Metaswitch inbound configuration for ClearIP
ClearIP is a cloud-based solution that complements the Metaswitch CFS with a variety of services, including:
- Analytics
- Telecom fraud prevention
- Robocall and TDoS prevention
- Jurisdictional static and least cost routing
- STIR/SHAKEN caller ID authentication and verification
- CNAM caller ID name information
ClearIP integrates with the Metaswitch CFS using a SIP INVITE—Redirect transaction. SIP messages between the CFS and ClearIP will pass through Perimeta. The Perimeta will connect to ClearIP over the internet using either a TCP or TLS connection.
This documentation guides you on configuring your Metaswitch CFS and Perimeta to route inbound calls coming into your network to ClearIP before they go to your subscribers. This documentation should only be used if you are not using an EAS (Enhanced Application Server) to provide terminating subscriber services. These instructions assume you are familiar with using configuration tools such as MetaView Explorer and the MetaView Web Subscriber Management Portal.
We require your MetaView Server to be at least version 9.3.20 with maintenance release 29+. The MetaView Server is used to manage the Call Feature Server, Universal Media Gateway and Enhanced Application Server.
Here are the configuration steps:
At the end of this page, we’ve provided a complete reference for two Remote Media Gateway models. In all configuration examples, we have highlighted values you should change to match names used in your network.
Configuration process
1. Create a new peering adjacency to your Perimeta SBC
Create an adjacency facing the external ClearIP service on the public internet. There’s nothing unusual about the ClearIP adjacency; just follow the standard Metaswitch documentation for this step.
If you plan to send both outbound and inbound traffic to ClearIP, then ClearIP needs a way to distinguish between outbound and inbound calls. This can be done by setting up two adjacencies: one for outbound calls, and the other for inbound calls. You will need two publicly-addressable IP addresses, one for each adjacency. The adjacency for inbound calls should use a different source IP address than the adjacency for outbound calls.
- Here’s a sample Perimeta adjacency configuration for inbound calls:
adjacency sip ClearIP Inbound adjacency-limits regs 0 regs-rate sustain 0 per-second call-media-policy media-bypass-policy forbid interop ping-enable fail-count 3 interval 10 lifetime 5 listen-transports tcp adjacency-type preset-peering mandated-transport tcp privacy trusted service-address Service Address # service-network 2 # signaling-local-address ipv4 External IP Two signaling-local-port 5060 signaling-peer inbound.sip.clearip.com dynamic-routing-domain-match inbound.sip.clearip.com signaling-peer-port 5060 statistics-setting detail default-interop-profile Peer deactivation-mode normal activate
To ensure the Perimeta can resolve ClearIP’s fully-qualified domain name, please check that DNS servers have been configured. This can be done by logging into the Craft Terminal. Select Admin, then Network, then DNS. You will have the option to check the current DNS configuration, set new DNS servers, and test DNS. Please perform a test DNS lookup on sip.clearip.com. If the DNS lookup is successful, you will see a confirmation message like the example below. If the DNS lookup fails, then you will see an error or timeout message and should configure a DNS server.
- Here’s an example of a successful DNS lookup test:
-------------------------------------------------------------------------------- Perimeta ISC LabPerimeta is running This is processor-blade B; processor-blade A is contactable; Session Controller is partnered; processor-blade B is primary [Main->Admin->Network->DNS] [=2 6 4] Manage the DNS server configuration Press ENTER to refresh 0 Back < Back to previous menu 1 Get DNS info Get the current DNS configuration 2 Set DNS servers Set DNS servers 3 Set selection mode Set server selection mode 4 Test DNS Perform a DNS lookup : 4 -------------------------------------------------------------------------------- Test DNS Perform a DNS lookup to test the configured DNS servers. Enter domain name to query for Default value is: <BLANK> : sip.clearip.com -------------------------------------------------------------------------------- Test DNS - Perform a DNS lookup sip.clearip.com Please verify that this command is correct 1 *OK Execute this command 2 Cancel Cancel this operation 3 Modify Modify the parameters of this command : * 1 -------------------------------------------------------------------------------- Testing DNS server 8.8.4.4 Looking up sip.clearip.com Using domain server: Name: 8.8.4.4 Address: 8.8.4.4#53 Aliases: sip.clearip.com has address 35.175.114.71 sip.clearip.com has address 35.175.114.72 sip.clearip.com has address 35.175.114.73 sip.clearip.com has address 35.175.114.74 Testing DNS server 8.8.8.8 Looking up sip.clearip.com Using domain server: Name: 8.8.8.8 Address: 8.8.8.8#53 Aliases: sip.clearip.com has address 35.175.114.73 sip.clearip.com has address 35.175.114.74 sip.clearip.com has address 35.175.114.72 sip.clearip.com has address 35.175.114.71 -------------------------------------------------------------------------------- Result: The command has completed successfully Press ENTER to get list of commands: --------------------------------------------------------------------------------
2. Install a Remote Media Gateway model
At the bottom of this page, you’ll find two Remote Media Gateway models that you need to use for this connection. Choose the appropriate model for the version of MetaView Server that you are using.
Copy the text for this model and save it as a text file on your computer with name ClearIPRMGM.txt. Use WinSCP to copy the model to your MetaView Server (logging in to WinSCP as defcraft), saving it in the EMSftp directory. If you’re not familiar with using WinSCP, please follow the Metaswitch documentation.
In MetaView Explorer, go to Call Feature Server➔Controlled Networks➔Remote Media Gateway Models.
Find the Import field and enter the name of the file you just uploaded.
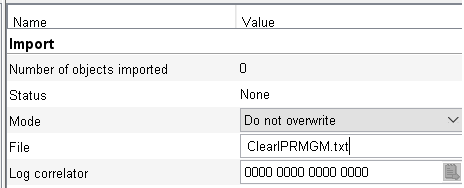
Press Apply, then press the Import button at the bottom of the screen. The new model should be imported.

Check the Status field to see if it was successful. If not, look at the error log.
If you have trouble importing the Remove Media Gateway model, you can create it manually using the reference output at the end of this page.
3. Create a configured SIP binding for inbound calls
Create a configured SIP binding using the Remote Media Gateway model. This SIP binding is set up as a Terminating Application Server.
Set the Contact Domain Name as inbound.sip.clearip.com, and set usage as Application Server.
The other values should be as follows:
- Use 5060 as your port, with Contact Address Scheme: Domain name A/AAAA lookup.
- Use the core network IP and port of Perimeta as your proxy IP and port.
- Set Transport Protocol to TCP.
- Select the remote media gateway model you imported above (TransNexus ClearIP).
- Set Use DN For Identification to True
- Apply the changes.
- Here’s a sample configured SIP binding configuration for inbound calls:
//UTF8 begin ConfiguredSIPBinding ConfiguredSIPBinding.536870951 // Configured SIP Binding “TransNexus ClearIP Inbound” Name TransNexus ClearIP Inbound Usage Application Server UseDNForIdentification True SIPAuthenticationRequired False IPAddressMatchRequired True ContactAddressScheme Domain name A/AAAA lookup ContactIPPort 5060 NoDTMFHubIfNotTerminatingMedia False ContactDomainName inbound.sip.clearip.com SupportedPreferredMediaAddressFamilies Use default SupportedPreferredMediaAddressFamiliesDefaultValue IPv4 SupportedPreferredMediaAddressFamiliesSpecificValue IPv4 SupportedIncomingTrunkGroupParameterType None TrunkGroupParameterTypeOnOutgoingMessages None ProxyIPAddress Perimeta IP Address ProxyIPPort 5060 TransportProtocol TCP SignalingType Same as Media Type MediaGatewayModel ../../MediaGatewayModelContainer/MediaGatewayModel.49 // Remote Media Gateway Model “TransNexus ClearIP” NetworkNode Use default NetworkNodeDefaultValue None NetworkNodeSpecificValue None SIPBindingLocation None Trusted True UseCallerNameProvidedBySIPDevice True PlayAnnouncementsWhenErrorConditionsOccur False UseStaticNATMapping False MaximumCallAppearances 10000 MaximumConcurrentHighBandwidthCallAppearancesAllowed 0 PollPeerDevice True PollingInterval 30 UseCustomSIPINVITEResponseTimeout False PollCallPaths False ConcurrentNumberOfCallAppearancesInUse 0 ConcurrentNumberOfHighBandwidthCallAppearancesInUse 0 DeactivationMode Normal LastCallFailure Last call failure LastCallFailureCause Subscriber not contactable LastCallFailureTimestamp 1/22/20 9:38:32 PM LastCallFailureLogCorrelator 0000 0000 0000 0000 AlarmsHeading Alarms FaultMonitoringProfile None AllowFMPsFromRelatedObjectsToApply True AlarmState Clear StatisticsAlarms 0 AlarmLogCorrelator 0000 0000 0000 0000 AttentionRequiredAlarmEvents 0 AlarmResetTimestamp 1/21/20 6:22:57 PM DiagnosticsHeading Diagnostics DiagnosticsLogLevel Default level DiagnosticsAPITraceEnabled False ExportHeading Export StatusHeading Status RequestedStatus Active end //ConfiguredSIPBinding
4. Create a Terminating Application Server for inbound calls
In MetaView Explorer, go to Connection to Call Feature Server➔Call Feature Server➔Call Feature Server➔Call Services➔Application Servers. Click the add sub-component button and select Application Server from the list of options.
Configure this new application server with the following settings:
- Set the Directory Number to an available telephone number within one of the number ranges owned by the CFS.
- Set Configured SIP binding as the configured SIP binding for inbound calls.
- Set the Server Type as Terminating.
- Set Action on failure as Bypass server.
- The other fields can be left as default values.
- Apply the changes.
- Here’s a sample Terminating Application Server configuration for inbound calls:
Description Incoming Calls to TransNexus SettingsHeading Settings ConfiguredSIPBinding ../../ControlledGatewaysContainer/ConfiguredSIPBindingContainer/ConfiguredSIPBinding.536870951 ServerType {Terminating} ActionOnFailure Bypass server RetryDelay 0 TerminatingServerProvideCallingName True TerminatingServerOnlyCorrelateSASTrails False TerminatingServerBillingOfTransfers Two records MaximumCallAppearances Specify value MaximumCallAppearancesDefaultValue 1024 MaximumCallAppearancesSpecificValue 10000 DiagnosticsHeading Diagnostics DiagnosticsLogLevel Default level DiagnosticsAPITraceEnabled False VQMCallLogging Use default VQMCallLoggingDefaultValue True VQMCallLoggingSpecificValue True AlarmsHeading Alarms AlarmState Clear StatisticsAlarms 0 AlarmLogCorrelator 842f 050b 58f7 9789 AdditionalAlarmLogCorrelator 0000 0000 0000 0000 AttentionRequiredAlarmEvents 0 AttendToDependentAlarmEvents 2 AlarmStateTimestamp 1/21/20 1:22:57 PM StatusHeading Status RequestedStatus Enabled ActualStatus Enabled
5. Enable the Terminating Application Server for inbound calls
For testing, you do not want the ClearIP application server you just created to be automatically applied on your subscriber’s inbound calls as the default application server. To ensure this, you should follow the instructions below. Then the application server must be enabled explicitly on each subscriber.
- In MetaView Explorer, go to Call Feature Server➔Call Feature Server➔Call Services➔Application Servers and select the ClearIP application server.
- Disable the application server.
- Look under the Terminating Service sub-heading.
- Set Support to Configured (it may already be set to this).
- Look at the Default Server. If one is already selected, leave it as is; otherwise select the ClearIP Application Server.
- Set the Default setting to False if you don’t want ClearIP Application Server to be the Default Server. May be set to TRUE if the ClearIP Application Server should be the default to avoid the requirement of opting in individual subscribers. Otherwise, leave this setting as is.
- Apply the change.
- Enable the application server.
For now, you should activate this application server as a Terminating Application Server on a test line. When you are ready to roll out ClearIP STIR/SHAKEN or robocall prevention in production, you will need to add the Terminating Application Server for all your subscribers. Please note that only one Terminating Application Server can be applied to any one subscriber at a given time.
You have two options to enable the terminating service: (1) MetaView Web Subscriber Management Portal, or (2) MetaView Explorer. Here are the instructions for each option.
Option 1. MetaView Web Subscriber Management Portal
- Log into the MetaView Web Subscriber Management portal.
- Find the subscriber.
- Look under Configuration Tab➔Advanced menu.
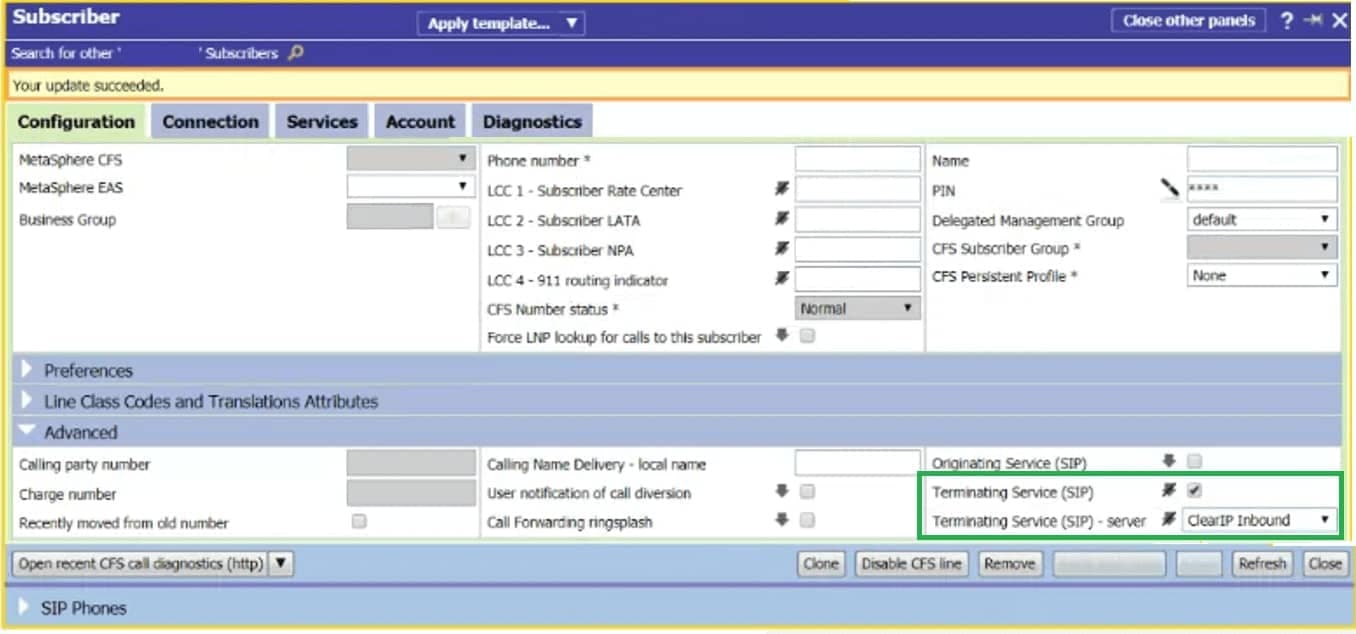
- Check the Terminating Service (SIP) box if it is not already checked. If it is checked, then the subscriber is already using another terminating application server. A given subscriber may only have one terminating application server configured.
- Select the application server you created in the Terminating Application Server, step 4, above.
- Apply the change.
Option 2. MetaView Explorer
- Log in to MetaView Explorer for the MetaView Server managing your CFS.
- Find the subscriber (for example using the Find Subscriber Lines menu option and searching the directory number; or by drilling down in the object tree).
- Navigate to the child Application Servers object.
- Look under the Terminating Service sub-heading.
- Confirm that currently Subscribed is set to False. If it is already True, this means the subscriber is already using another terminating application server, and they cannot have more than one.
- Set Subscribed as True.
- Select the ClearIP Application Server as the Server.
- Apply the change.
Now you have enabled inbound calls for this subscriber to route to ClearIP before terminating to the subscriber.
Reference: Remote Media Gateway models
- Remote gateway model for MetaView Server version 9.5.30 or higher
//UTF8 begin MediaGatewayModel // Remote Media Gateway Model “TransNexus ClearIP” Category SIP ModelName TransNexus ClearIP Description TransNexus ClearIP ControlProtocol SIP DefaultModel False AlertInfoStringsForDistinctiveRingingHeading Alert-Info strings for Distinctive Ringing NumberFormatsHeading Number formats NumberFormatsCalledNumberFormatInternationalScope NF<INT> NumberFormatsCalledNumberFormatNationalScope NF<INT> NumberFormatsCallingNumberFormatInternationalScope NF<INT> NumberFormatsCallingNumberFormatNationalScope NF<INT> NumberFormatsRedirectNumberFormatInternationalScope NF<INT> NumberFormatsRedirectNumberFormatNationalScope NF<INT> NumberFormatsOverrideAutogeneratedCallerID False SignalingSettingsHeading Signaling settings SupportedHighBandwidthMediaFormats {G.711 u-law} LowBandwidthVoiceCodecsSupportedAsStandard {} SupportedDataCodecs {} AdvancedVoiceCodecsPermitted No VideoCodecsPermitted No MaximumNumberOfVoiceCodecsSupported 5 PacketizationInterval 20 SilenceSuppressionAllowed False MaximumSimultaneousTransactionsOutstanding 300 DigitOverhangTime 250 OverrideToHeaderUserPartOnINVITEs False FixBitsMGCPMeGaCoSIPMSML {Cannot be hub,Simple contexts,No loopback between contexts,Restricted direct media,Cannot play ringback,Cannot control endpoint connectivity,Connections always receive,Cannot report detection of call-type discrimination tones} DynamicFixBitsMGCPMeGaCoSIPMSML {} FixBitsSIP {Include transport parameter in From header,May loop calls back to MetaSwitch,Trust number portability information (npdi),Supports receiving number portability information (npdi),Supports receiving carrier information (cic=XXXX)} FixBitsSIP2 {Supports GETS Resource-Priority header} FixBitsSIP3 {Use calling name from P-Asserted-Identity (if present)} FixBitsSIP4 {} FixBitsSIP5 {} SIPResponseCodeToQ850CauseCodeMappingTable 603,21 SIPResponseCodeForESAFailure 503 SIPResponseCodeForCongestion 500 RingLengthForUseWithICF 4 SupportsNotifysRequestingResynchronization False ReferenceCount 1 UpToDateCount 1 ParameterNamesForLineClassCodeHeading Parameter names for Line Class Code ExportHeading Export StatusHeading Status RequestedStatus Enabled end //MediaGatewayModel - Remote gateway model for MetaView Server version 9.3.20 with maintenance release 29+
//UTF8 begin MediaGatewayModel // Remote Media Gateway Model “TransNexus ClearIP” Category SIP ModelName TransNexus ClearIP Description TransNexus ClearIP ControlProtocol SIP DefaultModel False AlertInfoStringsForDistinctiveRingingHeading Alert-Info strings for Distinctive Ringing NumberFormatsHeading Number formats NumberFormatsOverrideAutogeneratedCallerID False SignalingSettingsHeading Signaling settings SupportedHighBandwidthMediaFormats {G.711 u-law} LowBandwidthVoiceCodecsSupportedAsStandard {} SupportedDataCodecs {} AdvancedVoiceCodecsPermitted No VideoCodecsPermitted No MaximumNumberOfVoiceCodecsSupported 5 PacketizationInterval 20 SilenceSuppressionAllowed False MaximumSimultaneousTransactionsOutstanding 300 DigitOverhangTime 250 OverrideToHeaderUserPartOnINVITEs False FixBitsMGCPMeGaCoSIPMSML {Cannot be hub,Simple contexts,No loopback between contexts,Restricted direct media,Cannot play ringback,Cannot control endpoint connectivity,Connections always receive,Cannot report detection of call-type discrimination tones} DynamicFixBitsMGCPMeGaCoSIPMSML {} FixBitsSIP {Use E164 numbers,Include transport parameter in From header,May loop calls back to MetaSwitch,Trust number portability information (npdi),Supports receiving number portability information (npdi),Supports receiving carrier information (cic=XXXX)} FixBitsSIP2 {Supports GETS Resource-Priority header} FixBitsSIP3 {} FixBitsSIP4 {} SIPResponseCodeToQ850CauseCodeMappingTable 603,21 SIPResponseCodeForESAFailure 503 SIPResponseCodeForCongestion 500 ParameterNamesForLineClassCodeHeading Parameter names for Line Class Code ExportHeading Export StatusHeading Status RequestedStatus Enabled end //MediaGatewayModel