Telecom fraud prevention guide
Detecting and preventing telecom fraud
According to the Federal Trade Commission, telecom fraud continues to account for more fraud complaints each year. New technology has led to an onslaught of new telecom fraud tactics. The latest schemes are difficult to track and investigate because of their frequency, layers of anonymity and global nature.
This guide will help you learn about the different types of telecom fraud and industry best practices for detection and prevention.
Three major categories of telecom fraud
We will divide the many telecom fraud schemes into three broad categories, based on whom the fraudsters are targeting. These categories are:
- Schemes to defraud telecom service providers. These schemes are the most complicated, and exploit telecom service providers using stimulated traffic, SIP trunking, regulatory loopholes, and more.
- Schemes to defraud subscribers. This is simply any scheme that involves gaining access to someone else’s account to make free phone calls.
- Schemes conducted over the telephone. Also known as phone fraud, this category covers all types of general fraud that are perpetrated over the telephone.
1. Schemes to defraud telecom service providers
Telecom Service Providers are particularly vulnerable to telecom fraud. Fraudsters are able to manipulate telecom regulatory systems to their advantage, and to the disadvantage of the service provider, in ways that are difficult to detect, trace, and prosecute. Fraudsters often take advantage of lax security practices of a service provider’s customers. A customer whose network has been compromised will often refuse to pay large fraudulent charges, leaving the service provider to cover the bill. Finally, attacks frequently happen over holidays and weekends, when networks are often monitored less closely.
The industry best practice for detecting and preventing this type of telecom fraud is to monitor calls in real time for suspicious traffic or call patterns. To truly shut down fraud, any fraud prevention system should be combined with call routing technology. ClearIP and NexOSS, from TransNexus, combine fraud detection with routing. This means that when suspicious traffic is identified, the TransNexus platforms will automatically change the outgoing calling plans to block or re-route dangerous traffic, stopping the fraudulent activity before it gets started.
Call transfer fraud
One type of telecom fraud that has been a particular issue for soft switch users is call transfer fraud. In this scenario, the fraudster hacks into a PBX and uses that PBX’s services to make free long distance calls. By instructing the compromised PBX to transfer the call to the hacker’s own phone service, subscribers to the fraudster’s phone service can speak to their international destinations through the hacked soft switch, and the soft switch operator cannot bill the hacker’s subscriber. Those familiar with three-way calling will recognize the inspiration for call transfer fraud.
Call transfer fraud scenario
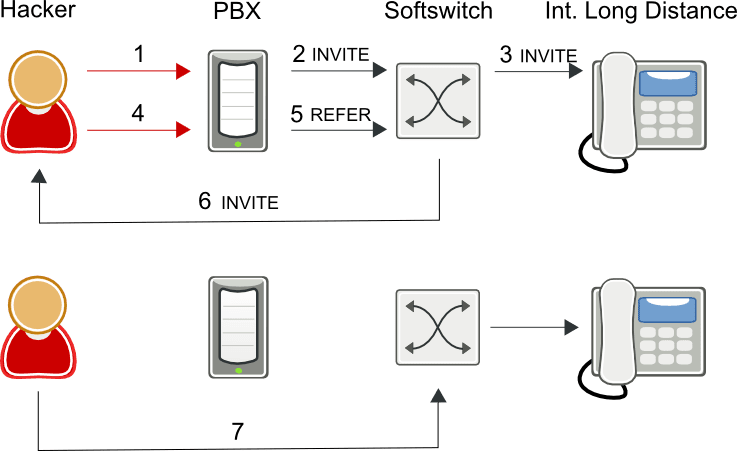
- Hacker phone service hacks unsuspecting PBX to make a call to make international calls
- PBX sends SIP INVITE to soft switch
- Softswitch routes call to international carrier
- Hacker instructs PBX to blind transfer call to hacker phone service
- PBX sends SIP REFER to soft switch to blind transfer call to hacker phone service
- Soft switch sends SIP INVITE to hacker phone service
- Hacker’s subscriber speaks to international destination through soft switch
Most soft switches have no way of tracking a call once it is transferred out of the network, so fraudsters can generate a significant amount of traffic and revenue for themselves before being caught.
False answer supervision
When a dialed phone number is not in service, the calling party will hear a brief recording telling them the number is no longer in service. There is no answer supervision or connection between the calling and called party. Since the call never connects, it is an incomplete call and should not be billed.
However, fraudsters use false answer supervision to make these calls appear as completed calls which may be billed. Perhaps the fraudster has published rates for terminating calls without any intention of actually completing the calls. Here, service providers will route calls through the fraudster, who, instead of terminating the call, will play a not in service message and then bill the service provider for more than 10 seconds of calling. This type of fraud hurts the originating service provider both by costing money, and by hurting their reputation.
The key indicators of this type of fraud are:
- Short phone calls
- Calling party hangs up nearly 100% of the time
- High answer seizure ratio
False answer supervision fraud call scenario
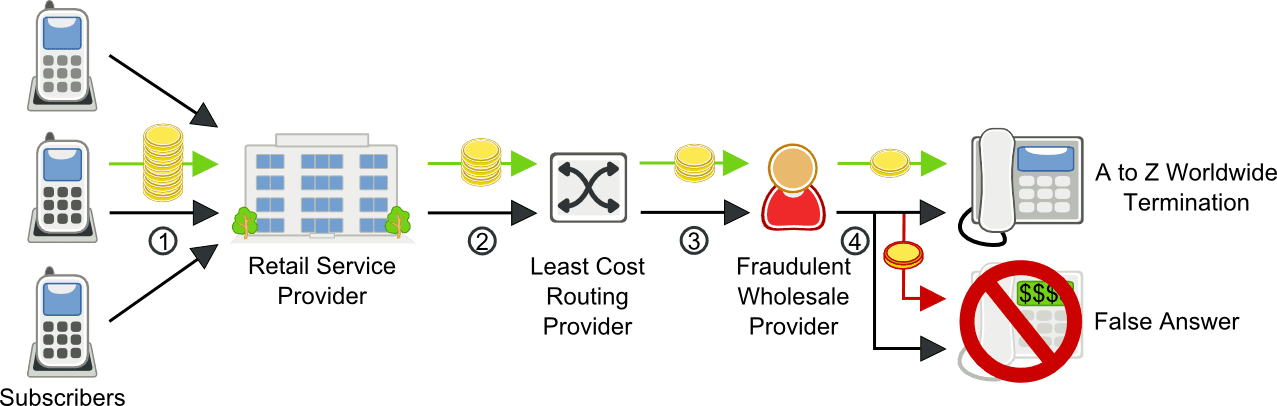
- Subscriber makes a call
- Service provider routes call to its wholesale least-cost-routing provider
- The wholesale customer routes the call to a wholesale provider who has been chosen for its exceptionally good rates to certain high-cost destinations
- In most cases, the wholesale provider completes the call, but in some cases, the wholesale provider routes calls to the high cost destination with a false answer — charging for a completed call without ever trying to complete it.
Location routing number fraud
Location Routing Number (LRN) fraud works based on the desire of some service providers to avoid extra charges from LRN dips. Most providers will run an LRN dip to determine the correct LRN for a dialed number. However, many service providers will not perform an LRN dip if the LRN is already in the SIP message.
Fraudsters take advantage of this by inserting fake LRNs into their calls. For example, they may insert the LRN for a relatively cheap terminating destination, when the call is actually going to a high cost rural destination. The service provider will then bill the fraudster for the cheaper call, but will have to eat the cost of the expensive rural call. In some cases, this can be up to five times the price they billed the fraudster.
Location Routing Number Fraud Call Scenario
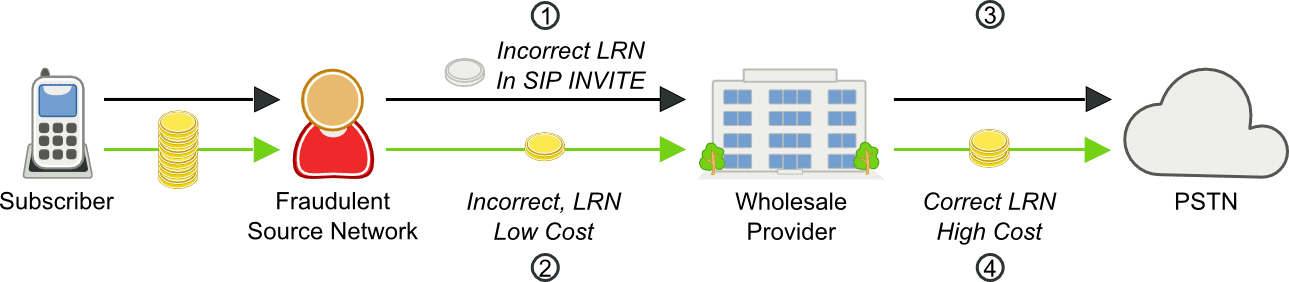
- Source network sends a call to a wholesale provider with an incorrect low cost LRN in the SIP INVITE
- Provider charges the source network for a call to the incorrect LRN
- The provider completes the call
- The correct LRN for the call is more expensive than expected. The provider loses money, and the source network gets below-cost termination
Revenue sharing fraud
Revenue share fraudulent activities are those which abuse carrier interconnect agreements. Cooperation is the key to this type of fraud. The fraudster’s goal is to pair up with a destination that can charge high rates, and then inflate traffic to his numbers at little or no cost to himself.
These types of schemes can occur within a country, or across international borders. Though they may not be technically illegal, they are often also paired with PBX hacking or other forms of fraud that generate illegal and artificial traffic.
How to detect revenue sharing fraud
The typical call signature for revenue sharing fraud is a spike in traffic to high-cost destinations. Because these spikes often occur over holidays or weekends, service providers must have a monitoring and alarm system in place that will stop the fraud immediately.
TransNexus software solutions monitor calls in real time. They look at five-minute samples of call attempts for suspicious spikes. When a spike occurs, the software will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions may be configured to re-route or block calls or to change the outgoing dial plan of subscribers who may have been compromised.
Multiple transfer fraud
Multiple call transfers are a sophisticated technique for amplifying International Revenue Sharing Fraud while making the fraud more difficult to detect.
Multiple call transfer fraud scenario
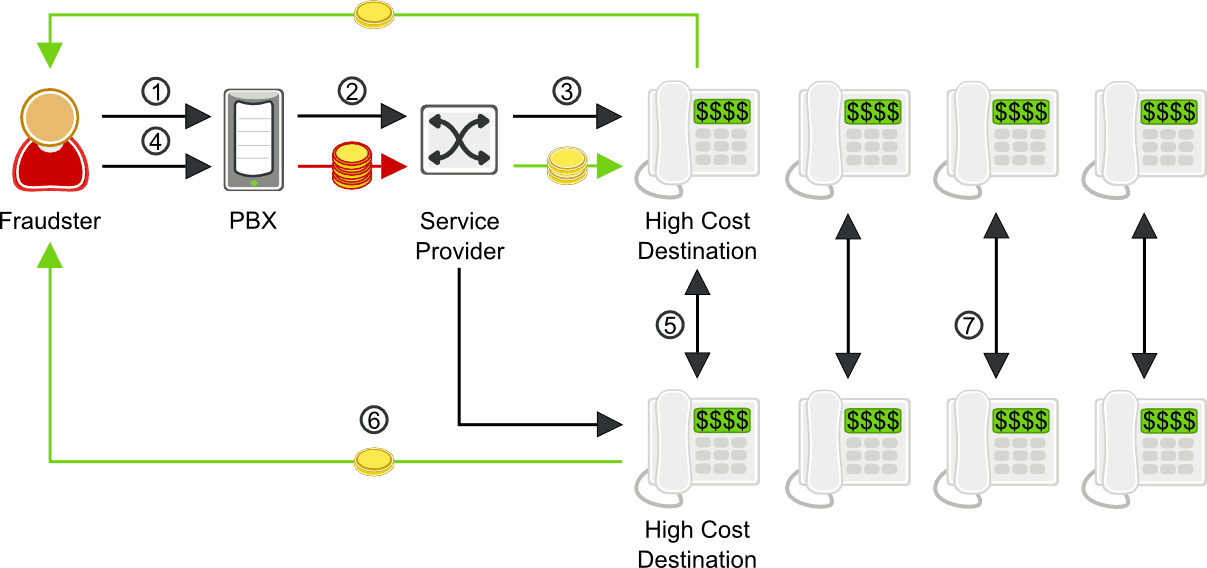
- Fraudster phone service hacks an enterprise PBX to make calls to high cost destinations
- PBX sends SIP INVITE to service provider’s soft switch
- Service provider routes call to high-cost destination
- Fraudster instructs PBX to transfer call to another high-cost destination
- The fraudster hangs up. The call between the two high cost destinations remains in place.
- Fraudster shares in the revenue from the fraudulent calls.
- Fraudster repeats steps 2-6 to set up hundreds or thousands of simultaneous calls
Once the calls are transferred, they stay up until the carrier shuts it down. Some customers have reported calls staying up for over 24 hours. On many platforms transferred calls don’t count against concurrent calls, and most switches won’t cut a call record until the call is over. If the criminal is clever, he will transfer dozens or hundreds of calls concurrently. They are pinned in the network, and can go unnoticed until it is too late.
How to detect multiple call transfer fraud
The typical call signature for any type of IRSF is a spike in traffic to high cost destinations. Because these spikes often occur over holidays or weekends, service providers must have a monitoring and alarm system in place that will stop the fraud immediately.
TransNexus software solutions monitor calls in real time. They look at five minute samples of call attempts for suspicious spikes. When a spike occurs, the software will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
Call forwarding fraud
The call forwarding hack is a more sophisticated form of VoIP telecom fraud. In this case, fraudsters are hacking through the user access web portal of an enterprise PBX. By guessing a user’s password, they can login to a PBX, and configure call forwarding to an expensive long distance destination to profit from IRSF. Then the hacker will call the telephone number of the hacked account which forwards the call for IRSF.
Call forwarding fraud scenario
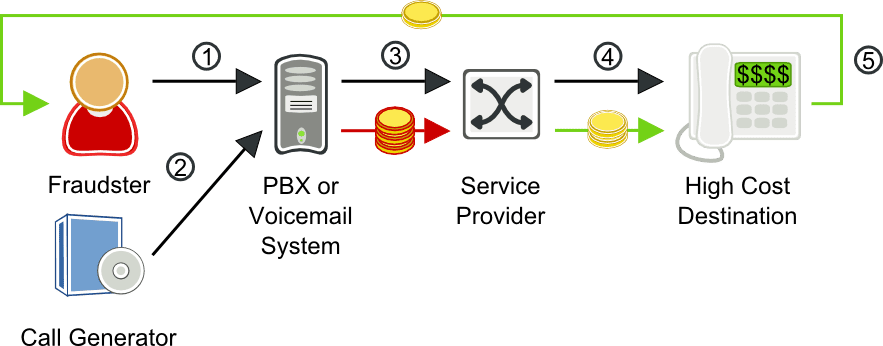
- Fraudster accesses the web interface of a PBX or IVR of a voice mail system, compromises a user’s login and password, and sets the user’s account to forward calls to a high cost destination.
- Fraudster calls the compromised number over either the PSTN or VoIP.
- Compromised PBX forwards the call to the service provider’s soft switch.
- The service provider switch forwards the call to the high-cost destination. The service provider must pay to complete the fraudulent calls, but rarely receives payment from the enterprise with the compromised PBX.
- The fraudster shares in the revenue from the fraudulent calls.
How to detect call forwarding fraud
The typical call signature for any type of IRSF is a spike in traffic to high cost destinations. Because these spikes often occur over holidays or weekends, service providers must have a monitoring and alarm system in place that will stop the fraud immediately.
TransNexus software solutions monitor calls in real time. They look at five minute samples of call attempts for suspicious spikes. When a spike occurs, the solutions will send Email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
International NANPA fraud
The NANPA (North American Numbering Plan Administration) lists numbers within the United States and international numbers in North America, the Caribbean, and US territories. Many switches do not consider numbers listed in NANPA as international, even though some are offshore. This leaves subscribers vulnerable to International Revenue Share Fraud (IRSF) because they cannot block calls to certain offshore high-fraud destinations, such as in the Caribbean, for example.
For organizations who cannot block offshore numbers listed in NANPA or the LERG, TranNexus solutions offer a solution. TransNexus software solutions monitor calls in real time. They look at five minute samples of call attempts for suspicious spikes. When a spike occurs, the solutions will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
International revenue sharing fraud (IRSF)
International Revenue Sharing Fraud (IRSF) is, without a doubt, the most damaging and most prevalent VoIP telecom fraud scenario. Revenue share fraudulent activities abuse carrier interconnect agreements. The fraudster partners with a local carrier that charges high rates for call termination and agrees to share revenue for any traffic generated by the fraudster. Common destinations for these calls include West African countries, UK mobile numbers and satellite phones.
IRSF is characterized by large amounts of calls, often with long duration, to a single destination. While it is not difficult to detect IRSF by examining Call Detail Records (CDRs), by the time you collect the CDRs, the damage has been done.
“IRSF is the most common form of fraud we see,” said Ryan Delgrosso, CTO of Phone Power. “The international carrier that delivers the last mile is obligated for paying the final destination telco. They charge the carrier that sent them the call, and the cost flows downhill until you get to the access point that was compromised. Further complicating matters, these schemes always cross international boundaries, making pursuit from a criminal perspective almost impossible. Access or retail service providers usually end up eating the costs.”
The first step for a potential VoIP fraudster is gaining illegal access to your network. As with any large network, it is difficult to protect every access point to a VoIP network. This is especially true for retail service providers whose customers access the service provider’s network over the internet using a wide range of different access devices. Residential or small business customers access the service provider network using analog telephone adaptors (ATAs) that may be easily compromised. Larger enterprises may access the service provider’s network over a SIP trunk connected to a Private Branch eXchange (PBX), which aggregates traffic from hundreds of SIP phones. Many of the SIP phones may be on the public Internet and completely removed from any security precautions that could be enforced the enterprise or service provider. In addition, lax PBX security precautions can make PBX hacking a simple task.
The typical call signature for revenue sharing fraud is a spike in traffic to high cost destinations. Because these spikes often occur over holidays or weekends, service providers must have a monitoring and alarm system in place that will stop the fraud immediately. TransNexus solutions monitor calls in real time. They look at five-minute samples of call attempts for suspicious spikes. When a spike occurs, the solutions will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
Traffic pumping
Because of telephone regulations, long-distance carriers must pay access fees to local exchange carriers for calls to those carriers’ local subscribers. Rural carriers may charge substantially higher access fees than urban carriers. In order to increase their incoming call volume and revenue, some rural carriers partner with telephone service providers to route their calls through the rural carrier. These often include phone sex or free conference call providers, who expect a high volume of incoming calls. A similar scenario occurs internationally, with fraudsters setting up conference servers in third world countries and making deals with the local (often state-owned) telephone company.
To qualify as access stimulation or traffic pumping, a fraudster must:
- Have a revenue share agreement between the terminating carrier and the fraudster who stimulates demand
- Have a 3-to-1 increase in interstate terminating to originating traffic, or 100% traffic growth in a month year-over-year.
In this case, authorities can step in and force the terminating carrier to re-file their access tariff with the public utilities commission within 45 days. Because of the extra traffic, the terminating carrier would no longer be eligible for the high access fee, and will likely be dropped from the revenue sharing agreement.
The typical call signature for traffic pumping fraud is a spike in traffic to high cost destinations. TransNexus solutions monitor calls in real time. They look at five minute samples of call attempts for suspicious spikes. When a spike occurs, the solutions will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
Voicemail hacking fraud
Voicemail hacking was an early form of communications fraud. It can happen simply and easily through the telephone network. It is a problem rampant enough that even the FCC has recently issued guidelines on how to avoid becoming a victim. Here, a hacker need only find a device with an easy-to-break password. Some voice mail systems have static or easily guessed default passwords, and users often do not change the default. Recent studies have shown that the password 1-2-3-4 constitutes nearly 5% of Voice Mail passwords, seven times the frequency of the next most common password (0-0-0-0).
Criminals can easily use this straightforward technique for International Revenue Sharing Fraud (IRSF). Once they have the password to an account, it is a simple matter in many voicemail systems to exploit the callback feature, which allows a user to immediately return a missed call. The criminal calls the phone number, leaving their IRSF number as the callback number. Then they login to the account, find their missed call and return it, signaling the voicemail to initiate a call to their IRSF number. Once the call is connected, a criminal can attempt to leave it up as long as possible, often hours or days.
The typical call signature for any type of IRSF is a spike in traffic to high-cost destinations. Because these spikes often occur over holidays or weekends, service providers must have a monitoring and alarm system in place that will stop the fraud immediately. TransNexus solutions monitor calls in real time. They look at five minute samples of call attempts for suspicious spikes. When a spike occurs, the solutions will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
Wangiri fraud
Wangiri, in Japanese, means “one and cut.” That is, one ring and a cut off phone call. A Wangiri phone fraud scheme relies on this single ring method for a quick way to make money. A fraudster will set up a computer to dial a large number of phone numbers at random. Each rings just once, then hangs up. This leaves a number as a missed call on the recipients’ phone. Users often see the missed call and believe a legitimate call was cut off, or are simply curious as to who called, so they dial the missed number. The number turns out to be a premium rate number — anything from advertising to “free prizes” to sex services.
There is also an SMS variant of Wangiri fraud that has been reported recently. In this variation, subscribers receive an SMS message like “Please call me back, this is urgent!” as a way to entice them to return a call.
Wangiri fraud scenario
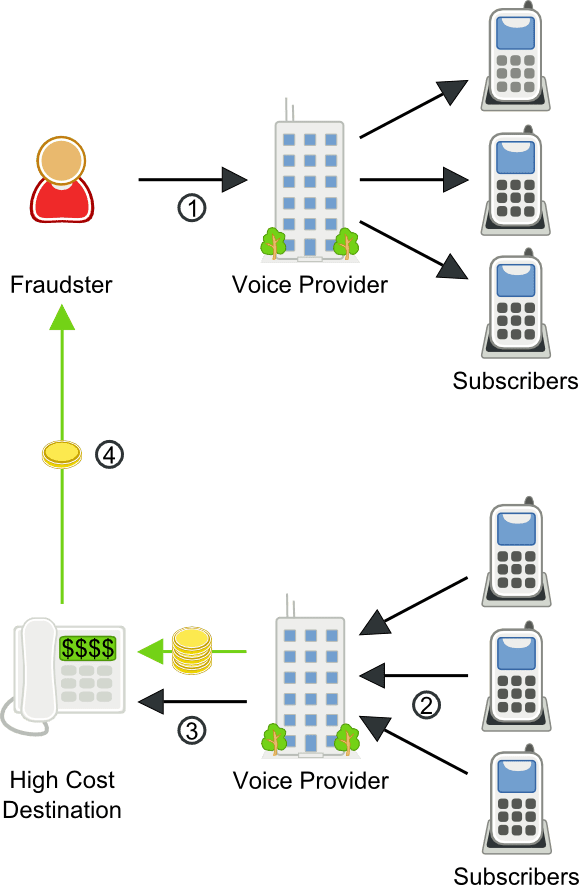
- The Fraudster sets up calls to voice subscribers, but hangs up after one ring. This means that the fraudster isn’t charged for making the calls.
- Curious subscribers see a missed call on their phones, and return the call, not realizing that the number is actually a high-cost destination.
- If subscribers are on a flat-rate plan, the service provider will be left paying high termination costs with no corresponding increase in revenue.
- The Fraudster shares in the revenue from the fraudulent calls.
The typical call signature for Wangiri fraud is a spike in traffic to high-cost destinations. TransNexus solutions monitor calls in real time. They look at five minute samples of call attempts for suspicious spikes. When a spike occurs, the solutions will send email and SNMP fraud alerts. In addition to the alarms, TransNexus solutions can be configured to re-route or block calls or to change outgoing dial plans of subscribers who may have been compromised.
Toll bypass fraud
Bypass fraud is the unauthorized insertion of traffic onto another carrier’s network. You may also find this type of fraud referred to as Interconnect fraud, GSM Gateway fraud, or SIM Boxing. This scenario requires that the fraudsters have access to advanced technology, which is capable of making international calls appear to be cheaper, domestic calls, effectively bypassing the normal payment system for international calling. The fraudsters will typically sell long distance calling cards overseas. When customers call the number on the cards, operators are able to switch the call to make it seem like a domestic call.
Toll bypass fraud scenario
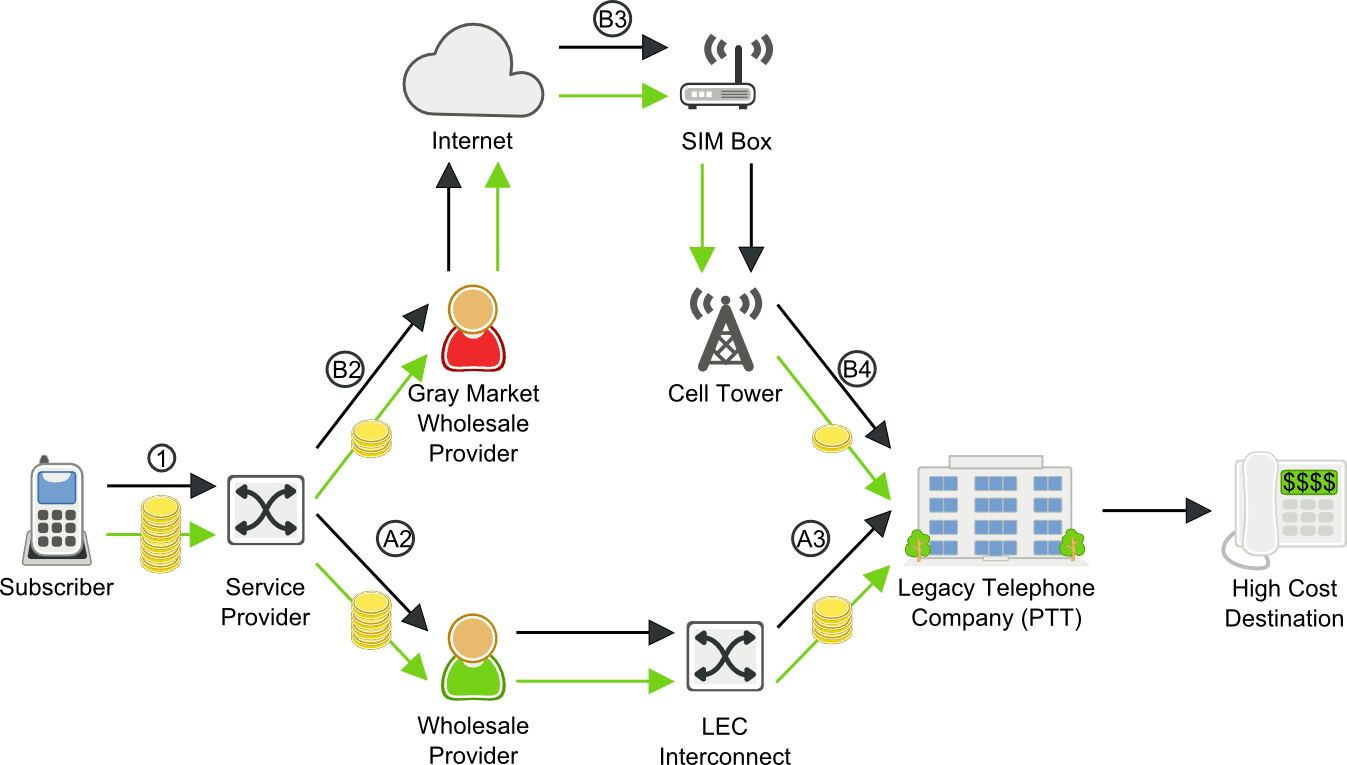
- Service provider has the choice to route a subscriber’s call to a more expensive wholesale provider (A) or a lower-cost gray-market provider (B)
- A2. Service provider routes call to wholesale provider
- A3. Wholesale provider pays a toll to the international Legacy Telephone Company (PTT)
- B2. Service provider routes call to a lower cost fraudulent wholesale provider
- B3. The fraudulent wholesale provider routes the call through a SIM Box
- B4. The international call routed through the SIM Box to a cell tower looks like local subscriber traffic, so the fraudulent service provider pays a significantly reduced toll.
Inter/intra state toll bypass fraud
Bypass fraud is the unauthorized insertion of traffic onto another carrier’s network. Inter/Intra State toll bypass fraud attempts to bypass the higher tolls of inter-state traffic by making it look like intra-state traffic.
Inter/intra state toll bypass fraud scenario
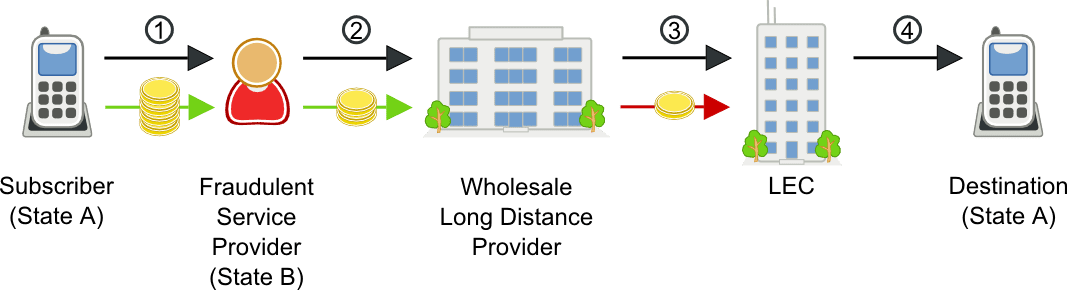
- Subscriber places an intra-state call
- Fraudulent service provider changes the calling number of the call so that it appears to be a less expensive inter-state call
- Wholesale long distance provider routes call to the LEC as an inter-state call
- LEC completes the more expensive intra-state call, but charges for a less expensive inter-state call
Toll free fraud
Toll free fraud can affect any business that uses a toll free number. In this scheme, a fraudster will typically make a profit-sharing agreement with a CLEC. He will then use VoIP technology to make multiple calls to a toll free number—often that of a large corporation. The CLEC will perform a dip to the SMS 800 database, and then transfer the call to another network for termination, earning something like 1.5 cents per minute in switched originating access fees.
The fraudster will then navigate the automated IVR prompts, avoiding connecting to a live operator. These calls are often left up for hours at a time and automated so multiple calls will be made at once. When large companies, like financial institutions, are targeted, they frequently don’t even notice the huge charges racked up by toll free fraud, even though they are expensive, long calls.
Toll free fraud scenario
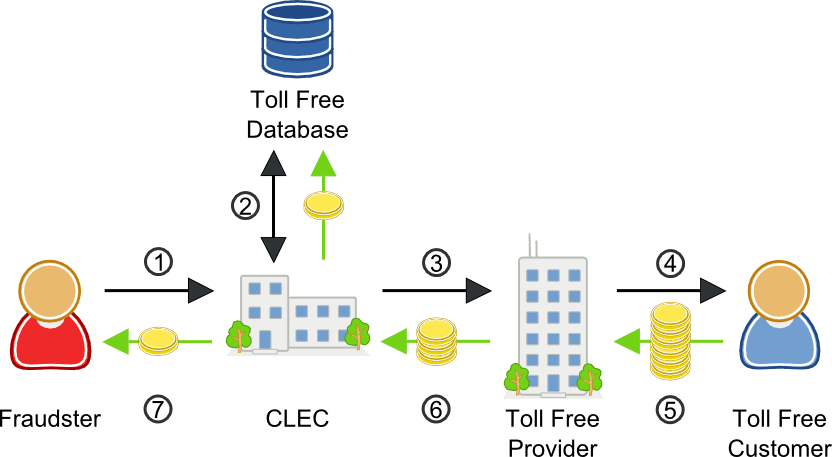
- Fraudster makes calls to toll free customer
- CLEC pays for a toll free database dip
- CLEC routes the call to the designated toll free provider
- Toll free provider completes the call to the toll free customer
- Toll free customer pays the provider the service fee
- Toll free provider pays the originating access fee to the CLEC
- The CLEC makes a profit sharing payment to the fraudster
Wholesale SIP trunking fraud
Fraudulent wholesale trunking is a relatively new phenomenon, but one that is growing in popularity and difficult to detect. In this scenario, the fraudster is actually making money by selling wholesale trunking services, using stolen credentials to terminate the calls. The key calling signature for this type of fraud is a huge number of apparently random calls. The destinations are not particularly high cost, but neither are they cheap. Countries like Vietnam, Laos, and other middle-priced Asian countries show up often. The traffic often appears to be to residential numbers.
Subscribers have reported tracing this type of fraudulent traffic coming from prepaid calling card companies operating a VoIP platform in an offshore facility. Prepaid calling services are well suited to exploit this type of fraud since there are no calling numbers linked to customers. The IP address of the prepaid calling platform is the only link to trace the fraudster.
Unfortunately, geolocation cannot always be used to identify the fraudster. These services can be offered via a tunnel through the internet that hides the true IP address of the fraudster. The public IP address of the fraudster’s calling platform could be the IP address of a hosted Virtual Private Network (VPN) service while the actual prepaid calling platform is located in a different part of the world.
Wholesale SIP Trunking Fraud Scenario
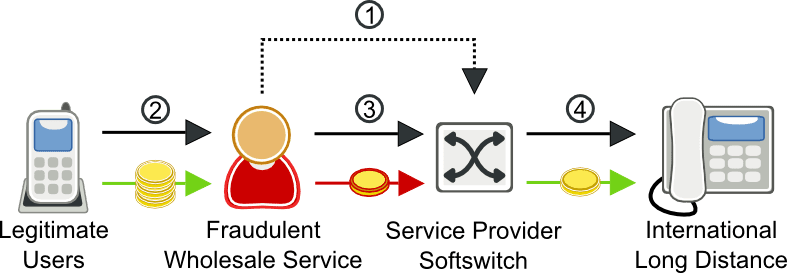
- Fraudster steals subscriber’s credentials
- Fraudster’s soft switch registers with service provider’s soft switch using stolen user name and password
- Legitimate user places a call
- Fraudster sends INVITE to service provider’s soft switch
- Soft switch routes call to international long distance destination
Wholesale SIP trunking fraud is often difficult to detect because the call patterns look similar to normal subscriber usage. For these types of fraud events, we have found that a 60 minute sample of call duration data by call source provides the best detection. By tracking the fraud score for call duration, TransNexus software solutions effectively monitor the spend rate of each call source.
2. Schemes to defraud subscribers
Subscriber fraud can affect any phone owner. It encompasses any fraud that involves using another person’s account to make free phone calls. Subscriber fraud may be as simple as using a lost or stolen phone or SIM card. The best way to combat subscriber fraud is to educate subscribers on basic security best practices, including creating and protecting strong passwords, and carefully examining bills for unrecognized calling activity.
Calling card fraud
Calling card fraud can happens in a number of ways. Fraudsters might call subscribers and pose as a service provider representative, and then ask for calling card numbers for verification purposes. Another common scenario is that someone watches or listens as the subscriber punch in or read their calling card number at a payphone. Subscribers should be aware of anyone calling to request calling card verification. They should only give out their card number when placing a call through an operator. Subscribers must also be careful that no one is watching when they key in their card PIN or any other PIN.
Lost or stolen phones and SIM card fraud
If a criminal gains access to a subscriber’s lost or stolen phone, he will be able to gain unauthorized access to the subscriber’s network. Once recognized as a bona fide customer, fraudsters then have access to a network and are able to carry out revenue generating schemes that can seriously damage reputation and bottom-line profits.
The true impact of subscription fraud often goes unrecognized because providers mistake it for bad debt. Subscribers should report lost or stolen equipment immediately to their service provider. Service providers can often add the lost device to the national list for lost or stolen mobile devices so that it cannot be used on their own or other service provider’s networks.
3. Schemes conducted over the telephone
Criminals of all sorts use telephony as a tool to defraud consumers and businesses. Phone fraud is a huge category, and can cover anything from Nigerian prince style scams to identity theft to extortion. TransNexus does not offer a solution to protect against these types of fraud, though there are other solutions on the market that can.
Account takeover
With this type of telecom fraud, the fraudster generally attacks something like a financial institution. Fraudsters will call financial institutions and maliciously impersonate another customer in order to steal the contents of an account. Pindrop Security estimates that a financial institution taking 50,000 calls per day will lose over $10 million per year to phone fraud losses.
It is not easy to distinguish between legitimate callers and phone fraud. One way is by using phone printing technology to analyze the audio content of a phone call. Pindrop Security offers solutions that measure certain characteristics of the audio signal to form a unique fingerprint for each call. In addition, they can identify the region the call originated from and determine if the call was from a landline, cell phone or specific VoIP provider. These pieces of information provide an high levels of insight into caller behavior.
Phone printing routinely identifies over 80% of inbound fraud calls to enterprise contact centers, saving millions of dollars in losses and contact center expenses a year.
Telecom denial-of-service (TDOS)
Telecom denial-of-service (TDoS) attacks are similar to traditional data network denial of service (DDoS) attacks. In a DDoS attack, unauthorized users flood a system with too many access requests, preventing legitimate users from accessing the network. For TDoS, fraudsters make a huge number of phone calls, keeping them up for long durations, and overwhelming the capacity of an organization’s phone network.
TDoS attacks can impair a voice network’s availability, but can also be used as a tool for extortion. TDoS attacks have been in the news recently as a threat to public safety, as fraudsters have taken to using TDoS attacks against hospitals, police stations, and other public services.
If your organization suffers from a TDoS attack, it is important that you save as much information as possible about the attack. Save the voice recording of suspects, phone numbers, start and stop times, number of calls per hour, ANIs, and IP addresses. Retain all call logs and IP logs. After the attack, you can then use the information to file reports with the FBI’s Internet Crime Complaint Center and your local police department.
Vishing
Phishing is a form of fraud that uses email messages with phony addresses, websites or pop-up windows to gather your personal information, which can then be used for identity theft. A form of phishing that uses the telephone instead of email is known as Vishing or “Voice Phishing.”
Vishers pose as a legitimate business to attempt to gather information from someone. That information can then be used for identity theft or other forms of fraud.
Vishing fraud scenario
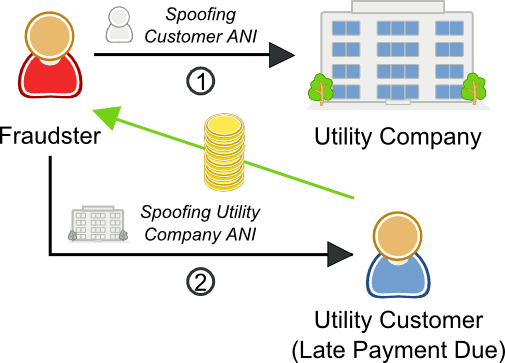
- Fraudster calls the utility company while spoofing the ANI of a customer. The fraudster then navigates the utility’s phone system to gather customer data, especially credit balance.
- Fraudster calls customers who are behind on their payments while spoofing the utility company’s ANI. The fraudster, pretends to work for the utility company, and demands payment over the phone in order to get the customer’s credit card information.
Don’t give out your personal information. Legitimate companies will never call or email you to request information such as passwords, bank account information or credit card numbers unless they’re responding directly to an inquiry you know you have made. To make sure you’re dealing with the real company, you can always contact us them directly. Be cautious about posting personal information on public websites, such as social networking sites. Fraudsters might use those details to gain your trust.
More on TransNexus.com
February 15, 2023
Suggestions to curb access arbitrage
June 27, 2022
FCC proposes new rules to prevent access stimulation
June 6, 2022
Denial of service attack and ransom demand defeated
May 18, 2022
China cracks down on telecom fraud
December 6, 2021
Telecom fraud losses increasing, according to CFCA report
December 1, 2020
FCC Report and Order on one-ring scam calls
November 9, 2020
Domestic telecom toll fraud is still a problem
October 12, 2020
FCC changes rules for intercarrier compensation on toll free calls
January 23, 2020
TRACED Act calls for one-ring scam protection
November 19, 2019
Robocall and TDoS case studies
October 28, 2019
FCC denies stay request on their Access Arbitrage Order
October 28, 2019
Wangiri telecom fraud activity reported in Canada
September 26, 2019
FCC issues order to prevent access stimulation
July 16, 2019
ClearIP adds new call forwarding blacklist capabilities
July 10, 2019
July holiday week telecom fraud attack profiles
June 13, 2019
ClearIP enhancements for blacklisting of SPID and location
May 20, 2019
Anatomy of a telecom fraud attack
May 14, 2019
Study on rule changes to eliminate access arbitrage
May 8, 2019
FCC warns of Wangiri telecom fraud scams
March 8, 2019
SIP Analytics vs. CDR-based fraud management – a case study
October 22, 2018
FCC proposal to curb domestic telecom fraud
September 27, 2018
ClearIP delivers the fastest, easiest, most-precise prevention of toll fraud, robocalls and TDoS attacks. It’s ready-to-go with STIR/SHAKEN.
Learn more