Domestic telecom toll fraud is still a problem
The FCC adopted an order on September 26, 2019 designed to prevent access arbitrage, i.e., domestic traffic pumping telecom toll fraud. Since then, service providers have noticed domestic traffic pumping attacks still occur. How is this possible, given the new rules on who pays? We review the situation here.
Before the order
Before the FCC order, domestic traffic pumping was designed to exploit an exception in the rules against access arbitrage when a Centralized Equal Access (CEA) provider was in the call path, as follows:
Previous FCC rules allowed a traffic-pumping loophole when a CEA was in the call path
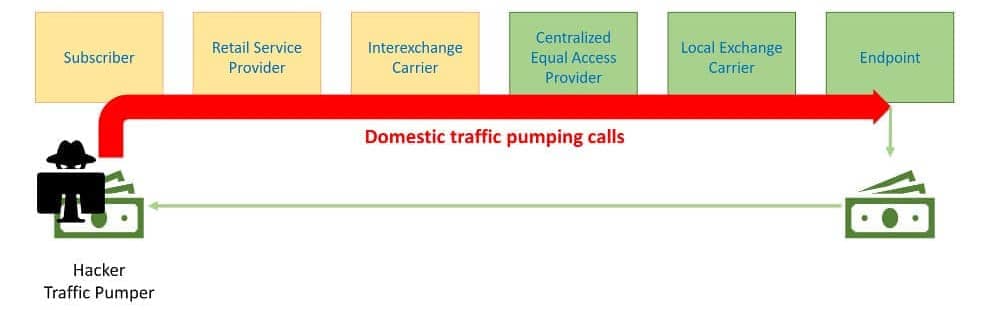
We described this scheme in more detail in a previous blog post. Fraudsters would typically hack into a subscriber’s PBX and pump traffic to an endpoint of the access-stimulating Local Exchange Carrier to generate high access termination fees.

New rules
The new rules in Docket WC 18-155 included the following changes:
- Financial responsibility for all tandem switching and transport services was shifted to access-stimulating LECs from the point where an access-stimulating LEC directs interexchange carriers to hand off the LEC’s traffic.
- The definition of access stimulation was broadened to include situations where there is no revenue sharing agreement in place, including:
- Competitive LECs with an interstate terminating-to-originating traffic ratio of at least 6:1 in a calendar month;
- Rate-of-return LECs with an interstate terminating-to-originating traffic ratio of at least 10:1 in a three calendar month period and 500,000 minutes or more of interstate terminating minutes-of-use per month in an end office in the same three calendar month period.
These rules were designed to remove financial incentives for access arbitrage involving domestic traffic pumping. If the access stimulating LEC must pay terminating access fees, then they would discontinue domestic traffic pumping schemes.
Results
Unfortunately, domestic traffic pumping continues. Several voice service providers have noticed hackers are still hacking into PBXs and pumping traffic to domestic endpoints.
But how do the fraudsters make any money on this?
This has been a topic of discussion among industry observers. A consensus is emerging that the fraudsters monetize this by revenue sharing among the last few providers in the call path. There isn’t as much revenue available as before the rule changes, but there is some, and fraudsters continue to pump traffic to domestic endpoints. Here’s an example.
Case study of domestic traffic pumping
A service provider recently contacted us about a domestic traffic pumping attack that they observed. We will not share specific details to respect the privacy of the providers involved, but we can provide a general overview of the nature of the attack.
The service provider observed 1,662 calls within a 24-hour period to higher cost domestic endpoints, mostly in Iowa. We grouped these calls by total termination rates as follows:
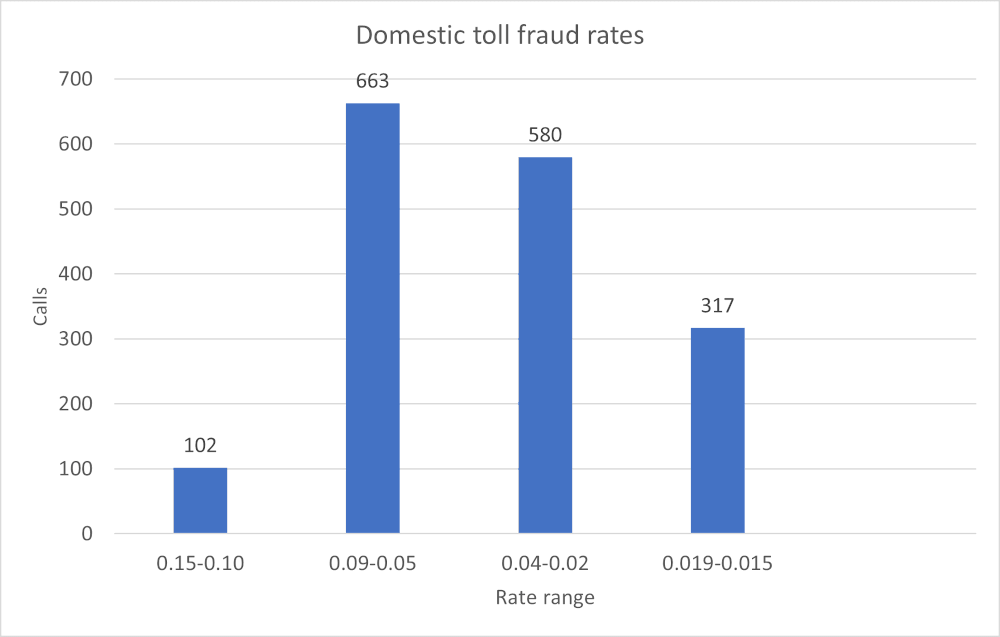
Fortunately, toll fraud prevention techniques can still detect and prevent such attacks. Service providers have to be alert and use these techniques to protect their business and customers.
TransNexus solutions
We offer SIP Analytics with our ClearIP and NexOSS software platforms. SIP Analytics inspects each call before it begins. It’s the fastest way available to detect and prevent telecom toll fraud.
Contact us today to learn more.
SIP Analytics® inspects each call before it begins. It’s the fastest, most precise method available to detect and prevent telecom toll fraud.
Learn more about SIP Analytics