For example, a UDP-based amplification attack sends UDP packets to another server, such as a DNS (Domain Name System) or NTP (Network Time Protocol) server, with a spoofed sender IP address. The spoofed sender IP address is the attack target. UDP doesn’t involve a handshake, so spoofing is possible. The server replies to the spoofed sender IP address, and the response packets can be 10 to 100 times larger than the request was.
The motive: ransomware. The bad actor contacts the victim and asks for ransom payment, paid in cryptocurrency, to stop the attack.

DDoS prevention
Network security vendors use a variety of techniques to identify and thwart DDoS attacks, such as rate limiting. This technique monitors the frequency of requests from a client. Excessive requests can be diverted to a queue, challenged, or discarded. The idea is to preserve network capacity for legitimate traffic while diverting or blocking the attack.
The Cybersecurity & Infrastructure Security Agency (CISA) Security Tip ST04-015 explains DoS/DDoS attacks and provides security tips.
Did the victims do anything wrong?
We wouldn’t lay blame on these companies for being targeted and experiencing service disruptions. They are victims of criminal attacks and extortion attempts. The criminals have become more aggressive, and the attacks are growing in scale.
Case in point: In August 2021, Cloudflare announced that they detected and mitigated the largest DDoS attack ever reported. The attack generated 17.2 million requests per second. The traffic was generated by over 20,000 helper bots spread across 125 countries.
DDoS attacks are a serious risk, and the threat is growing. Service providers and enterprises should be vigilant in protecting their networks.
TransNexus solutions
We are frequently contacted by voice service providers and enterprises to help them protect their network from Telephony Denial of Service (TDoS) attacks. TDoS attacks are like DoS/DDoS attacks, except the attack is made with phone calls, not packets. We offer TDoS prevention solutions for service providers and enterprises in our ClearIP and NexOSS software platforms. Here’s a case study example.
Contact us today to learn more.
Updated September 28, 2021, with links to recent news items.
Updated September 30, 2021, with a link to Bandwidth’s message to their customers and partners.
Atlantic Coast Automotive uses ClearIP to protect their business from TDoS attacks.
Learn more about the ACA case study