Update caller display name for spam calls
Call authentication and analytics can identify potential spam calls. There isn’t yet a standard for display relevant information to the called party, but standards are emerging. Here’s an overview.
First, it’s important to note that call authentication and call analytics work well together. While the FCC orders in response to the TRACED Act don’t require both authentication and analytics, industry observers have encouraged the Commission to reconsider mandating both. The CATA WG best practices document also recommends this.
Therefore, in this blog post, we assume that the originating service provider (OSP) authenticates calls with STIR/SHAKEN, and the terminating service provider (TSP) verifies calls with STIR/SHAKEN and incorporates the results call analytics, a process the STIR/SHAKEN standards refers to as Call Validation Treatment (CVT).

STIR/SHAKEN call authentication and verification
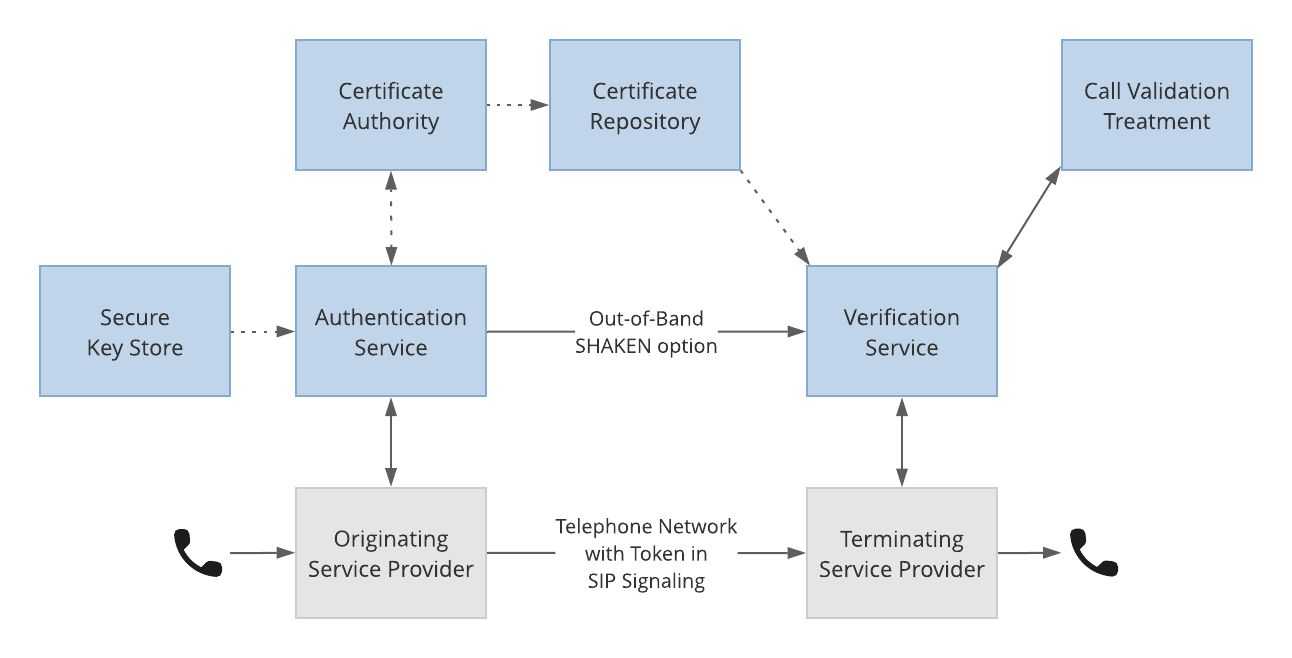
- The OSP authenticates outbound calls and generates a cryptographically signed SHAKEN PASSporT.
- The TSP verifies the signature and caller ID information to determine verification status.
- This result is then used by Call Validation Treatment, or call analytics, as part of its determination of potential spam.
Call analytics
There are a variety of methods that can be used in call analytics, for example:
- Dynamic traffic analysis
- Phone number reputation lookup
- Blacklisting to prevent neighbor-spoofing
- Customer-maintained blacklists
- Shield detection of high-risk and invalid numbers
See our robocall prevention page for more information about these methods.
Update caller name display
At this time, there is not a standard way of displaying the results of call authentication and analytics to the called party. The following table illustrates an approach that’s evolving in the industry and that we have adopted in our software.
The display patterns are based upon the results of three analyses:
- STIR/SHAKEN verification outcome
- Call analytics outcome
- Whether there is a privacy header in the SIP message The following table describes the recommended displays according to results of these analyses:
| SHAKEN outcome | Reputation | Privacy header | Digital display | Character display |
|---|---|---|---|---|
| Verified | Good | No | Caller ID | [V]Caller ID |
| Verified | Good | Yes | Anonymous | [V]Anonymous |
| Verified | Poor | Yes or No | <SPAM> | [V]<SPAM> |
| Failed or no token | Good | No | Caller ID | Caller ID |
| Failed or no token | Good | Yes | Anonymous | Anonymous |
| Failed or no token | Poor | Yes or No | <SPAM> | <SPAM> |
There are a few things worth noting in this table:
- There is a positive indication for successful call authentication.
- Handsets will not support graphical check marks until their firmware is updated, but [V] can be prepended to caller display name.
- Call analytics can label a suspicious call, even if it’s authenticated. There’s nothing to prevent a robocall perpetrator from signing up for numbers and placing calls that will be signed, at least for a while.
- The privacy header is respected.
TransNexus solutions
We offer STIR/SHAKEN and robocall prevention solutions in our ClearIP and NexOSS software platforms. Contact us today to learn more about these solutions.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy