Suggestions to curb access arbitrage
Despite the Access Arbitrage Order, traffic pumping continues to exploit high access charges. Here’s an update on the latest round of suggestions to curb access arbitrage.
The Access Arbitrage Order of 2019 changed the access stimulation definition and rules. Since then, providers engaging in access arbitrage have figured out a way to exploit the rules.
IPES provider loophole
The latest access arbitrage tactic involves IPES (Internet Protocol Enabled Services) providers. Here’s how it works:
Inbound Call Flows for IPES Providers
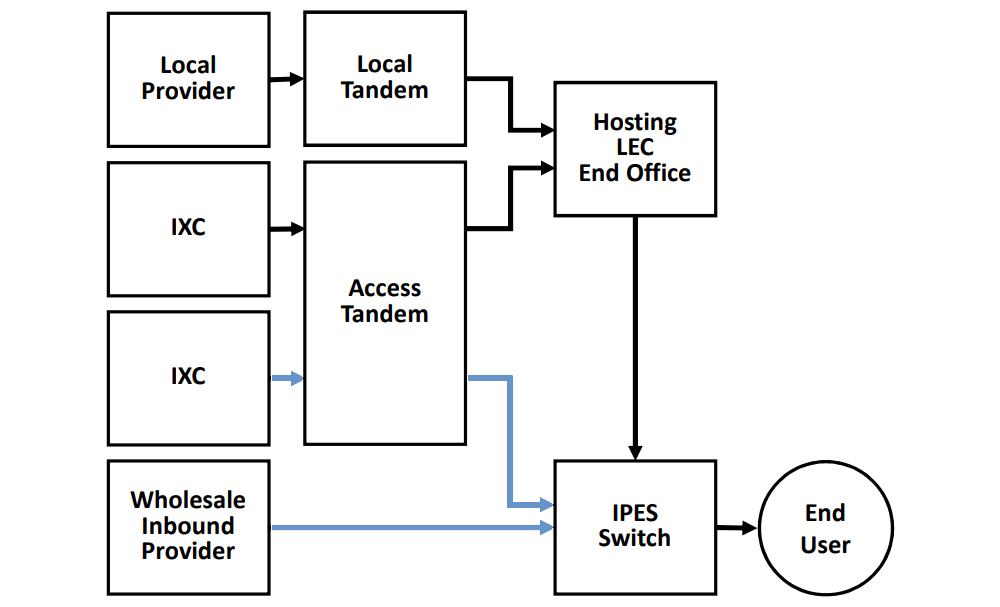
Figure 1. IPES Providers Often Route Most Inbound Calls Direct (Blue Lines). (Image credit: Inteliquent)
Figure 1 illustrates this arrangement. An IPES provider is inserted into the call flow. Under the current rules, they are not required to calculate their traffic ratios. Instead, their traffic is attributed to their Host LEC. Meanwhile, they establish other routes for traffic pumping to avoid the traffic ratio triggers.
Proposed remedy
The Commission proposed further rule changes in July 2022. The FNPRM proposed that access stimulation rules should be applied to IPES providers. They would be required to calculate their traffic ratios and self-identify as an access stimulators if their traffic ratios exceed the limits.
In a recent filing, AT&T wrote that “despite rules requiring carriers to self-identify as access stimulators, many carriers have flatly ignored the rules even though their traffic ratios far exceed the triggers.”
So, what do you do if the access stimulators don’t self-identify?
Latest proposals
AT&T wrote that they use their network data to calculate call traffic ratios for LECs and IPES providers. AT&T urged the Commission to allow IXCs (Inter-Exchange Carriers) to use such calculations to create a “rebuttable presumption” that the LEC or IPES entity is engaging in access stimulation.
AT&T suggests that IXCs would calculate the traffic ratios on an OCN and state level basis. If the ratios exceed the triggers, then the Hosting LEC or IPES provider is presumed to be engaged in access arbitrage.
It’s then up to the Hosting LEC to rebut the IXC’s access stimulation accusation. If the LEC can’t do that, then they are the access stimulator.
Indirect traffic to IPES providers
In some cases, an IPES provider receives traffic indirectly from a LEC, and upstream IXCs can’t calculate traffic ratios. In this case, IXCs would attribute the traffic ratios to the Hosting LEC. If a traffic ratio is triggered, then the Hosting LEC is presumed to be the access stimulator.
The LEC could rebut this allegation by using its data to calculate traffic ratios for the IPES providers it is hosting. This would shift the access stimulation charge against the IPES provider.
So, an IXC would provide calculations that implicate the Hosting LEC, which would rebut the accusation with calculations that implicate the IPES provider.
Would this work? It seems reasonable. At the very least, it would challenge Hosting LECs and IPES providers engaged in access stimulation to explain away the numbers, which would be difficult.

TransNexus solutions
TransNexus is a leader in developing innovative software to manage and protect telecommunications networks. The company has over 20 years’ experience in providing telecom software solutions including toll fraud prevention, robocall mitigation and prevention, TDoS prevention, analytics, routing, billing support, STIR/SHAKEN and SHAKEN certificate services.
Contact us today to learn more.
SIP Analytics® inspects each call before it begins. It’s the fastest, most precise method available to detect and prevent telecom toll fraud.
Learn more about SIP Analytics