Understanding STIR/SHAKEN
Criminals and unscrupulous robocallers often alter or spoof the calling number of their outbound telephone calls in order to deceive the called party. This deception can be as simple as changing the calling number so it appears that a neighbor is calling.
This deception increases the chance that the called party will answer a robocall. In other cases, the deception may be more malicious, such as a fraudster impersonating an IRS agent in order to steal a tax refund. This practice of altering the calling number of a telephone call is known as spoofing.
The Federal Communications Commission (FCC) has been encouraging the telecommunications industry to develop a solution to stop robocalls and spoofed calling numbers since 2014. The industry’s response has been to develop a new technology standard called STIR [1] (Secure Telephony Identity Revisited) and SHAKEN [2] (Secure Handling of Asserted information using toKENs) which defines how telephone service providers should implement the STIR technology to ensure calling numbers are not spoofed.
How STIR/SHAKEN works
STIR/SHAKEN uses digital certificates, based on common public key cryptography techniques, to ensure the calling number of a telephone call is secure. In simple terms, each telephone service provider obtains their digital certificate from a certificate authority who is trusted by other telephone service providers. The certificate technology enables the called party to verify that the calling number is accurate and has not been spoofed. The details of how SHAKEN uses public key infrastructure is explained in our whitepaper on Certificate Management for STIR/SHAKEN.
The following call flow diagram illustrates how STIR/SHAKEN works:
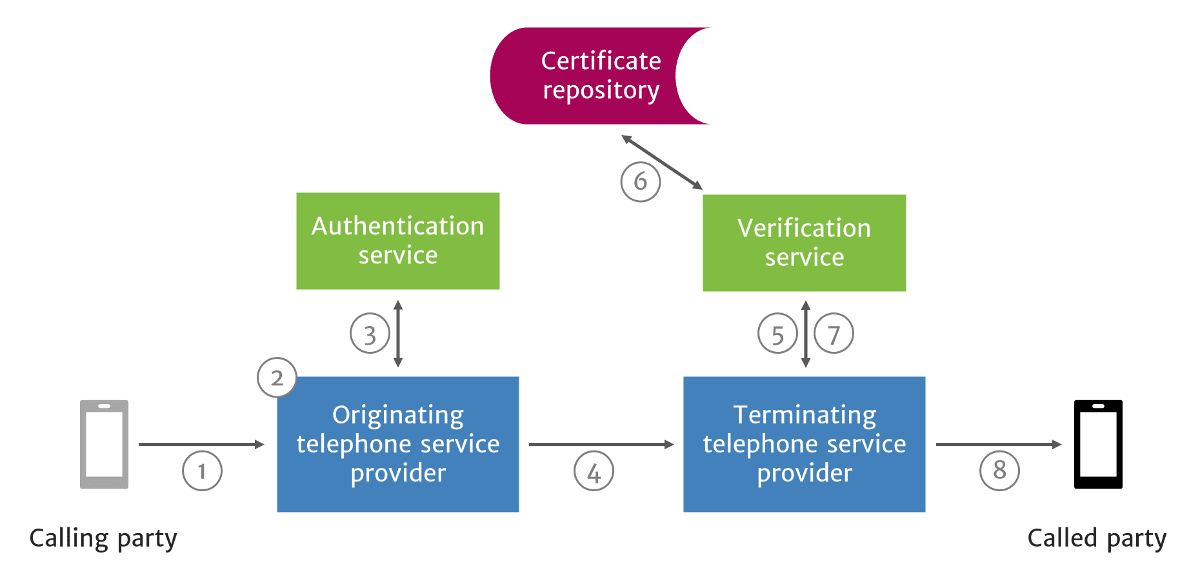
How STIR/SHAKEN Works in a Network
- A SIP INVITE is received by the originating telephone service provider.
- The originating telephone service provider checks the call source and calling number to determine how to attest for the validity of the calling number.
- Full Attestation (A) — The service provider has authenticated the calling party and they are authorized to use the calling number. An example of this case is a subscriber registered with the originating telephone service provider’s softswitch.
- Partial Attestation (B) — The service provider has authenticated the call origination, but cannot verify the call source is authorized to use the calling number. An example of this use case is a telephone number behind an enterprise PBX.
- Gateway Attestation (C) — The service provider has authenticated from where it received the call, but cannot authenticate the call source. An example of this case would be a call received from an international gateway.
- The originating telephone service provider uses the authentication service to create a SIP Identity header. The authentication service could be a third-party service hosted in the cloud a software application integrated with the telephone service provider’s softswitch or Session Border Controller (SBC). The SIP Identity header contains the following data:
- Calling number
- Called number(s)
- Current timestamp
- Attestation level
- Origination identifier
- The SIP INVITE with the SIP Identity header is sent to the terminating telephone service provider. In addition, the Identity token may be sent across the internet, around non-SIP call segments, using Out-of-Band SHAKEN.
- The SIP INVITE with Identity header is passed to the verification service.
- The verification service obtains the digital certificate of the originating telephone service provider from the public certificate repository and begins a multi-step verification process. If all verification steps are successful, then the calling number has not been spoofed.
- The SIP Identity header is base64 URL decoded and the details are compared to the SIP INVITE message.
- The public key of the certificate is used to verify the SIP Identity header signature.
- The certificate chain of trust is verified.
- The verification service returns the results to the terminating service provider’s softswitch or SBC.
- The call is completed to the called party.
SIP Identity header example
The following is an example SIP INVITE message with an Identity header:
SIP invite example
INVITE sip:18001234567@example.com:5060 SIP/2.0
Via: SIP/2.0/UDP example.com:5060
From: "Alice" <sip:14045266060@5.6.7.8:5060>;tag=123456789
To: "Bob" <sip:18001234567@1.2.3.4:5060>
Call-ID: 1-12345@5.6.7.8
CSeq: 1 INVITE
Max-Forwards: 70
Identity: eyJhbGciOiJFUzI1NiIsInBwdCI6InNoYWtlbiIsInR5cCI6InBhc3Nwb3J0IiwieDV1IjoiaHR0cHM6Ly9jZXJ0aWZpY2F0ZXMuZXhhbXBsZS5jb20vMTIzNDU2Nzg5LnBlbSJ9.eyJhdHRlc3QiOiJBIiwiZGVzdCI6eyJ0biI6WyIxODAwMTIzNDU2NyJdfSwiaWF0IjoxNTQ4ODU5OTgyLCJvcmlnIjp7InRuIjoiMTQwNDUyNjYwNjAifSwib3JpZ2lkIjoiM2E0N2NhMjMtZDdhYi00NDZiLTgyMWQtMzNkNWRlZWRiZWQ0In0.S_vqkgCk88ee9rtk89P6a6ru0ncDfSrdb1GyK_mJj-10hsLW-dMF7eCjDYARLR7EZSZwiu0fd4H_QD_9Z5U2bg;info=<https://certificates.example.com/123456789.pem>alg=ES256;ppt=shaken
The SIP Identity header contains a JSON web token (JWT) and three parameters. The JWT has three sections: header + payload + signature. The header and payload are base64 URL encoded JSON. The contents of each section are described below.
The SIP Identity header is comprised of a web token and parameters, as follows:
- JSON web token
- Header
- Payload
- Signature
- Parameters
- Info
- Alg
- PPT
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy
JSON web token
Encoded Header
Identity: eyJhbGciOiJFUzI1NiIsInBwdCI6InNoYWtlbiIsInR5cCI6InBhc3Nwb3J0IiwieDV1IjoiaHR0cHM6Ly9jZXJ0aWZpY2F0ZXMuZXhhbXBsZS5jb20vMTIzNDU2Nzg5LnBlbSJ9.eyJhdHRlc3QiOiJBIiwiZGVzdCI6eyJ0biI6WyIxODAwMTIzNDU2NyJdfSwiaWF0IjoxNTQ4ODU5OTgyLCJvcmlnIjp7InRuIjoiMTQwNDUyNjYwNjAifSwib3JpZ2lkIjoiM2E0N2NhMjMtZDdhYi00NDZiLTgyMWQtMzNkNWRlZWRiZWQ0In0.S_vqkgCk88ee9rtk89P6a6ru0ncDfSrdb1GyK_mJj-10hsLW-dMF7eCjDYARLR7EZSZwiu0fd4H_QD_9Z5U2bg;info=<https://certificates.example.com/123456789.pem>alg=ES256;ppt=shaken
Decoded Header
{
"alg": "ES256",
"ppt": "shaken",
"typ": "passport",
"x5u": "https://certificates.example.com/123456789.pem"
}
- alg — This value indicates the encryption algorithm. Must be ES256.
- ppt — This value indicates the extension used. Must be shaken.
- typ — This value indicates the token type. Must be passport.
- x5u — This value indicates the location of the certificate used to sign the token.
Encoded Payload
Identity: eyJhbGciOiJFUzI1NiIsInBwdCI6InNoYWtlbiIsInR5cCI6InBhc3Nwb3J0IiwieDV1IjoiaHR0cHM6Ly9jZXJ0aWZpY2F0ZXMuZXhhbXBsZS5jb20vMTIzNDU2Nzg5LnBlbSJ9.eyJhdHRlc3QiOiJBIiwiZGVzdCI6eyJ0biI6WyIxODAwMTIzNDU2NyJdfSwiaWF0IjoxNTQ4ODU5OTgyLCJvcmlnIjp7InRuIjoiMTQwNDUyNjYwNjAifSwib3JpZ2lkIjoiM2E0N2NhMjMtZDdhYi00NDZiLTgyMWQtMzNkNWRlZWRiZWQ0In0.S_vqkgCk88ee9rtk89P6a6ru0ncDfSrdb1GyK_mJj-10hsLW-dMF7eCjDYARLR7EZSZwiu0fd4H_QD_9Z5U2bg;info=<https://certificates.example.com/123456789.pem>alg=ES256;ppt=shaken
Decoded Payload
{
"attest": "A",
"dest": {
"tn": [
"18001234567"
]
},
"iat": 1548859982,
"orig": {
"tn": "14045266060"
},
"origid": "3a47ca23-d7ab-446b-821d-33d5deedbed4"
}
- attest — This value indicates the attestation level. Must be either A, B, or C.
- dest — This value indicates the called number(s) or called Uniform Resource Identifier(s).
- iat — This value indicates the timestamp when the token was created. The timestamp is the number of seconds that have passed since the beginning of 00:00:00 UTC 1 January 1970.
- orig — This value indicates the calling number or calling Uniform Resource Identifier.
- origid — This value indicates the origination identifier.
Signature
S_vqkgCk88ee9rtk89P6a6ru0ncDfSrdb1GyK_mJj-10hsLW-dMF7eCjDYARLR7EZSZwiu0fd4H_QD_9Z5U2bg
Parameters
info
info=<https://certificates.example.com/123456789.pem>;
This value indicates the location of the certificate used to sign the token. It must be the same as the x5u value in the JWT.
alg
alg=ES256;
This value indicates the encryption algorithm. Must be ES256.
ppt
ppt=shaken
This value indicates the extension used. Must be shaken.
TransNexus STIR/SHAKEN solutions
We offer production-ready STIR/SHAKEN solutions in our ClearIP and NexOSS software products. These solutions are unique in their capabilities to combine complete STIR/SHAKEN services with flexible policy controls and a comprehensive portfolio of other services, including fraud prevention, least cost routing and much more.
Contact us today to explore how we can help you implement SHAKEN quickly and easily.
Notes
- STIR, or Secure Telephony Identity Revisited, is a Working Group of the Internet Engineering Task Force (www.ietf.org). The IETF’s stated mission is to make the Internet work better by producing high quality, relevant technical documents that influence the way people design, use, and manage the Internet. The charter for the STIR Working Group (WG) is to define mechanisms that allow verification of the calling party's authorization to use a particular telephone number. The IETF standards developed by the STIR WG are:
- RFC 8224. Defines how SIP Identity tokens are used to authenticate and verify the calling number in SIP signaling.
- RFC 8225. Defines a method for creating and validating a token that cryptographically verifies a calling number.
- RFC 8226. Describes the use of certificates in establishing authority over telephone numbers.
- SHAKEN provides telephone services providers with a framework and guidance on how to use techniques defined by the STIR WG for validation of legitimate calls and the mitigation of illegitimate spoofing of telephone identities on the VoIP Telephone Network. SHAKEN is formally known as the ATIS Standard on Signature-based Handling of Asserted Information Using Tokens. ATIS (www.atis.org), or the Alliance for Telecommunications Industry Solutions, is accredited by the American National Standards Institute (ANSI).
More on TransNexus.com
April 17, 2024
April 1, 2024
STIR/SHAKEN statistics from March 2024
March 4, 2024
STIR/SHAKEN statistics from February 2024
February 14, 2024
STIR/SHAKEN statistics from January 2024
January 25, 2024
Compliance dates announced for updated SHAKEN rules
January 3, 2024
STIR/SHAKEN statistics from December 2023
December 18, 2023
SHAKEN deadline for non-gateway intermediate providers
December 6, 2023
STIR/SHAKEN statistics from November 2023
November 8, 2023
STIR/SHAKEN statistics from October 2023
October 18, 2023
September 20, 2023
How to monitor SHAKEN signer reputation
August 30, 2023
U.K. progress on central number database for STIR/SHAKEN
July 27, 2023
Rich Call Data and caller identity
June 19, 2023
Can Rich Call Data solve incorrect spam call labeling?
May 31, 2023
TransNexus has a comprehensive suite of robocall mitigation solutions to prevent the origination of unlawful robocalls.
Learn more