STIR/SHAKEN, least cost routing and attestation
As STIR/SHAKEN becomes used more widely, callers will want their calls authenticated with full attestation, and called parties will be more likely to answer calls with full attestation. There are many arrangements in the telecom ecosystem that will make this difficult. Participants need to understand their options and develop a strategy.
Basic STIR/SHAKEN
STIR/SHAKEN call flow
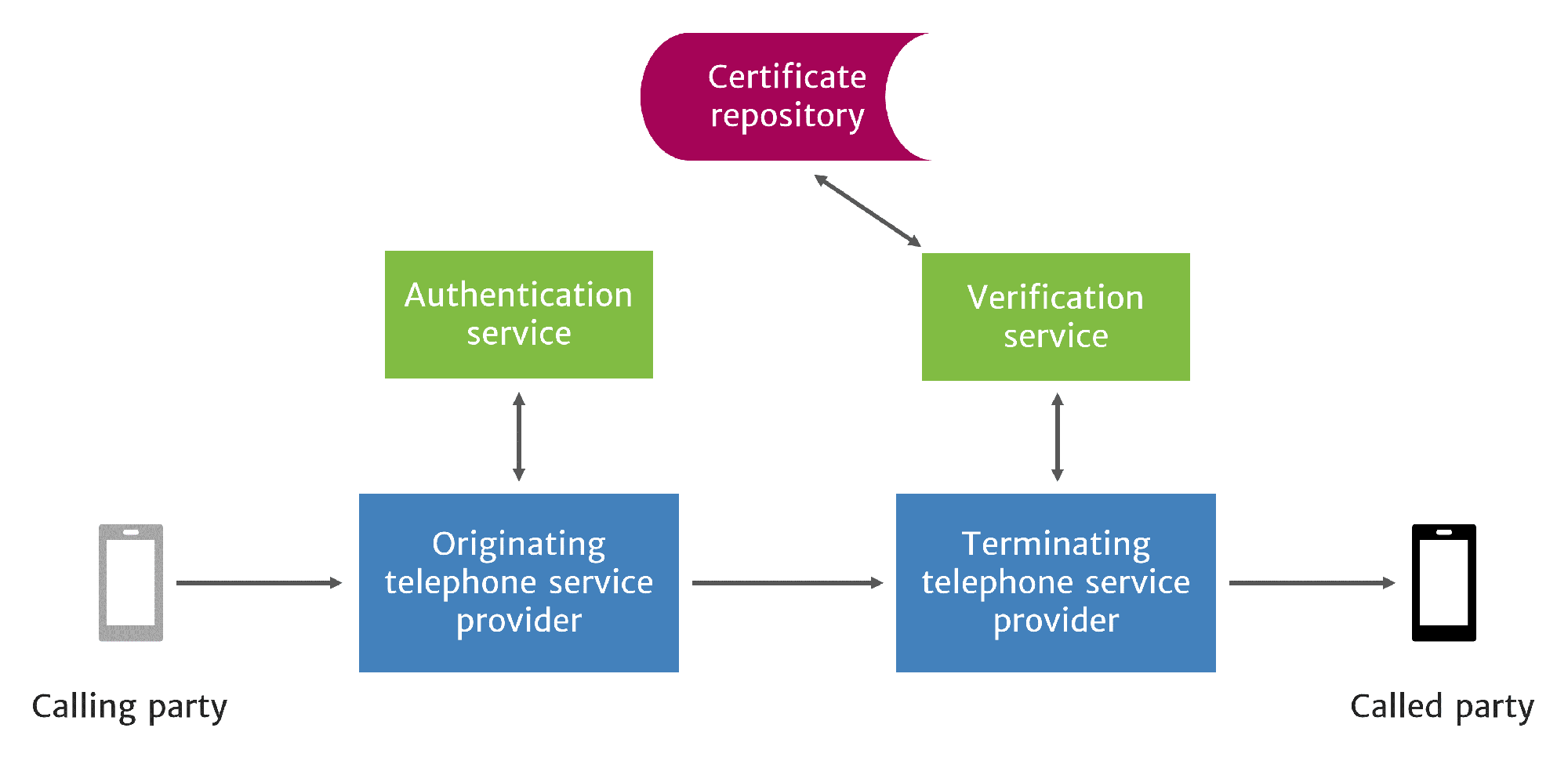
In the simplest use case, the originating service provider (OSP) knows the customer, knows the calling number, and knows that they issued the calling number to the customer. They can authenticate caller ID information with full attestation.
The OSP can use least cost routing to send the call to any trunk. The choice of downstream provider is unrelated to the attestation level placed on the call.
More complex use cases
What happens in more complex use cases, when the OSP doesn’t know the end user and/or doesn’t know whether their use of the calling number is legitimate? There are several more complex enterprise use cases like this:
- Multi-homed enterprise PBX
- Over-the-Top (OTT) PSTN interconnection
- Origination with toll-free calling numbers
- Contact centers that make outbound calls for enterprise customers using their calling numbers.
These situations are more difficult because the OSP often does not know the end user or whether the end user has a legitimate use of the asserted calling number.

Authentication as a service
Some OSPs might offer STIR/SHAKEN authentication as a service. They will use a know-your-customer vetting process offline, in advance, to determine that the end user has a legitimate right to use that calling number. As a result, the OSP might be willing to authenticate such calls with full attestation.
Would that solve the problem?
Perhaps. But does the end user, or the enterprise or call center representing the end user, have to send all their outbound calls to the same OSP for authentication?
What would that mean for routing costs?
Least cost routing
Enterprise callers, interconnected VoIP service providers and OTT providers often like to negotiate rates with several providers. Competition among downstream providers helps these businesses find the best rates.
If these organizations must send all their calls through just one downstream provider, the loss of least cost routing benefits would likely drive up their routing costs.
As you can see from these examples, there can be a tension between the goals of achieving full attestation and least cost routing. Here are some ways that such callers might get the best of both worlds.
Three potential solutions
ATIS and the SIP Forum have published a Study of Full Attestation Alternatives for Enterprises and Business Entities with Multi-Homing and Other Arrangements. This study identified three alternative methods for enterprise callers to achieve full attestation with least cost routing:
- Delegate certificates
- Telephone number letter of authorization exchange
- Central telephone number database
Delegate certificates
We have described delegate certificates more thoroughly in a whitepaper. The essential feature of delegate certificates is that the process enables a telephone number service provider to issue a delegate certificate to a VoiP entity.
Delegate certificates extend chain of trust
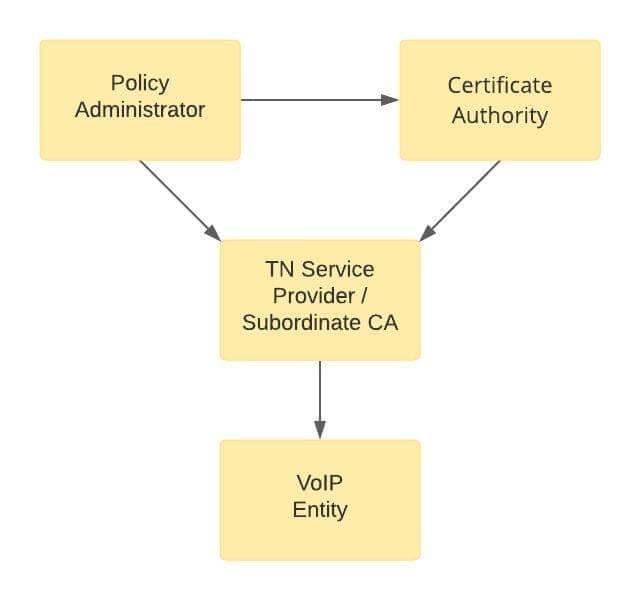
With delegate certificates:
- The TN provider issues a delegate certificate to the VoIP Entity to cover the number(s) issued.
- The VoIP Entity creates a base PASSporT signed with the delegate certificate.
- The OSP has two options:
- Verify the base PASSporT with the delegate certificate and use that as justification to create a SHAKEN PASSporT with full authentication.
- Leave the signed base PASSporT in the call.
- The terminating service provider would verify the STIR/SHAKEN information using the STIR/SHAKEN information provided with the call.
Advantages: Extends the certificate chain of trust using PKI methods
Disadvantages: Uncertain whether all providers will participate
TN Letter of Authorization
With this approach, letters of authorization would be exchanged as an administrative procedure offline, in advance of call traffic. OSPs would use these letters as justification for attestation.
Advantages: Low-tech approach
Disadvantages: Administrative burden
Central TN Database
With this approach, a central authority maintains a database where TN number providers send information about numbers they’ve issued. Relying parties would query the database to determine attestation.
Advantages: No stacking of identity headers is required and there are no precedence/interop issues
Disadvantages: Doesn’t use PKI, so spoofing is possible.
TransNexus solutions
We offer STIR/SHAKEN and robocall prevention solutions in our ClearIP and NexOSS software platforms. Contact us today to learn more about these solutions.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy