Stop Spoofed Robocalls with STIR and SHAKEN
TransNexus has written extensively about the scourge of robocalls and fraud in the telecom network. Americans are reminded daily about the illegal, spoofed robocalls that are afflicting all of us.
Many of the illegal calls use caller ID spoofing, which occurs when the originator of the call manipulates the telephone network in order to display a number that is different than the originating number. Most of the time, spoofed caller IDs are very similar to the number that is being dialed which increases the likelihood the call will be answered.
STIR and SHAKEN are protocols created to combat bad actors who use caller ID spoofing to increase the chances of speaking to a subscriber. TransNexus has written about and followed the development of these frameworks that promise to make a significant impact in the number of robocalls ultimately reaching subscribers.
Jim Dalton, CEO of TransNexus, has noted that STIR and SHAKEN have two major strengths: “First, the new standard enables a highly competitive ecosystem of solutions. Users and telephone companies will have choices for secure caller ID. Second, a secure caller ID raises the integrity of the telephone network to a level that will enable new, unimagined applications and transactions.”
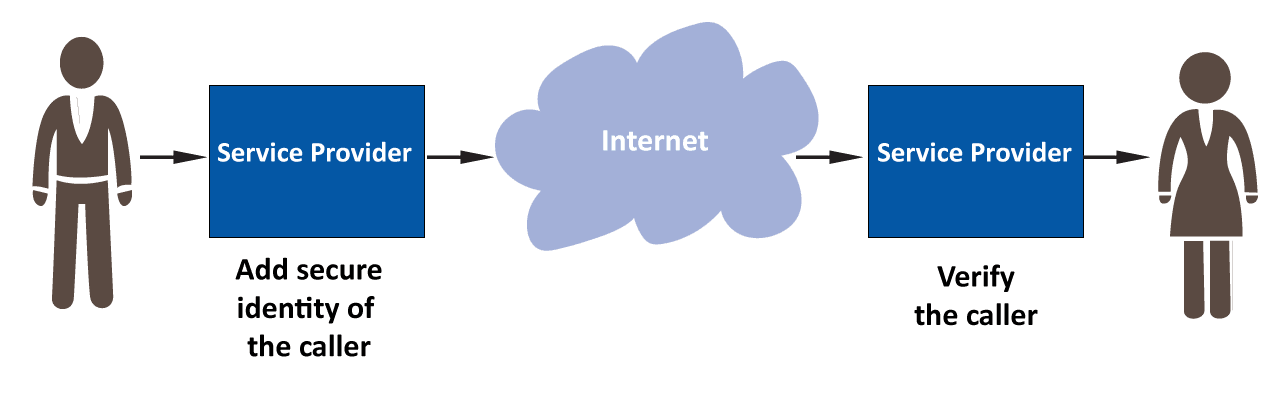
The (simplified) illustration below shows how STIR/SHAKEN will work in a VoIP network. A subscriber makes an outgoing call and that call is secured and authenticated by the service provider. It’s passed over the internet and received by the recipient’s ISP which verifies the call before completing it. When an authorized call is received, consumers will be confident in answering a call that does not have a spoofed caller ID.
STIR, SHAKEN, and the FCC
Around 2015, the FCC began exploring these protocols, in earnest, and have just announced a Notice of Inquiry (NOI) in order to seek comment around call authentication frameworks, namely STIR and SHAKEN. The FCC has worked the last few years to put an end to some of these robocalls and this recent call for an NOI is a continuation of the work, with a focus around STIR and SHAKEN as the solution to stop spoofed calls.
The Notice of Inquiry has been set up to get public comment on the following:
- The role of the FCC in ensuring call authentication.
- The system of call authentication, specifically the industry-proposed protocol, SHAKEN: the criteria around the roles within the SHAKEN protocol, the governance authority, policy administrator, and certification authorities.
- The impact of call authentication on reducing robocalls on VoIP and legacy telephone systems.
The FCC is working towards implementing standards for authenticating calls. Stakeholders, including the Internet Engineering Task Force (IETF), Alliance for Telecommunications Industry Solutions (ATIS), SIP Forum, and others, have developed STIR and SHAKEN in order to address the issue of caller ID spoofing. The FCC wants to seek comment around introducing these protocols and what the role of the FCC will be around these frameworks for caller authentication.
The work done by ATIS and the SIP forum is comprised of three phases: SHAKEN framework, the governance model around guaranteeing call authenticity, and call validation display framework that recommends how to display SHAKEN and STIR information to consumer. Only phases one and two are included in the current NOI, as work continues on how to display the information to the end user.
Phase One: the SHAKEN Framework
The first phase of stopping spoofed robocalls is authenticating the calls with STIR/SHAKEN. STIR “defines a [digital] signature to verify the calling number and specifies how it will be transported in SIP.” This information is used by telephone service providers to verify the call’s authenticity. SHAKEN is a framework to implement the protocols produced by STIR.
Using STIR/SHAKEN, the call is authenticated by the calling party’s service provider that digitally signs the calling number. The called party’s service provider validates the digital signature to verify the calling party identity. The SHAKEN governance framework defines how service providers are authenticated and authorized by a certificate authority to digitally secure the calling number of telephone calls.
STIR/SHAKEN Setup
- Telephone service providers generate their own private/public key pair. They will use their private key to digitally sign telephone numbers and provide their public key so anyone can verify their digital signatures.
- Telephone service providers receive authorization from the policy administrator to submit their public key to an authorized certificate authority who will create a certificate that can be used by anyone to validate the service provider.
When a call is made under STIR/SHAKEN
- The originating service provider digitally signs the calling number with its private key to create a cryptographic identity token.
- The originating service provider includes the digitally signed identity token in the call setup to the terminating service provider. The originating service provider also includes its certificate and a link to the certificate authority that proves the certificate is valid.
- The terminating service provider checks that the originating service provider’s certificate is valid.
- The terminating service provider decrypts the identify token using the originating service provider’s certificate. If the calling number in the decrypted identity token matches the calling number in the telephone call setup, then the calling number is valid and the call came from the originating service provider.
Phase Two: Governance and Certification
In order to operate effectively, a certificate management system needs to be developed and many roles need to be filled. The FCC has to define how service providers receive the certificates described above to authenticate the calls and how they are subsequently managed.
The current proposal has seven requirements around a certificate management system and will take place before a service provider starts authenticating any calls.
- Determine the certification authority that will issue certificates
- How to register with the certification authority
- How to request certificates
- How to validate the service provider
- How to add public key certificates to a repository
- How to renew or update certificates
- How to cancel certificates
In order for the management system to operate effectively, the following roles have been identified:
- Governance authority: define policies and procedures around who can issue and who can acquire certificates.
- Policy administrator: Sets the rules and confirms certification authorities can issue certificates; service providers can request and receive certificates
- Certification authority: Certification issuer
- Service providers: depending on size, service providers could have a certificate authority within the organization.
The FCC Questions
The FCC has opened this NOI to receive public comment on how the commission should go about both implementing and governing STIR and SHAKEN. They are seeking comment around not just the technical implementation of the protocols, but also the role of the FCC in the new system.
Their questions around SHAKEN, STIR, and the implementation are extensive. The FCC wants to ensure this new method of stopping spoofed calls works well and is significant to both service providers and consumers. As the public starts to comment on the proposed authentication process, TransNexus will keep readers updated.
A previous NOI around other methods targeting robocalls has public comments pouring in over the last few weeks. TransNexus readers can expect a digest soon of the more salient comments and suggestions. We are committed to keeping readers aware of the progress made towards decreasing telephone fraud, so keep coming back to the website and the blog for more in our series around fraud, security and STIR/SHAKEN.