Robocaller tried to hack SHAKEN
A voice service provider using ClearIP SHAKEN encountered a batch of inbound robocalls signed with a hacked SHAKEN PASSporT. Here’s what happened, and what we think it means.
This ClearIP customer is a next-generation interconnected VoIP service provider. They are approved by the Policy Administrator as a SHAKEN-authorized voice service provider. They have been authenticating and verifying calls with STIR/SHAKEN in ClearIP since April 2021.
This story unfolds in two episodes:
- The service provider originated a properly signed SHAKEN call on May 31, 2021.
- They received a batch of robocalls on June 25, 2021, 25 days later, that were signed with a hacked SHAKEN PASSporT.
- Most of the hacked PASSporT was identical to the PASSporT they generated for that call they originated on May 31 (see episode 1).
The journey of a hacked SHAKEN PASSporT
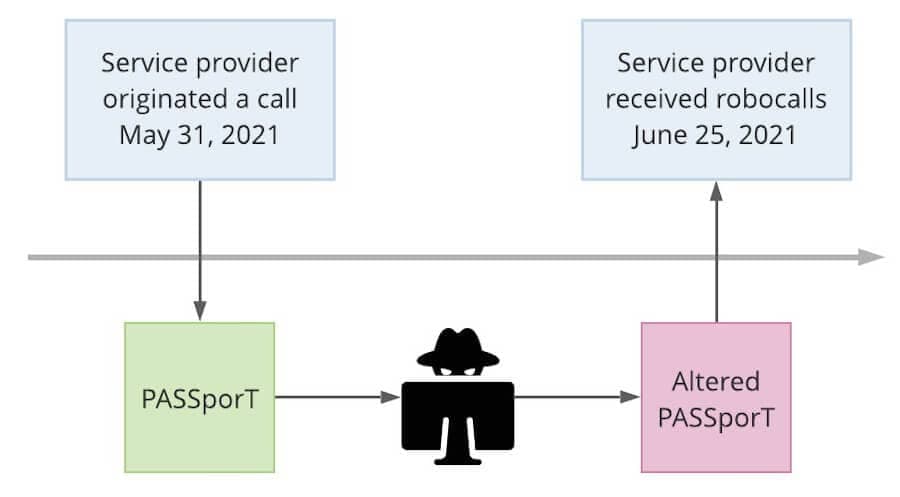
Because these robocalls were signed with SHAKEN PASSporTs, they went through the SHAKEN verification process. They failed.
A TransNexus software engineer happened to be reviewing SHAKEN activity and noticed a series of verification failures. (We keep an eye on these things—see our blog posts on STIR/SHAKEN statistics in March/April 2021 and May 2021).

Upon closer inspection, the engineer found that the exact same malformed PASSporT had been used on several illegal robocalls. Some of these robocalls targeted 8YY numbers. Although the PASSporT was badly malformed, the engineer was able to decode it.
Now it gets interesting:
- The PASSporTs used in these robocalls were identical.
- The attestation level had been changed from full attestation (A) to gateway attestation (C).
- As mentioned above, the remaining information in the hacked PASSporT was identical to a PASSporT this same service provider had generated for a call they originated on May 31. This information did not match the robocalls.
- When the hacked PASSporT was reassembled, the hacker encoded it improperly.
What does this mean?
This was a poor attempt by the hacker. It never stood a chance. SHAKEN did its job.
Why did the robocaller bother with this attempt?
We can’t say for sure, of course, but we know from experience that robocallers and fraudsters are persistent. They keep trying, testing the fences.
Perhaps this was an attempt to check whether SHAKEN deployments are doing what they claim or are merely vaporware. Are SHAKEN service providers really doing all that verification stuff?
Yes, they are.
We don’t know if this is an isolated incident or the start of a trend. Based on our experience, we believe that robocallers may continue testing the fences for a while, then move on to something else.
TransNexus solutions
We offer STIR/SHAKEN and robocall mitigation solutions in our ClearIP and NexOSS software platforms. We can make your STIR/SHAKEN deployment a smooth process.
In addition, we help service providers with all aspects of STIR/SHAKEN deployment, including registering with the Policy Administrator and filing their certification with the FCC.
Contact us today to learn more.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy