Case study of a $15,000 telecom fraud loss
Telecom fraud management systems that rely on CDR analysis can allow thousands of dollars in fraud losses even when they work properly. The problem is simple: CDR analysis is too slow.
Fraud analysis cannot begin until CDRs for the first fraudulent calls are collected. Hackers can generate hundreds of fraudulent calls in an attack before the first call ends. Thousands of dollars of fraudulent calls will already be in progress when the first fraud alarm sounds.
This case study describes a fraud attack on a service provider whose fraud management system (FMS) detected fraudulent calls and sent alerts exactly as expected. There was no breakdown in technology or business processes. Nevertheless, the FMS that used CDR analysis for fraud detection allowed over fifteen thousand dollars in toll fraud.
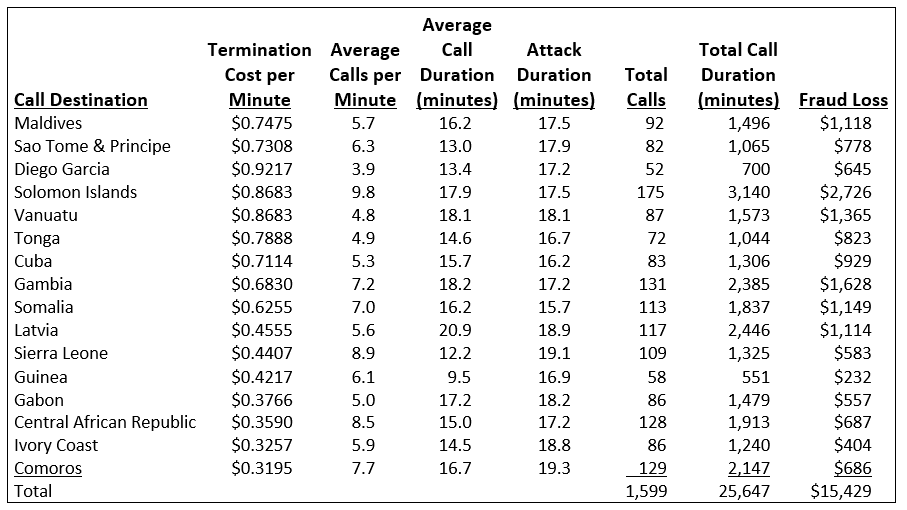
The attack began at approximately 1:00 am on a Saturday morning. A customer’s PBX had been hacked and was pumping traffic to a high cost number in the Maldives. During the initial attack, the hacker generated an average of 5.7 calls per minute. The average duration for each fraudulent call was 16.2 minutes.
The FMS detected the attack as soon as the first CDRs were reported and began blocking calls to the Maldives 17.5 minutes after the attack began. However, the FMS was too late to prevent 92 fraudulent calls already in progress and a fraud loss of $1,118.
Unfortunately, this was not the end of the attack.
Shortly after calls to the Maldives were blocked, the hacker continued his attack with calls to Sao Tome and Principe. The FMS detected and blocked fraudulent calls to Sao Tome and Principe, but was too slow to prevent an additional loss of $778.
This process continued all weekend. The hacker would pump calls to a high cost destination. The FMS would detect the fraudulent calls and block the route. The hacker would pump calls to a different number.
The cycle was stopped on Monday morning when the service provider helped its customer to identify and fix the breach in their PBX. The fraudster was able to generate over $15,000 in fraudulent calls before the PBX breach was fixed. The table below provides details of the fraud attack and losses.
Fraud analysis before call setup eliminates the fraud leakage that is inevitable with post-call analysis of CDRs. TransNexus SIP Analytics detects the start of a fraud attack by analyzing each SIP Invite before call set-up.
Contact TransNexus today to learn how SIP Analytics will reduce your fraud losses.